- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Adversaries are exploiting unpatched zero-day security vulnerabilities more rapidly than ever, and it’s not just operating systems that are vulnerable. Browsers are a high-return exploit. It’s become more important than ever to patch everything as quickly as possible. You wouldn’t want an exploited device being used to bypass all of the security you’ve set up to protect resources.
Demo Overview
JumpCloud’s automated patch management helps you keep your macOS, Windows, and Linux devices secure and updated with automated OS and Chrome browser patching. It’s integrated with the platform, so there’s fewer vendors to manage and a unified IT management experience. We'll set up some basic policies to get your started.
Prerequisites
Not every step here is necessary to complete this tutorial, but you’ll be doing these things anyway if you want to experience your trial as if you’re implementing the product.
- To complete this tutorial, we recommend that you have completed the following walkthroughs (or have set up your instance with the appropriate assets on your own):
- Create admin users
- Creating Users 101
- Creating Groups 101
- Adding Devices 101
Demo Walkthrough
We’ll be using the Admin Console’s Devices Overview tab to analyze your JumpCloud-managed devices and review the most current releases from Microsoft, Apple, and Canonical. You can manage when major OS upgrades and minor updates are available and applied to your devices with an IT Admin with Manager role or higher. Configuring a required installation window lets users choose the most convenient time to perform an OS update. This walkthrough will focus on Windows as an example and demonstrate how to centrally manage Chrome browser updates.
Are you a visual learner? Watch this video tutorial.
Step 1: Create a Default Windows Patch Policy
- Log in to the JumpCloud Admin Portal.
- Go to Device Management > Policy Management.
- Select Patch Management, then select the OS tab.
- If you haven’t yet configured a patch policy or patch policy group, click Load Default Policies & Policy Groups to create four out-of-the-box default policy groups. Each policy group contains three pre-configured deployment ring policies that are automatically bound to the group.
- Review the preconfigured settings for the Windows default policies, but do not change this for purposes of this exercise.
- The Windows OS Patch Management policy modifies the Windows Updates for Business group policy settings on devices and allows administrators to keep Windows devices up to date with the latest security patches available to devices.
- Review the Deferral and Deadline Settings and the Update Enforcement & Restart Settings in the Admin Portal for the four default Windows OS Patch Management policies. Select Windows Vanguard for the lowest permitted deferral for updates.
Resources:
Get Started with Patch Management
Step 2: Create a Policy Group
- Review your default policy groups and policies. The policies are automatically assigned to the appropriate group. It will apply to all Window testing endpoints.
- Select the Devices tab. Select one or more devices where you’ll apply this policy. Click save.
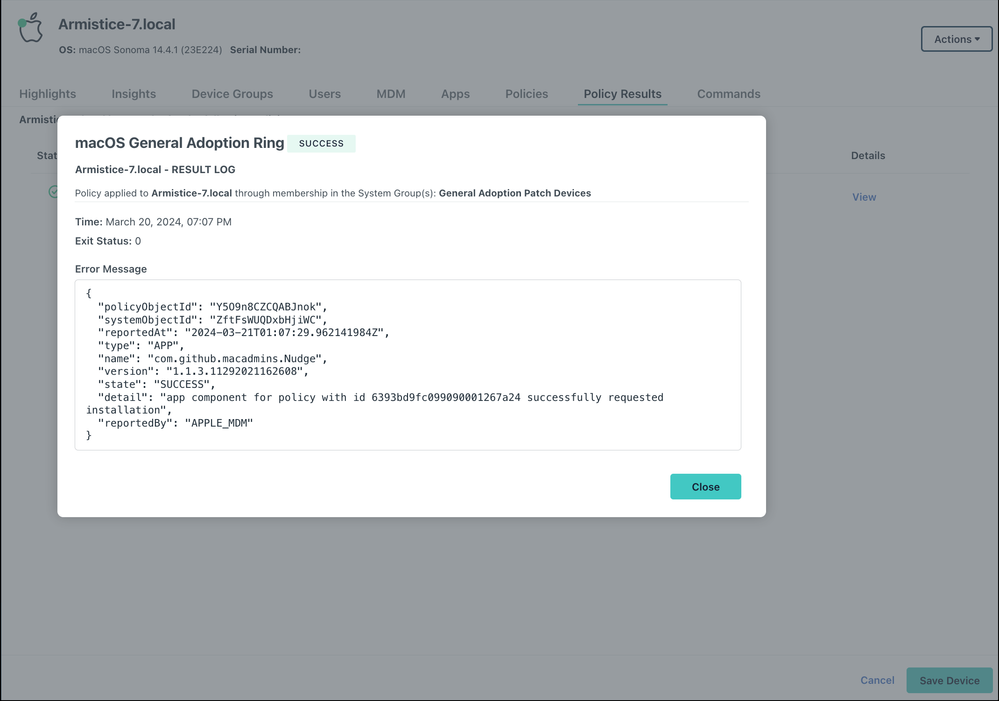
- After the policy runs, you can view detailed results for a specific device:
- Go to Device Management > Devices.
