- JumpCloud Community
- IT Topics
- Security & Networks
- How to establish Device Trust (managed devices) fo...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to establish Device Trust (managed devices) for Okta by using JumpCloud as factor for authentication?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2023 02:33 AM - edited 02-22-2023 05:19 PM
Hello
Sharing a documentation here to configure JumpCloud and Okta in tandem to use JumpCloud as factor for Device Trust by using OIDC, Conditional Access Policies and Okta's Policy Engine.
What it does:
If you're using Okta for SSO (let's say via SAML to your Salesforce instance) you have ample of options to add additional layers for enhanced security by having MFA enabled, iincluding FIDO2 (WebAuthn).
What you don't have that straight forward with Okta is Device Trust. So if you want to make sure that only managed devices (Windows, macOS, Linux) have access to i.e. Salesforce, you have to rely on third-parties here.
By default, Okta integrates with EMM solutions, Certification Authorities and Endpoint Security solutions to establish these additional layers. For example, if your having a CA with a SCEP service, you could integrate this way by pushing out certificates to your devices with the caveat that you also have to configure the SSO extension profile.
What if you're using JumpCloud and Okta and you want to use JumpCloud's super-easy-to-deploy Device Trust Certificates instead?
Well, got it figured out. The entry point here is the capability of Okta to integrate with other IDP's as a factor.
Ingredients used:
- JumpCloud Custom OIDC App
- JumpCloud Conditional Policy
- JumpCloud Device Certificates
- Okta Identity Provider integration
- Okta Authentication Policies
Requirements:
- Okta tenant with respective licensing in place
