How to configure JumpCloud SSO for Cisco Meraki MX and Cisco AnyConnect (Cisco Secure Client) for VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2023 11:42 PM - edited 09-23-2024 04:34 PM
Hello
Earlier this months Cisco Meraki released SAML Authentication for Cisco Secure Clients (formerly known as Cisco AnyConnect). You can find the respective documentation here and until now you need to ask Meraki's support to enable the feature for you (just raise a simple ticket to them).
Notable is that you need a firmware version on your MX which is 16.3+ or 17.5+. In my case I configured this with the beta version 18.105.
On JumpCloud I used a "Custom SAML App"-Connector to get it configured.
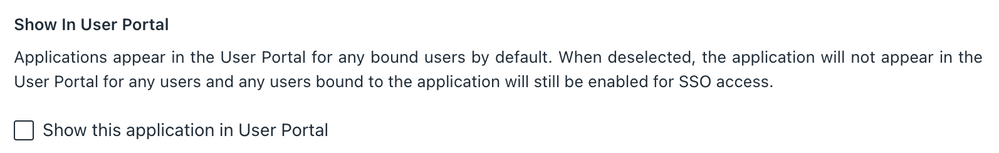
As mentioned in Meraki's KB, the config naturally only supports SP-Initiated logins and therefore I uncheck the box to show the application in the User Portal:
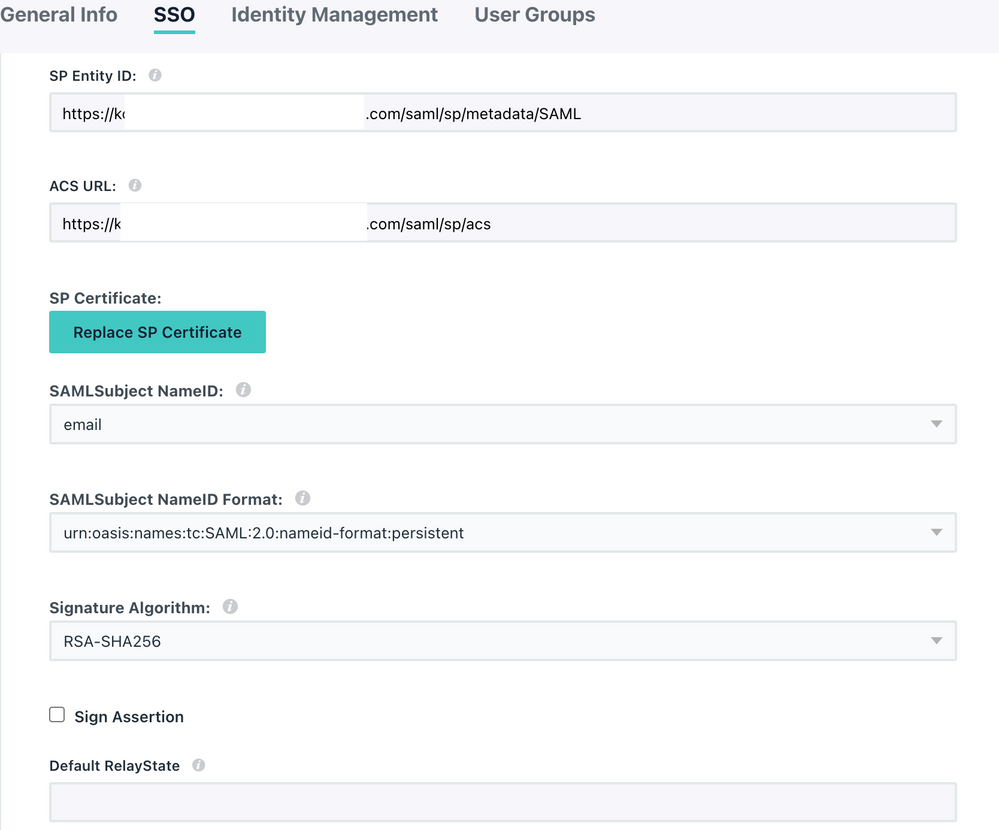
Following the KB's to set up SAML on the IDP side of things you end up with the following entries for JumpCloud while configuring the Connector:
SP Entity ID (case sensitive) https://<YOUR_FQDN_HERE>/saml/sp/metadata/SAML
ACS URL: https://<YOUR_FQDN_HERE>/saml/sp/acs
Login URL: same as ACS URL
SAML Subject NameID Format: SAML 2.0 NameID Persistent
Declare Redirect Endpoint: checked (enabled)
Lastly assign your User Groups to be entitled for using this VPN-Connection.
