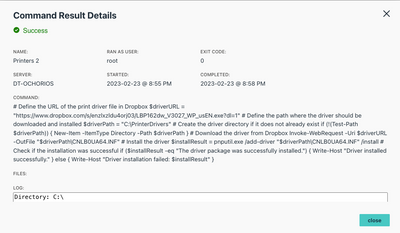
Linux Ubuntu Support - Reset Password.
We identified that in Linux, when the user performs a password reset or the password expires, the user assigned to the computer is no longer visible, making it impossible for the user to log in and change the password.Do you have an explanation why t...