Block Apple ID and Internet Accounts on macOS and iOS devices
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2024 03:46 AM - edited 08-27-2024 02:39 AM
Hola Admin Friends,
I'm back with a guide to explore how to effectively disable Apple ID and Internet Account sign-ins on macOS or iOS, to block end users from signing into their devices.
|
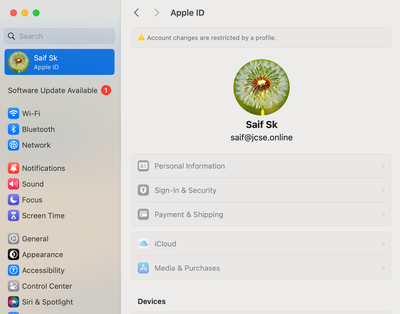
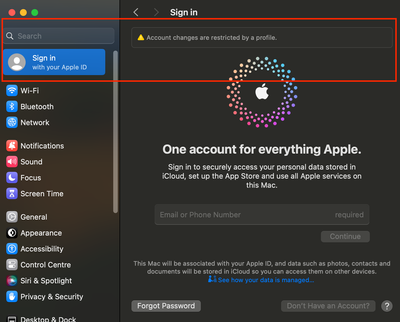
IMPORTANT NOTE - This process will only grey out the Apple ID and Internet Account sign-in options and works well when the user is NOT signed into any of their accounts on the device. If the user is already signed in prior to deploying this profile, then it will keep the account logged in a locked state and NOT log them out.
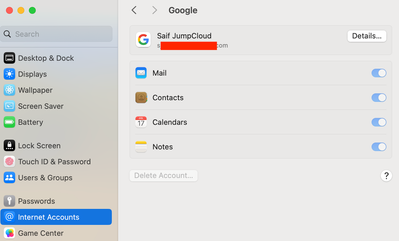
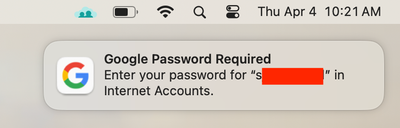
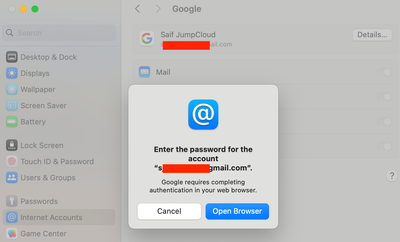
With a locked Apple ID or Internet Account, the device will still receive emails, sync contacts, and calendar events based on the settings configured by the end user. If there has been a password change outside of the device, the system will prompt the end user that a password change has occurred and prompt the user to re-authenticate using the new password. Here's a snapshot of what enduser sees, when they change the password of their Google account outside of the device, which has been locked within device's Internet Accounts -
|
Why?
With the launch of macOS 14 Sonoma, the landscape of Apple MDM has changed to a certain extent including deprecation of a few MDM payloads like SystemPreferences. Devices running macOS 13.X.X and below are able to utilize this payload and block Apple ID by enabling or disabling the System Settings preferences pane via the EnabledPreferencePanes and DisabledPreferencePanes properties, respectively. We offer a preconfigured Mac - System Preferences Control Policy to achieve the same for devices running macOS 13.X.X and below.
However, for macOS 14 and above, iOS 17 and above we can utilize Restrictions MDM payload, which works for both - macOS 10.7+ and iOS/iPadOS 4+. As we do not have a preconfigured MDM policy in the admin console at the moment, we can craft a custom MDM profile using the below payload to meet this requirement.
| NOTE - For iOS devices, device needs to be in a supervised state for the policy to kick in. This policy WILL NOT work on non-supervised iOS devices. |
Using Apple Configurator or iMazing Profile Editor or simple Mac tools like TextEdit or Visual Studio Code, create a custom MDM configuration profile with the below payload, which is in XML format and save the file with .mobileconfig extension:
for macOS -
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadDisplayName</key>
<string>Restrictions</string>
<key>PayloadIdentifier</key>
<string>com.apple.applicationaccess.8C0F15FE-A045-4AE8-916A-4E03BF256140</string>
<key>PayloadType</key>
<string>com.apple.applicationaccess</string>
<key>PayloadUUID</key>
<string>8C0F15FE-A045-4AE8-916A-4E03BF256140</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>allowAccountModification</key>
<false/>
</dict>
</array>
<key>PayloadDisplayName</key>
<string>Disable Apple ID</string>
<key>PayloadDescription</key>
<string>This policy disables modification of Apple ID and Internet Accounts</string>
<key>PayloadIdentifier</key>
<string>com.jumpcloud.blockID</string>
<key>PayloadOrganization</key>
<string>YOUR ORG NAME</string>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>080C90A7-1A97-414F-B994-9EC875BD9F96</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>TargetDeviceType</key>
<integer>5</integer>
</dict>
</plist>
for iOS -
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadDisplayName</key>
<string>Restrictions</string>
<key>PayloadIdentifier</key>
<string>com.apple.applicationaccess.0AC770BB-456B-4651-8D79-189EC9093CB8</string>
<key>PayloadType</key>
<string>com.apple.applicationaccess</string>
<key>PayloadUUID</key>
<string>0AC770BB-456B-4651-8D79-189EC9093CB8</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>allowAccountModification</key>
<false/>
</dict>
</array>
<key>PayloadDisplayName</key>
<string>Block Apple ID</string>
<key>PayloadDescription</key>
<string>This policy blocks modification of Apple ID</string>
<key>PayloadIdentifier</key>
<string>com.jumpcloud.blockIDiOS</string>
<key>PayloadOrganization</key>
<string>YOUR ORG NAME</string>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>49331B64-A9D1-42AC-B236-5E03CCDDB86C</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>TargetDeviceType</key>
<integer>1</integer>
</dict>
</plist>
For both profiles, in lines 23, 25 and 27, you can manually update the profile name, profile description and organization name as per your choice of requirement.