- Select the Devices tab, then select the device.
- Select Policy Results, then click view to see more details. An Exit Code of 0 means the policy ran successfully.
- To delete a patch policy, select the checkbox next to the policy and click delete. The policy is removed from the OS Patch Management list.
To force the policy to take effect as soon as possible, you can manually run a Group Policy Update on the device and wait at least 60 seconds for the JumpCloud Agent to download the policy updates to the local devices. Open the Windows Command Prompt as an admin on the local device and run the gpupdate /force command. Restart.
Resources:
View OS System Updates in Directory Insights
Step 3: Creating Default Chrome Browser Patch Policies
Browser updates can be as vital as OS Updates.
To create default universal browser patch policies:
- Log in to the JumpCloud Admin Portal.
- Go to Device Management > Policy Management.
- Select Patch Management, then select the Browser tab.
- If you haven’t yet configured a Google Chrome browser patch policy, click Load Default Policies to and select “Chrome Day Zero Ring’ from one of the preconfigured universal default Chrome policies. That will provide a one-day grace period for updates.
Enter a new name for the policy or keep the default. Policy names must be unique.
Review the fields under Automatic Update Settings and the default settings for each browser patch policy. You can adjust them as needed at a later time. Click Save.
- Configure the fields under Sign-in Settings as you determine. You may bypass “Restrict sign-in to regular expression pattern”, but may configure it per the knowledge base article linked below. Sign-in Settings and Chrome Browser Cloud Management Settings are organization-specific and do not contain preconfigured settings.
- (Optional) If you are new to Google and need a Google Admin Console login to configure Chrome Browser Cloud Management Settings, you can sign up for Chrome Browser Cloud Management at no additional cost. See Chrome Browser Cloud Management documentation. It provides more granular control to enforce additional browser policies, view and enforce managed browser extensions, and view detailed reports on managed browsers
- Select the policy you just created and select Device Groups. Select one or more device groups where you’ll apply this policy. For device groups with multiple OS member types, the policy is applied only to the supported OS.
- (Optional) Select Devices, then select one or more devices where you’ll apply this policy.
- (Optional) Select Policy Groups, then select one or more policy groups for this policy. Click save. The configured policy appears in the Browser tab under the Patch Management tab.
After applying the policy, the user must relaunch Chrome on the device for the changes to take effect. After the policy runs, you can view detailed results for a specific device:
- Go to Device Management > Devices.
- Select the Devices tab, then select the device.
- Select Policy Results, then click view to see more details. An Exit Code of 0 means the policy ran successfully. Click ok.
Resources:
Create a Universal Patch Policy
Bonus Simulations
Conditional Access Device Trust (Simulation)
Final Results
That’s it… you’ve just configured patch management. Patching reduces attack surface area by eliminating exploits that threat actors may be using in their attacks. Don’t fret if there’s no patch available: JumpCloud commands can be used to rapidly implement remediations.
Endpoint posture is an important aspect of asset-based security, and is integral to an identity and access management strategy. Only managed devices should be accessing your most privileged resources. You’ve taken a big step in that direction. Consider using device trust as a basis for Conditional Access policies to secure access after you’ve configured standard policies.
Get prepped now
Managed devices can be configured to utilize JumpCloud Go™, a passwordless credential that’s phishing resistant, as an authentication factor. Read the whitepaper to learn more.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.