JumpCloud Go™, hardware-protected and phishing-resistant passwordless login, is here!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2023
04:23 PM
- last edited on
09-12-2023
04:57 PM
by
![]() BScott
BScott
![]()
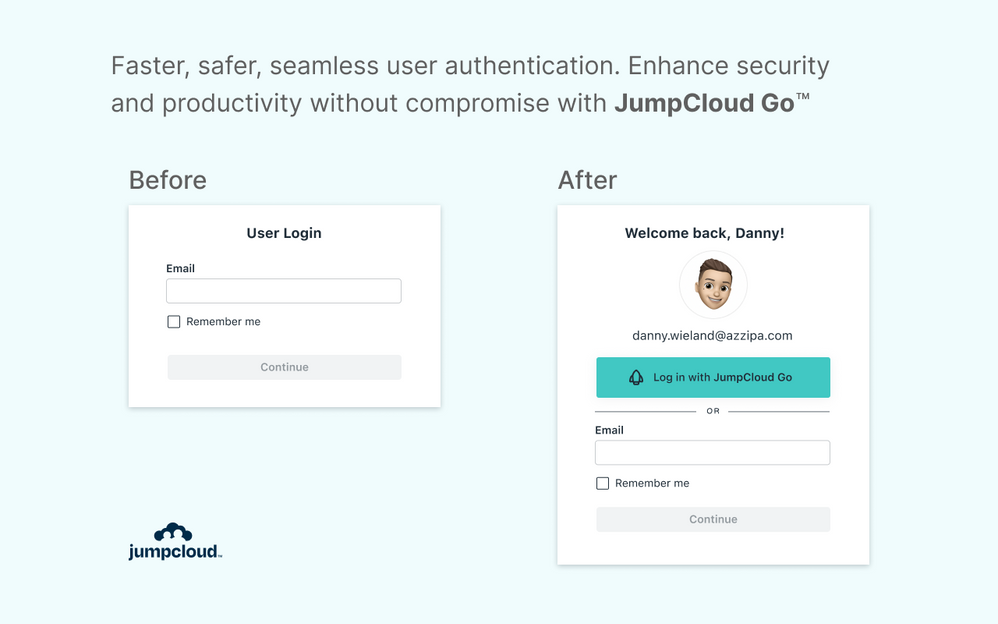
What is JumpCloud Go™?
JumpCloud Go™ is a hardware-protected and phishing-resistant passwordless login method that allows users seamless access to JumpCloud-protected web resources from managed devices. JumpCloud Go is supported on MacOS and Windows and integrates with device biometric authenticators (Apple Touch ID or Windows Hello) to satisfy traditional password sign-in challenges. Users experience minimal interruptions with JumpCloud Go, and are prompted for input only when required. This simpler and more secure login experience drastically reduces exposure to cyber attacks, improving both security and productivity.
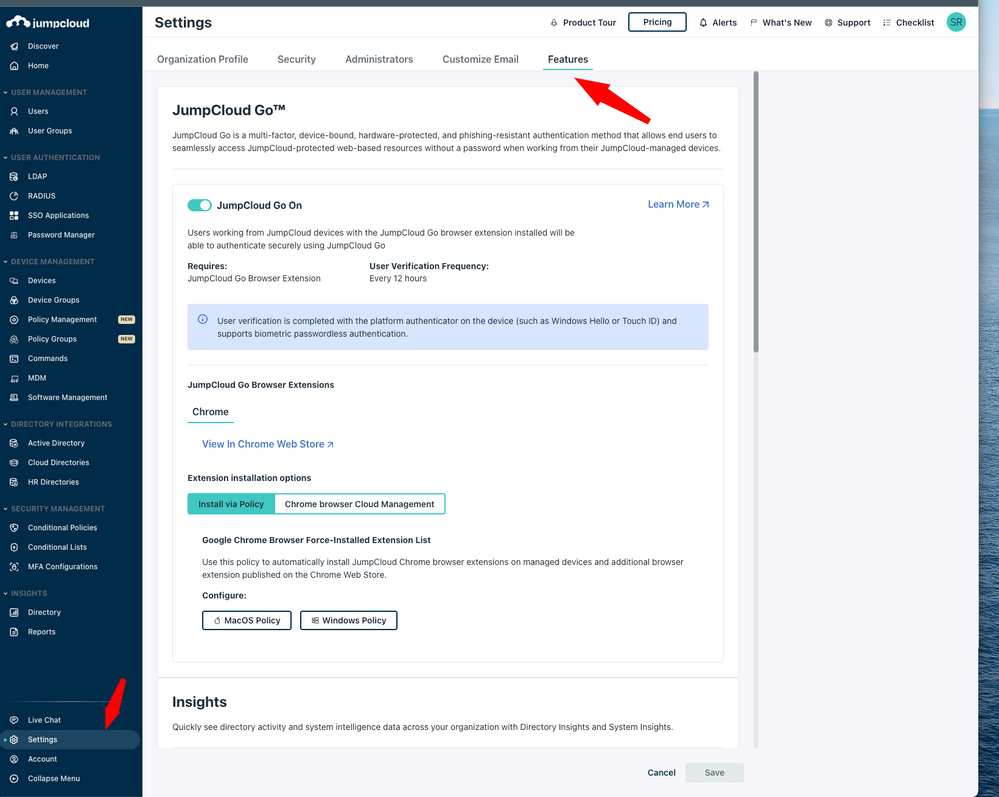
In order to use JumpCloud Go users must be working from JumpCloud Agent managed devices that have a JumpCloud Go browser extension installed. The JumpCloud Agent can be used alongside any device management tool and is not dependent on organizations utilizing JumpCloud for full device management. Organizations can deploy the required browser extension effortlessly using JumpCloud policies or leverage JumpClouds deep integration with Chrome Browser Cloud Management to facilitate and enforce extension installation in Chrome via the Google Admin console. Passwordless login is facilitated by integrations with device biometric authenticators, such as Apple Touch ID or Windows Hello, which combined with JumpCloud Go allows users to satisfy traditional password sign-in challenges without inputting a username or password.
