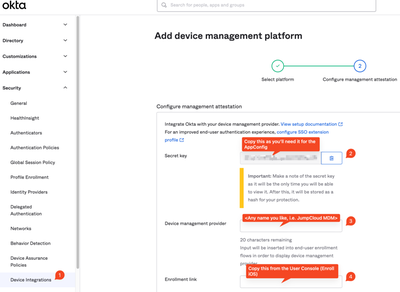
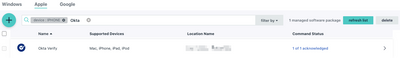
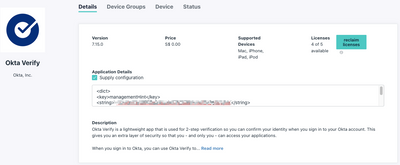
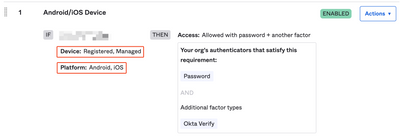
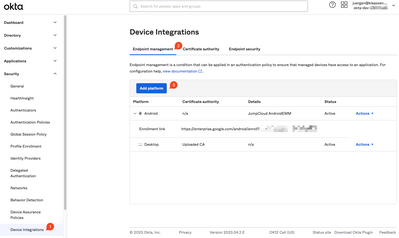
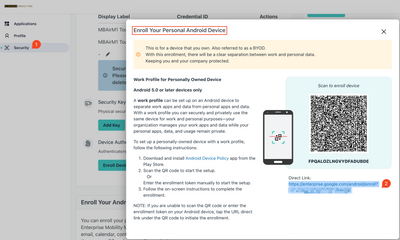
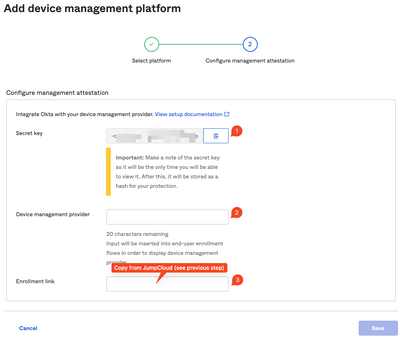
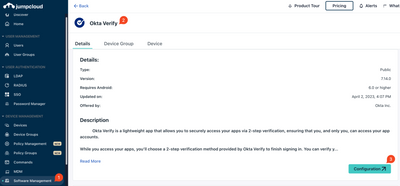
AI Security Crisis: Hidden Threats IT Must Stop Now
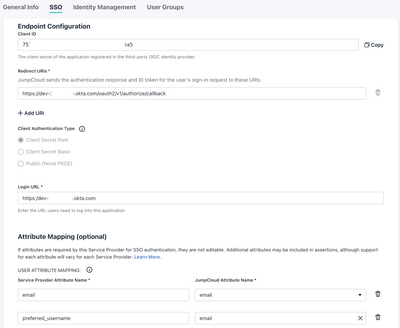
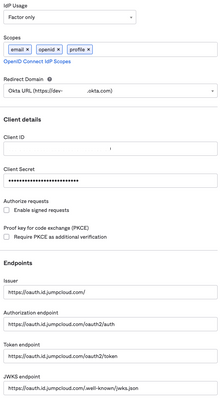
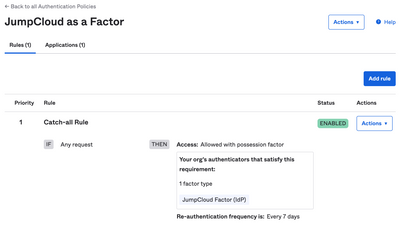
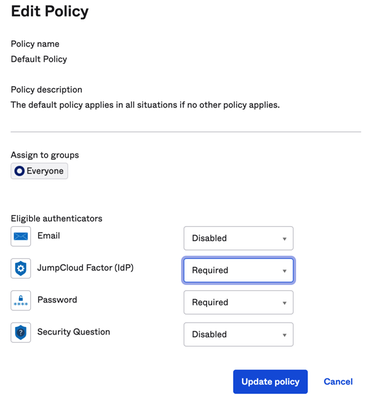
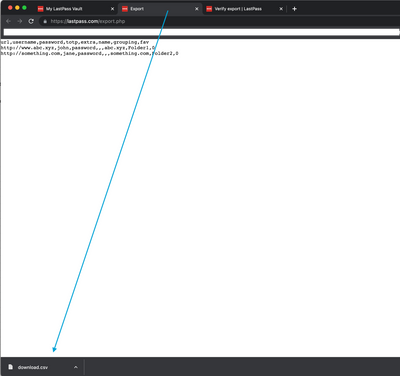
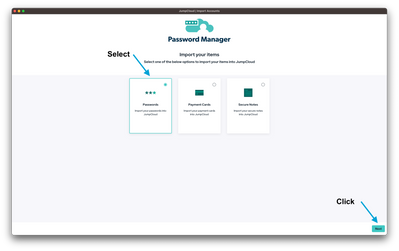
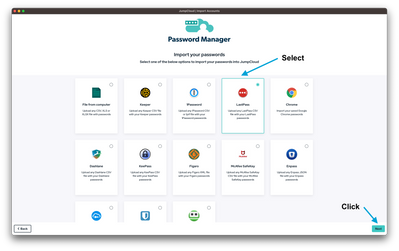
AI here, AI there, AI everywhere! AI is transforming technology, making systems smarter and automating tasks. But this progress comes with new risks. IT professionals, beware… Hackers are now using AI to supercharge their attacks, making security t...