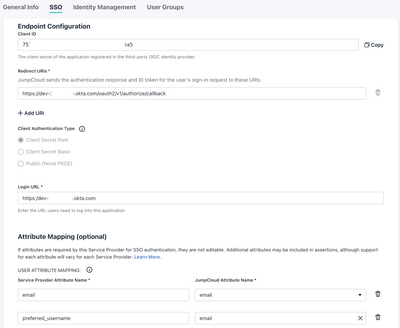
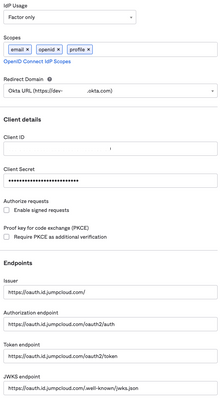
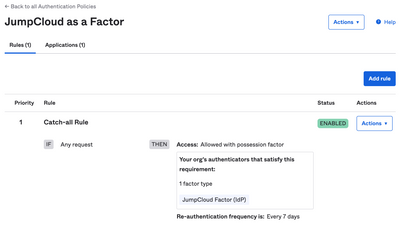
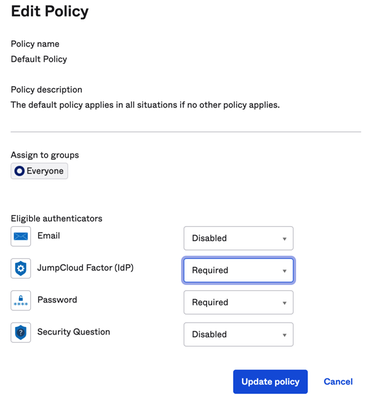
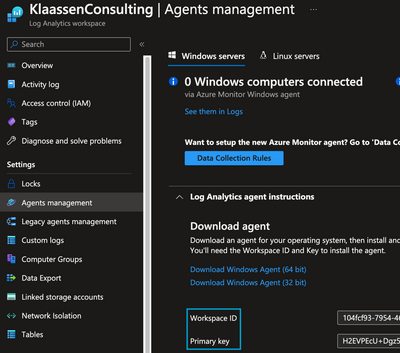
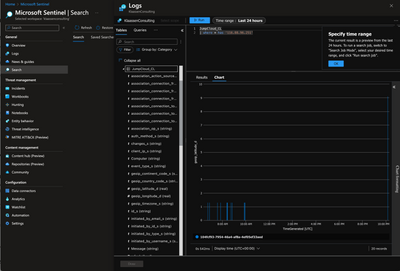
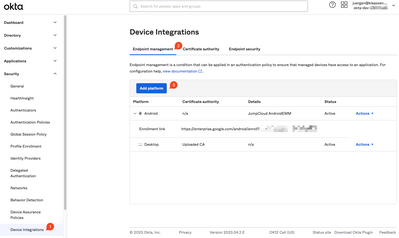
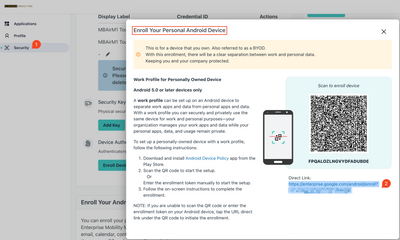
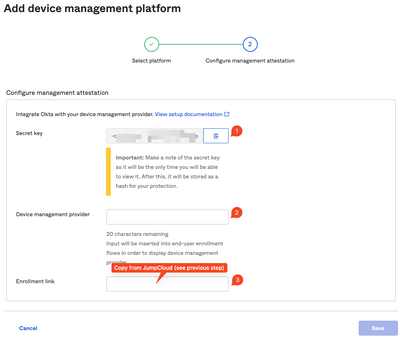
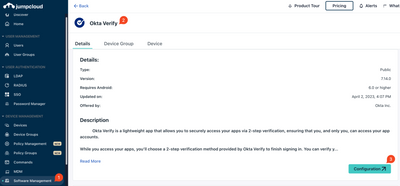
Resolved! Need help with my project on wordpress
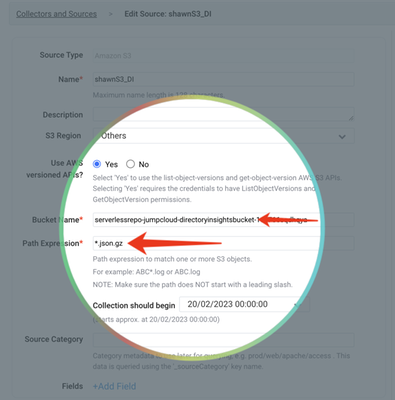
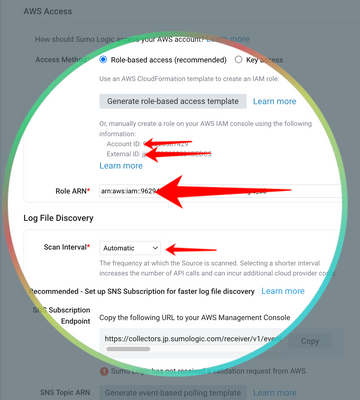
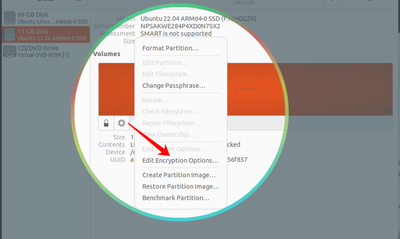
I am a student and I was working on my infertility project on WordPress. My Ubuntu showed a pending software update and I updated my laptop. However, after that update, my WordPress project won’t even open. My project is due next week, and I have to ...