- JumpCloud tenant with respective licensing in place
- Device Certificates already enabled and deployed
Caveats:
Right now, the check on the Device Trust Certificate requires an actual login to JumpCloud. This leads to a 'double authentication' every time it's required. In practice, there might be no need to check on the Device Trust Certificate on every login. In my configuration I only enforced it once a week - while unmanaged devices are denied completely.
How to:
1. Configure a Custom OIDC App
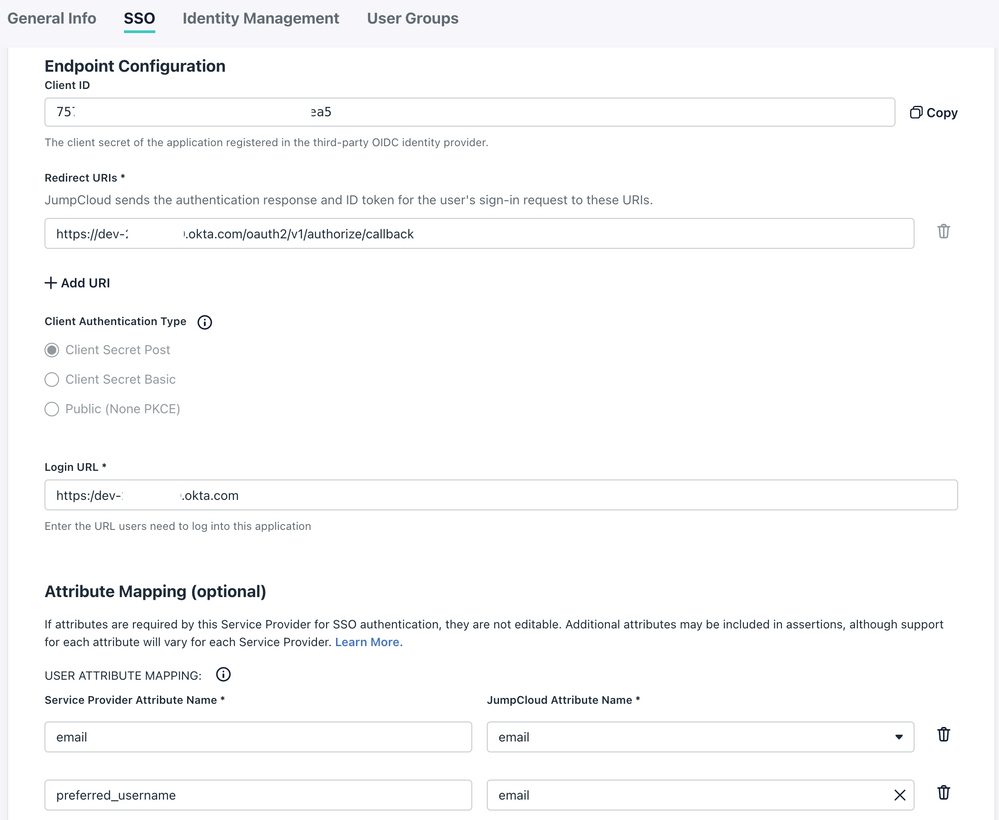
On JumpCloud you will need to populate the following settings:
Redirect URIs: https://dev-xxxx.okta.com/oauth2/v1/authorize/callback
Login URL: https:/dev-xxxxx.okta.com
Attribute Mappings (Okta requires preferred_username here as well):
| Service Provider Attribute Name | JumpCloud Attribute Name |
| preferred_username |
On Okta:
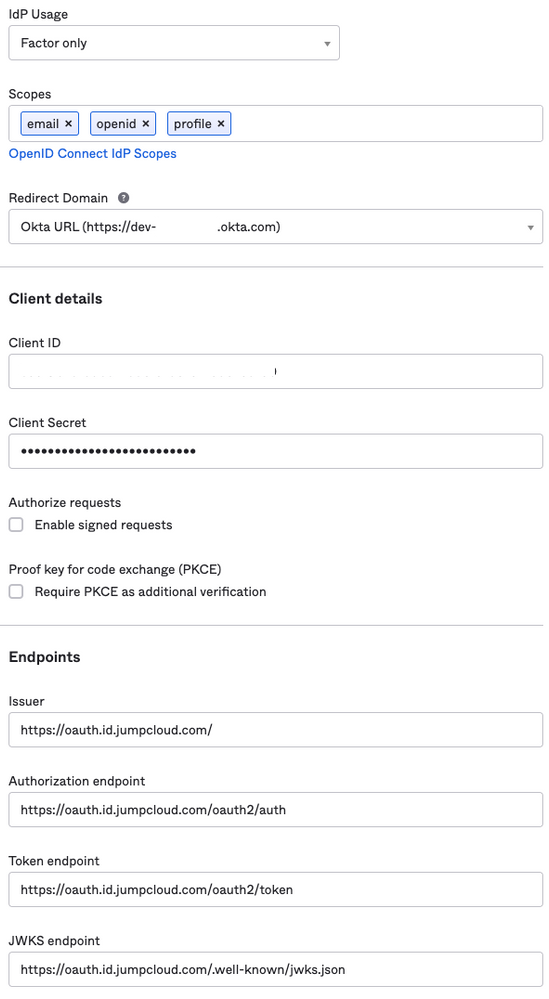
Go to Security / Authenticators and click "Add authenticator"
I named it 'JumpCloud Factor' and follow the instructions outlined here in this article.
Use the following settings (according to your own tenant):
Redirect Domain: Your tenant-URL
Client ID and Client Secret from the JumpCloud Configuration
Issuer: https://oauth.id.jumpcloud.com/
Authorization endpoint: https://oauth.id.jumpcloud.com/oauth2/auth
Token endpoint: https://oauth.id.jumpcloud.com/oauth2/token
JWKS endpoint: https://oauth.id.jumpcloud.com/.well-known/jwks.json
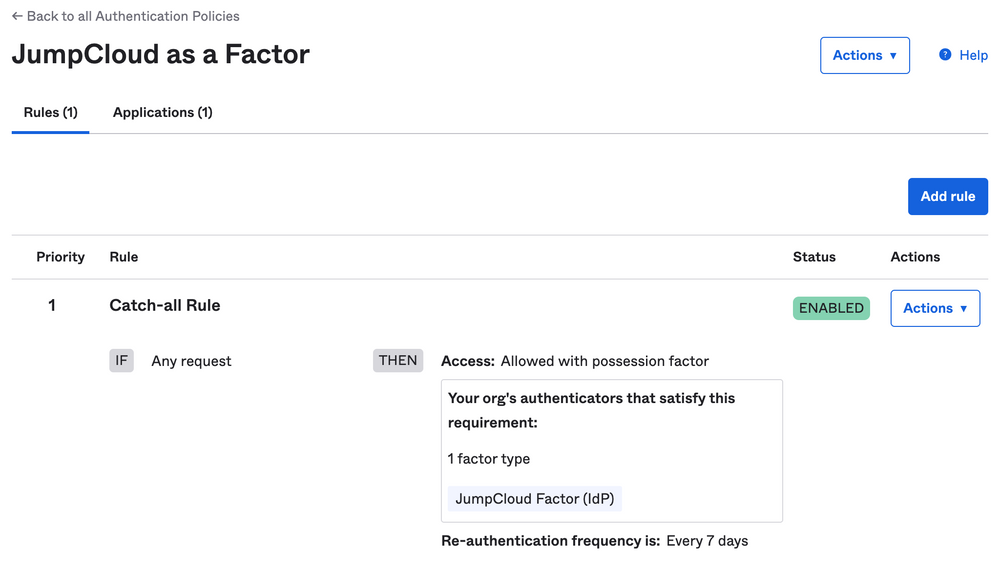
Remaining on Okta, you will have to add an Authentication policy recognising this factor (JumpCloud's OIDC App):
For testing purposes I assigned this policy only to one test application without any deeper configurations. As you can see in the screenshot: Every 7 days the factor will be re-enforced which leads to the 'double auth' including JumpCloud.
