- JumpCloud Community
- JumpCloud
- Product News
- Addressing CVE-2022-32893 and CVE-2022-32894 macOS...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Addressing CVE-2022-32893 and CVE-2022-32894 macOS Vulnerabilities with JumpCloud
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2022
05:11 PM
- last edited on
08-22-2022
05:51 PM
by
![]() BScott
BScott
![]()
Apple has released software patch updates for MacOS and iPhone / iPadOS that address recent security vulnerabilities. For JumpCloud customers, JumpCloud Patch Management is the best way to be sure that your macOS fleet has been updated. End users with affected mobile devices should observe the Apple-provided update mechanisms.
The affected Apple devices are:
- Macs running on macOS Monterey, prior to version 12.5.1
- iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation), on OS versions prior to version 15.6.1.
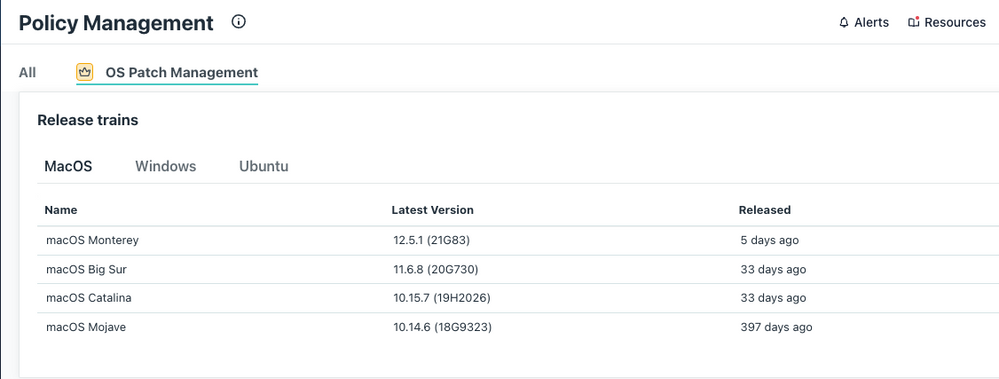
Below you will find information on the CVEs, OS versions impacted and step-by-step instructions for how to patch your Mac devices with JumpCloud Patch Management.
- CVE-2022-32893, which documents out-of-bounds write issue in WebKit, Apple’s browser engine that powers its Safari web browser and all iOS web browsers
- CVE-2022-32894, which documents out-of-bounds write issues in the operating systems’ kernel that can be exploited by a malicious application to execute arbitrary code with kernel privileges.
Enabling macOS Patch Updates Through JumpCloud
The Patch Management features live under the Policy Management section in the JumpCloud Admin Console. To create the Automatic MacOS Updates policy:
1) Log in to the JumpCloud Admin Portal
2) Go to DEVICE MANAGEMENT > Policy Management.
3) Select OS Patch Management. Only OS patch policies appear in this tab.
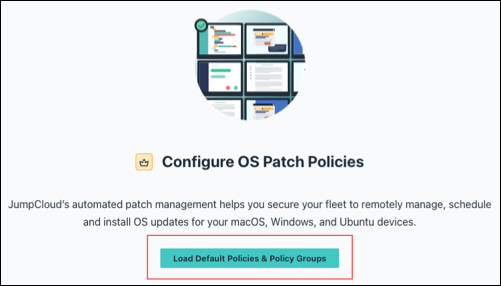
4) If this is the first time you’ve accessed the OS Patch Management tab, click Load Default Policies & Policy Groups. To add the automatic MacOS Updates Policy, click ( + ), then choose macOS. You will see that 4 ring policies are created.
Configuring macOS Patch Updates
After loading the Default Policies you will see 4 ring policies, each with update defaults. For instructions, see Creating Default Patch Policies & Policy Groups on the JumpCloud support site.
- Vanguard - Deploy automated upgrades inside your IT Department.
- Early Adoption - Deploy automated upgrades to early adopters outside of IT.
- General Adoption - Deploy automated upgrades to general users in your company.
- Late Adoption - Deploy automated upgrades to remaining users in your company.
It’s important that your macOS device fleet is placed in the correct ring that maps to your internal policies (as they have different deferral defaults). Depending on your risk appetite, you can be more aggressive on the updates and adjust the deferrals within the thresholds called out in the support docs, for example going from a 7 day deferral to 3 days in a given ring policy.
You can also check out this video tutorial that covers the entire Patch Management configuration process within JumpCloud, including an overview of the default policies and how to adjust them.
How macOS Patches Are Applied
The update notifications to end users from JumpCloud begin once the device detects that it has an update available. Every 5 hours – twice per average working day – the alert window will launch and prompt the user to update their operating system.
When less than 72 hours remain in the grace period, the alert will increase in frequency from twice per working day to 6 times per working day, every 100 minutes. When less than 24 hours remain in the grace period, the alert will increase in frequency again from every 100 minutes to every 10 minutes.
When the grace period has elapsed, and the system is still not updated, the alerts will continue every 10 minutes, but the window can no longer be closed, will re-center on the screen every 10 minutes, and you cannot quit the app from the UI. If the user discovers the process and terminates it through the command line, it will regenerate.
Viewing Fleet Update Status
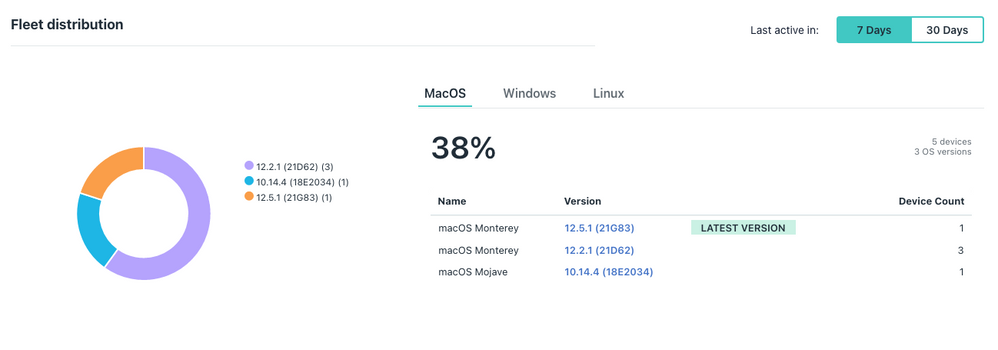
In the JumpCloud Admin Console on the Devices tab you are able to see a Fleet Overview where the current OS version status of macOS devices. As devices check in and the notifications trigger OS patch version upgrade, the device counts will shift to the target OS version (example below).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2022 05:52 PM
Just hit the play button to watch the attached video tutorial, btw.
Like someone's post? Give them a kudo!
Did someone's answer help you? Please mark it as a solution.
New to the site? Take a look at these additional resources:
Ready to join us? You can register here.
- Update a Device via Patch Management in Demo Walkthroughs
- New Features - JumpCloud Password Manager in JumpCloud Product News
- Introducing Zero-Touch Enforced OS Minor Updates and Major Upgrades for macOS in JumpCloud Product News
- JumpCloud Security Update: Okta, LastPass and CircleCI breaches in JumpCloud Product News
- New Report Alert - Browser Patch Management Policy Status in JumpCloud Product News