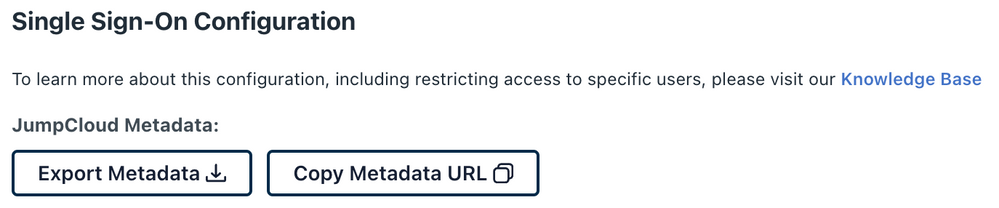
Now you can grab the JumpCloud Metadata-File and upload it to the Meraki Admin Dashboard.
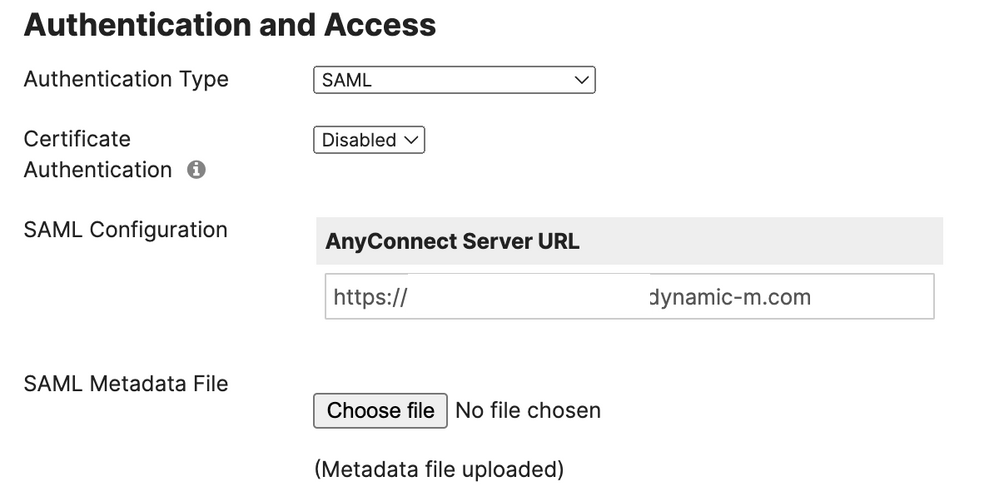
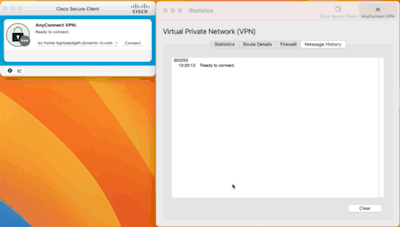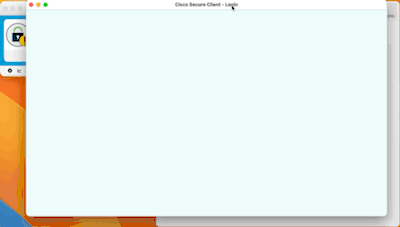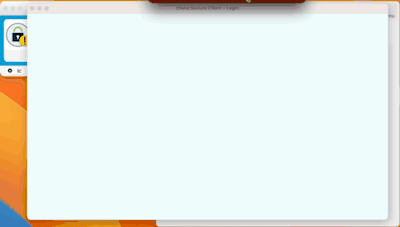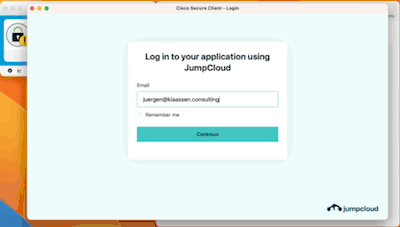
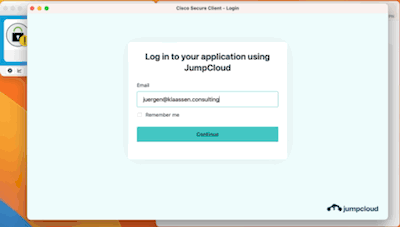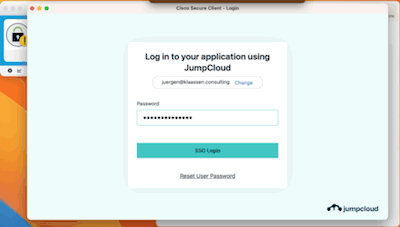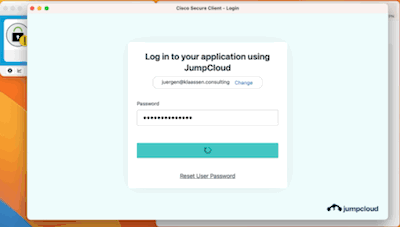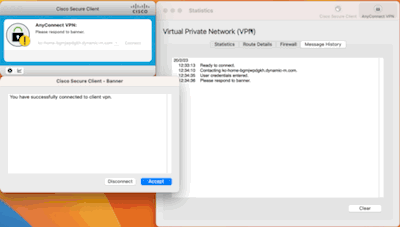
Once done and saved, you're actually ready to fire up your Cisco Secure Client:
If you need guidance on how to deploy and configure the Cisco Secure Client (AnyConnect), please check out one of my previous posts: Deploy and manage Cisco AnyConnect clients on macOS
Note at the end: I haven't tested this with an Conditional Access Policy applied to this connector yet
Thanks for reading as always.
Cheers
-Juergen
- Labels:
-
General Networking
-
Wireless
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2023 11:40 PM