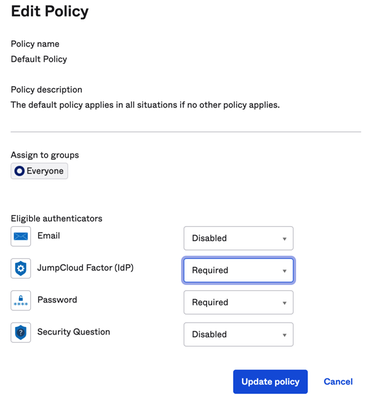
Still on Okta, go to Authenticators and require the Enrollment for "JumpCloud Factor":
Now we switch back to JumpCloud to configure Conditional Access Policies.
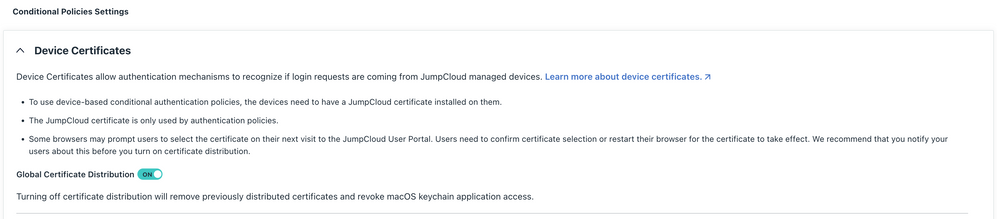
First, make sure that you have enabled Device Certificates. Go to Conditional Policies / Settings and check that "Global Certificate Distribution" is toggled to "ON"
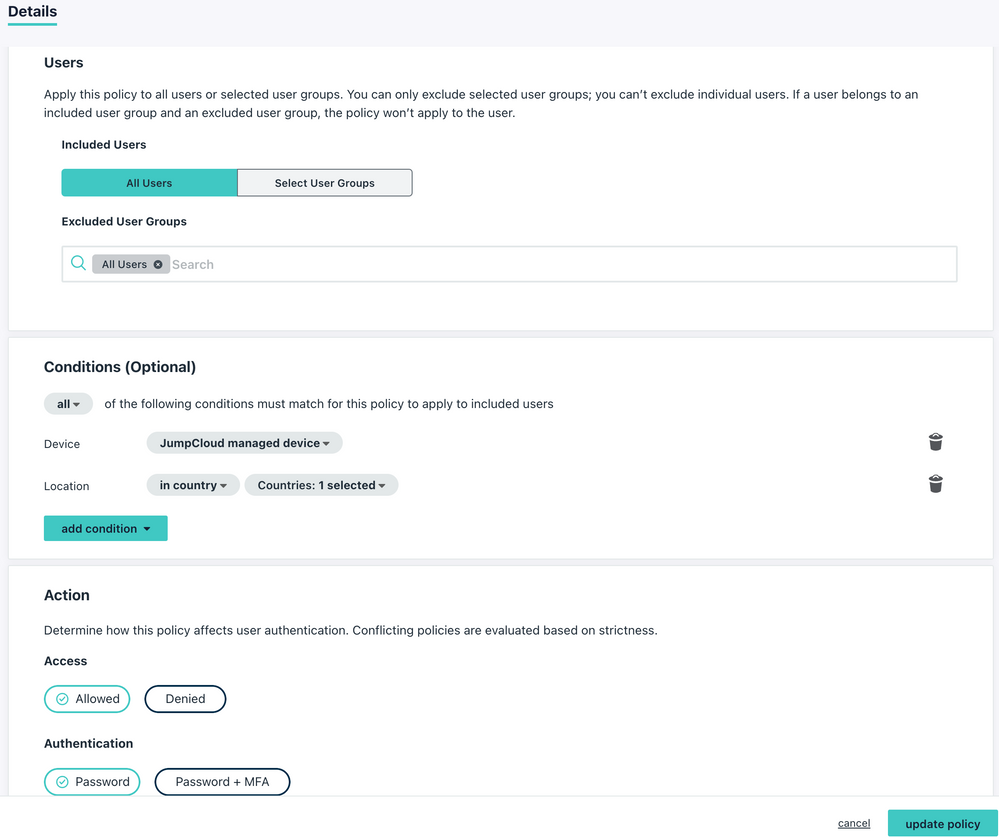
Next, let's configure the Conditional Policy.