At launch JumpCloud Go is supported within Chrome on Windows/Mac workstations. Additional browser and Linux support is coming soon.
Benefits of JumpCloud Go
Phishing-Resistant Authentication
JumpCloud Go uses phishing-resistant technology to reduce an organization's exposure to: phishing, credential theft, or 2FA bypass cyber attacks. User sessions are issued only after requests are cryptographically verified by a hard-ware protected secret and the JumpCloud login service.
Passwordless Login
JumpCloud Go enables passwordless login to JumpCloud-protected web resources from JumpCloud managed and trusted devices.
Users enjoy a passwordless and secure multifactored login experience to all of their JumpCloud web based resources using JumpCloud Go. Users gain significant time back when they are not constantly required to authenticate using a password and higher friction MFA factors to access organizational resources.
High MFA Authenticator Assurance
Users use hardware-protected managed device-bound authenticators on MacOS and Windows combined with JumpCloud Go to satisfy sign-in challenges. By integrating with device authenticators on trusted and managed devices, JumpCloud Go authentication always represents two authentication factors satisfying “Proof of Possession” and “Knowledge" or "Inherence” factors each time it is used.
Simpler and Safer Employee Experience
The JumpCloud Go user login experience is simpler and more secure for users and seamlessly promotes safer login habits while reducing authentication fatigue. JumpCloud Go significantly reduces the amount of login prompts users face daily and saves organizations valuable time. IT organizations benefit from less end user support requests related to assisting users with lockout, password, or account recovery issues.
3rd Party MDM & EMM Compatible
JumpCloud Go can be used with any device management tool. Pair it with JumpCloud MDM or integrate it with any enterprise mobility management (EMM)/mobile device management (MDM) solution.
Start Using JumpCloud Go Today!
Find steps for enabling and using JumpCloud Go below
Feature Enablement & Admin Experience
End User Experience
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2023 04:45 PM
I'm so EXCITED!!!
Like someone's post? Give them a kudo!
Did someone's answer help you? Please mark it as a solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2023 06:14 PM
Wooohoo!!!! Huge day for all the teams at JumpCloud who've worked so hard on making it impossibly easy to login every day. I can use my fingerprint for everything and just... Go!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2023 03:31 AM
Loving this new functionality! Thanks team.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2023 01:11 PM
Super excited! Looking forward to the device login phase too! Cheers to all behind this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-07-2023 03:04 PM - edited 09-07-2023 03:10 PM
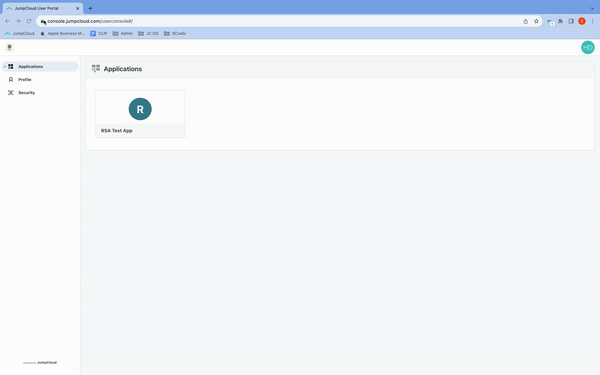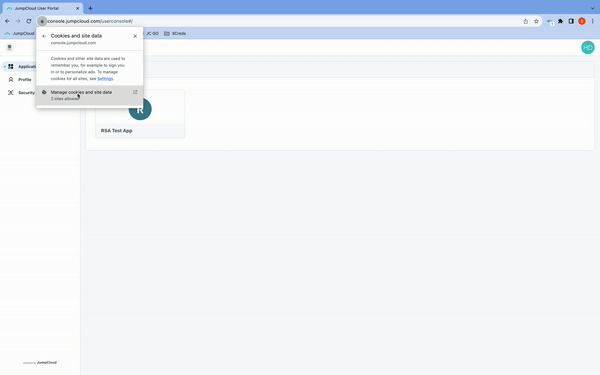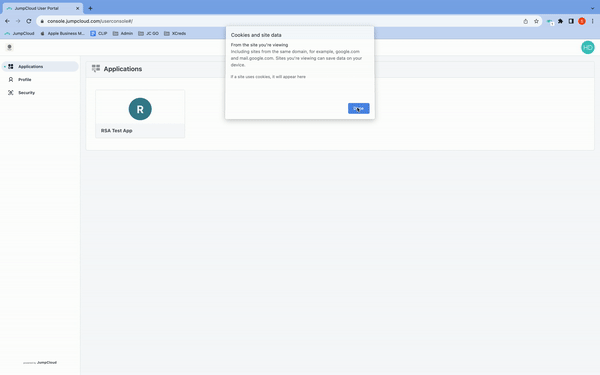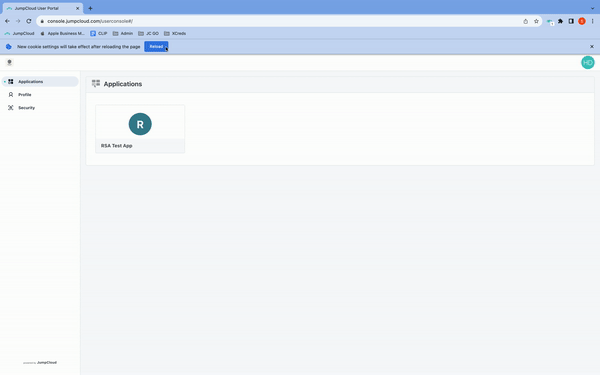