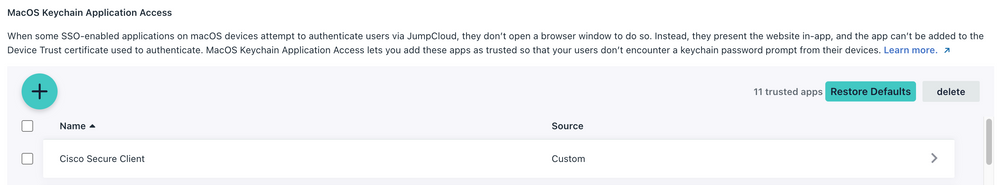
Update: Tested Conditional Access Policies here as well.
Ideally you add the Cisco Secure Client to the Trusted Applications under Settings:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2024 12:17 PM
Hi Juergen,
I tried setup in Jumpcloud and Meraki Firewall with your suggested settings, the AnyConnect could launch a Jumpcloud login page, but error message "Bad Request" prompted after inputted user name and password. When I click the on "Bad Request", it redirected me to Jumpcloud user portal page. Do you help any idea about it? Thank you in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2024 05:02 AM
Hi @rk_2024
Is this persistent and did you reach out to JumpCloud's support for this? Do you experience this on Windows or macOS?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2024 06:24 AM
Hi Juergen,
Thank you for your advice.
This is a persistent issue. I just tried it on Windows devices.
I will seek help from JumpCloud's support.