I named it "JumpCloud as a Factor for Okta" and you select the OIDC app "JumpCloud Factor", i included "All Users" and as Conditions i did configure
| Device | JumpCloud managed device |
| Location | in country: Singapore |
Action = Allowed
Authentication = Password
That's it, now let's do some testing for validation.
1. JumpCloud Managed Device
2. Unmanaged Device
That's the basic configuration.
You can enhance the posturing and conditioning here by adding factors like Disk Encryption or IP Address, on Okta itself you can also tweak the Authentication Policy if needed.
Thanks again for reading.
- Juergen
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2023 02:43 AM
Cool solution @JuergenKlaassen !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2023 03:21 AM
Very cool! @JuergenKlaassen
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2023 03:21 PM
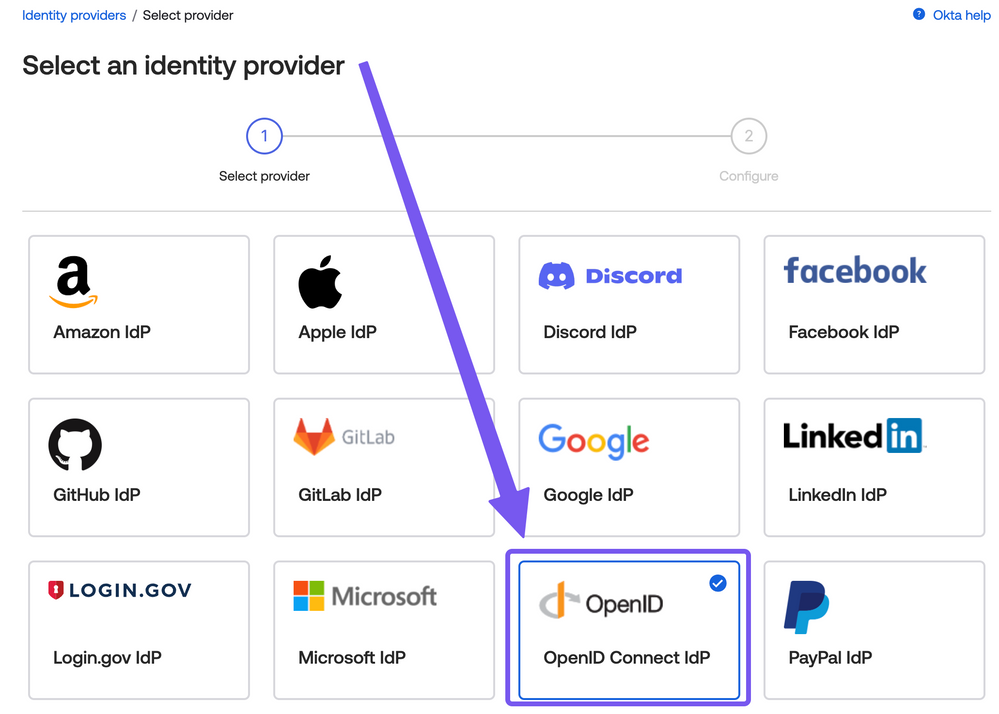
It appears that some of these instructions have changed on the Okta side. Okta now requires an "Identity Provider" to be setup before the "Authenticator" can be established. These appear to be the same step in the instructions above. When attempting to setup the Identity Provider, OIDC is not an option (at least for me) in Okta. Would love to connect directly on this as what you've outlined is exactly what I am trying to accomplish with JumpCloud and Okta.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2023 05:13 PM
@JuergenKlaassen tagging so you can take a look
Like someone's post? Give them a kudo!
Did someone's answer help you? Please mark it as a solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2023 06:29 PM
Hi Timothy
I just checked and at a first glance, I don't see any significant changes on the Okta UI.
Having JC setup as an IdP in Okta is definitely required to make this work.
You don't have this option in your Okta Console?
I'm not sure atm which type license this would require for Okta (I'm using a dev-tenant).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2023 12:09 PM
Thanks for the reply! I do not have the OpenID option, but I have all of the others. I will inquire with Okta as to what is needed to get that option. I am wondering if a dev account is required to see that option. I do have a SAML 2.0 option, which I do not see in your screenshot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2023 02:46 PM
@JuergenKlaassen Progress! Okta needed to enable the OIDC Identity Provider within their system, so I was able to complete the configuration now. If you're not seeing it, reach out to Okta to enable it.