Sharing the outcome of a DM with @rjordan surrounding his testing experience with JumpCloud Go.
During the first login with JumpCloud Go registration occurs..
This is the first (and last) login users do and is a traditional auth to the user portal
After this the passwordless magic kicks in
To see/test the passwordless magic in real time, and not wait out the 12 hour timeout, the following steps can be used.
After logging in with JumpCloud Go and when at the user portal
On macOS
- Run the following terminal command: defaults delete com.jumpcloud.DurtService com.jumpcloud.durt.presenceChecked
On Windows
- Restart the JumpCloud agent service in services.msc
Then
- In the JumpCloud user console delete the JumpCloud cookies
- Reload the page
This will jumpstart and trigger the "Passwordless Login" flow in real time.
🚀
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2023 04:54 PM
Thanks Scott! I'll reach out more here in the community. After last week's episode it was a nice reminder for me to be looped into the latest/greatest JC here and give feedback, ask questions, etc.
Cheers!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2023 12:22 PM
Hi Scott,
What options are available on Windows devices if you have Windows Hello disabled org wide due to its many security vulnerabilities, the biggest of which is it enables users to bypass JumpCloud MFA requirements. I have 1,000+ endpoints in my org and in order to follow what we have committed to via compliance and agreements with our partner orgs, we had no choice but to disable Windows Hello.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2023 12:39 PM
👋🏻
JumpCloud Go is not dependent on Windows Hello. Windows Hello is what can make the daily user verification step passwordless for end users. For users/organizations that have disabled Windows Hello (or do not have it configured) the daily user verification step after Go registration differs to the configured Sign-in options on the Windows device (which in your case would be a a password only). This means that users would register for JumpCloud Go using their JumpCloud password (and any configured user portal MFA policies) and then each day input their password once (prompted & authenticated by the device locally via the WIndows Security app) to use their device bound JumpCloud Go credential for passwordless authentication.
If you want to test this out in real time follow the steps two posts up (Sign in via JC Go, restart JumpCloud Agent Service, clear cookies) and you'll experience the daily user verification flow that will be triggered by the "Windows Security" app and a locally authenticated password.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2023 01:17 PM - edited 09-08-2023 01:18 PM
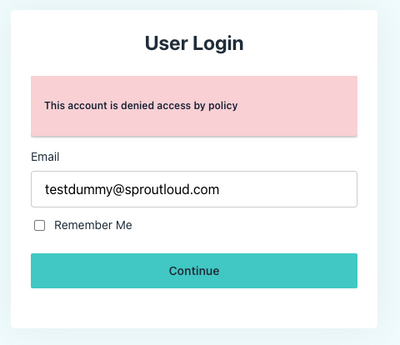
I'm getting this when I try logging in with JumpCloud Go - "This account is denied access by policy"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2023 12:06 PM
@jaggrey have you set everything up as described in the guide that Scott linked? Did you have any issues with the set up?