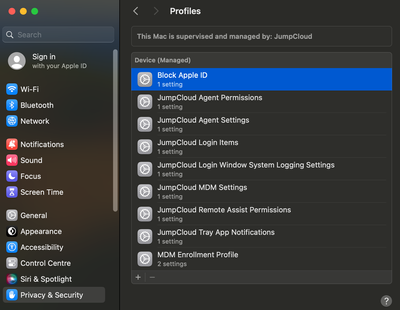
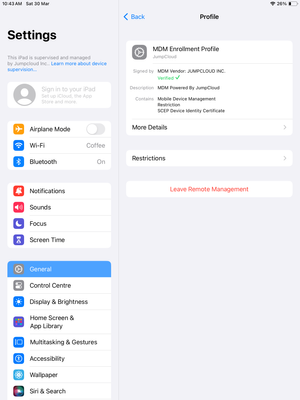
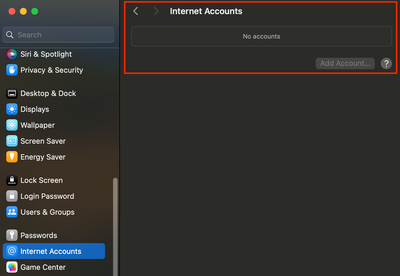
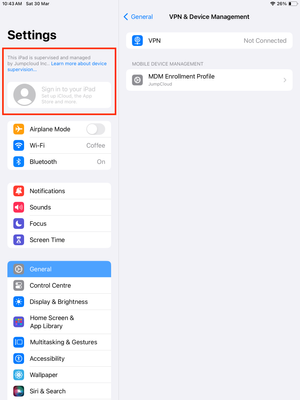
Once the policy is deployed to the endpoint, this payload can be located under System Settings > Privacy & Security > Profiles for macOS and Settings > General > VPN & Device Management > MDM Enrollment Profile > Restrictions for iOS/iPadOS, as shown below:
macOS -
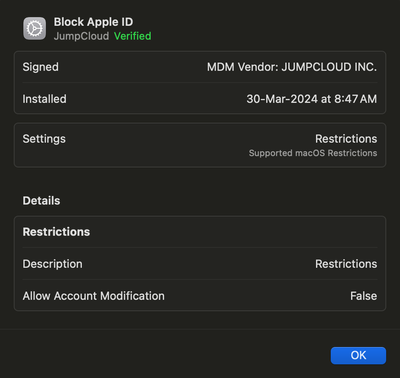
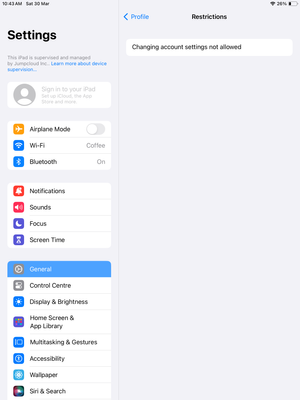
We can now verify that the block policy has been enforced as we are unable to add Apple ID or Internet Accounts on both macOS and iOS/iPadOS.
macOS-
iOS/iPadOS -
Hope this was helpful in blocking Apple ID sign-ins in a seamless way! Until next time 😄
- Labels:
-
Mac
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2024 10:57 AM
@saifshaik we've got someone asking about this over on iPadOS\iOS AppleID Block -- think you can help?
Like someone's post? Give them a kudo!
Did someone's answer help you? Please mark it as a solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2024 12:52 AM
Sure Becky! Let me test this out as we had another customer the other day stating that this didn't work on their iPad when tested. Will test and get back to the customer shortly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2024 08:54 AM
This is not working, I test it out in my iOS device and nothing 😕
Can you help me?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2024 11:04 PM
@Itamar This policy works only on supervised iOS devices. Ensure the iOS device where you're trying to assign the policy is a 'supervised' one. iOS devices in JumpCloud are 'supervised' when they're enrolled via Automated Device Enrollment. Hope this helps!