I am still dealing with an issue where I cannot force the JumpCloud IdP Factor to be required for authentication because it is seen as a similar "possession" factor as Okta Verify, so the system allows the user to use EITHER of those two factors and get around the JumpCloud authentication requirement. I'm working with Okta support on that and will report back.
Second, I am also finding that JumpCloud is allowing authentication of the SSO application even from non-managed devices. Configuration all checks out and the JumpCloud certificates have been deployed, but JC allows a user to authenticate with their JC credentials and MFA using that factor on any device still. I'm still trying to sort that one out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2023 04:43 AM
Hey Timothy
Sorry for my delayed response.
Did you figure it out with the possession factor?
Maybe you can share more details/screenshots about your policies there?
On the second, do you have configured your Conditional Access Policies accordingly on JumpCloud?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2023 11:33 AM
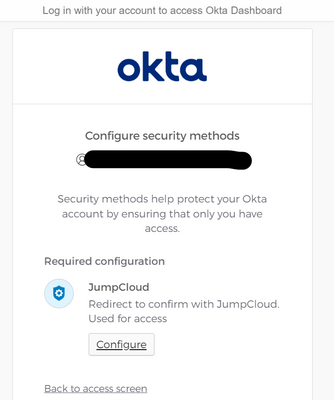
Hello, I believe I have it set up correctly, but when trying to access the Okta Dashboard it redirects me to Jumpcloud in an attempt to sign up
When I click on "Configure" I am redirected to my jumpcloud tenant, after logging in, I am directed to the jumpcloud applications screen
and when I return to my okta dashboard, I am redirected to the first screen I mentioned and it stays on repeat
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2023 04:05 AM
Hey
The 'Configure' and being redirected is expected as Okta uses JC as a factor here. But once completed, you shall not end up in a look or so.
Does your Conditional Policy with Device Trust works as expected with JC (standalone without Okta in the chain)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2023 08:27 AM
Hello, yes I've set up my Conditional Policy in JC, and it's working fine. I can only access it if I have the Jumpcloud Agent.
After clicking on 'configure,' and "enroll" I am redirected to the JC website
I end up in this infinite loop.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2023 10:50 AM
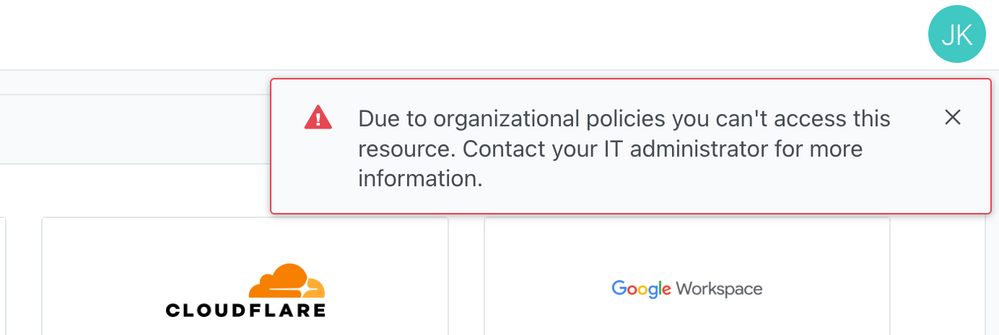
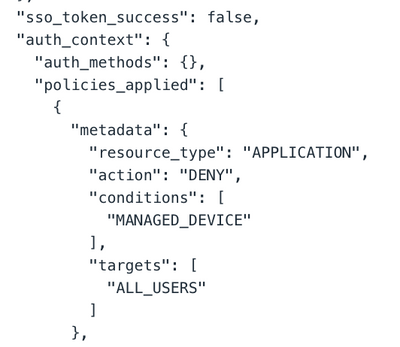
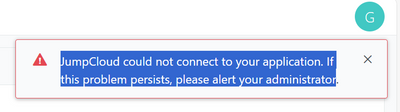
I believe it might be something related to the redirect url. in the okta logs, im not receiving anything from jumpcloud
and after logging to JC, im encountering this erro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2024 10:50 AM
Hey,
What is the Jumpcloud license required for this to work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2024 09:58 PM
Hi @shalomcarmel
That would require Platform Prime as it's relying on Conditional Access.
New to the site? Take a look at these additional resources:
Ready to join us? You can register here.
- Enabling 801.X Auth for Ethernet on Windows via XML and Powershell in Security & Networks
- Lots of O365 Login Prompts in Software & Hardware
- Using JumpCloud & Duo for MFA on User Portal, SSO applications, and device logins in Software & Hardware
- Tailscale SSO OIDC in Security & Networks
- IT Onboarding Handbook in Best Practices