- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Populating JumpCloud’s open directory will help you understand how it will work for you. Creating devices can work by distributing an agent to a target device (or group of devices), or through MDM protocols (based on the types of the devices you intend to manage).
Completing this demo walkthrough will grant you access to features such as:
- Single sign-on to all of your resources and environment-wide MFA
- Dynamic groups to make IT admins more efficient with the benefit of continuous attestation.
- Assigning users to managed devices to achieve a Zero Trust posture with phishing-resistance access control … all from one place and with minimal effort.
Now, let’s get started. It’s a few simple steps, and you’re on your way to getting things done.
Demo Overview
Adding a device is a great way to understand the JumpCloud features that will be at your disposal once endpoints are being managed. You’re covered for cross-OS device management, with options to manage a wide variety of operating systems and device types (not to mention use cases and ownership models). JumpCloud can even connect with an existing identity provider (IdP) like Okta or Google Workspace to integrate device and identity management.
The JumpCloud platform integrates universal endpoint management with directory services (including Active Directory) for holistic access control. You don’t need point solutions for single sign-on (SSO), multi-factor authentication, and more. It can all start with device management.
Prerequisites
Not every step here is necessary to complete this tutorial. However, if you want to experience your evaluation of this (and other) feature as if you’re implementing the product, we recommend the following:
- Complete the following walkthroughs (or have set up your instance with the appropriate assets on your own):
- Creating JumpCloud Admins
- A test device or VM
- Create a Dynamic User Group (optional)
In addition, it’s necessary to have a test group accessible ahead of this walkthrough if you want to practice that step.
Demo Walkthrough
JumpCloud agents gather device telemetry and deploy policies for desktop operating systems. Agents can be combined with MFA for Windows for tamper-proof endpoint management. This demo focuses on using agents to add either Linux, macOS, or Windows boxes to your organization. We’ll show you how to deploy agents, view device details, and then will explore policies (and more) to demonstrate JumpCloud’s cross-OS device management.
JumpCloud combines user and device management into a single console, which provides asset-based security. Android EMM and Apple MDM are also included in the platform for no additional cost. Device management is just the start of what’s possible.
Adding a device takes just a few minutes. This walkthrough unlocks your ability to explore what’s possible with commands, policies, reporting, and how integrating device and identity management can enable Zero Trust security. You can even manage devices for identities that reside within other Identity Providers (IdPs) to help protect your resources and privileged users.
If you have time, we strongly suggest deploying JumpCloud Go for passwordless logins. It’s a phishing-resistant credential that eliminates the problem of MFA fatigue for users while fortifying your security. Simulations and other resources will show you how to set up MFA, Conditional Access, and Go. Patch Management for OSs and browsers is another option once agents are deployed; integrated remote access and troubleshooting is also there for you to try.
Step 1: Add the Device
Do more, with less effort. JumpCloud can automatically group devices as they’re added to the cloud directory using conditions such as their type operating system. You’ll see the device(s) that you add in this walkthrough automatically populate into your dynamic device group.
Policies can be applied against that group to make it easier for you to have a healthy device posture for Day 1. We’ll explore policies in more detail below, after you’ve added a device.
Simulation: Enable and Configure Dynamic Device Groups
Create a dynamic group or just skip ahead and get started to add a device.
To get started, simplly:
- Log in to the JumpCloud Admin Portal.
- Go to Device Management > Devices.
- Select the Devices tab.
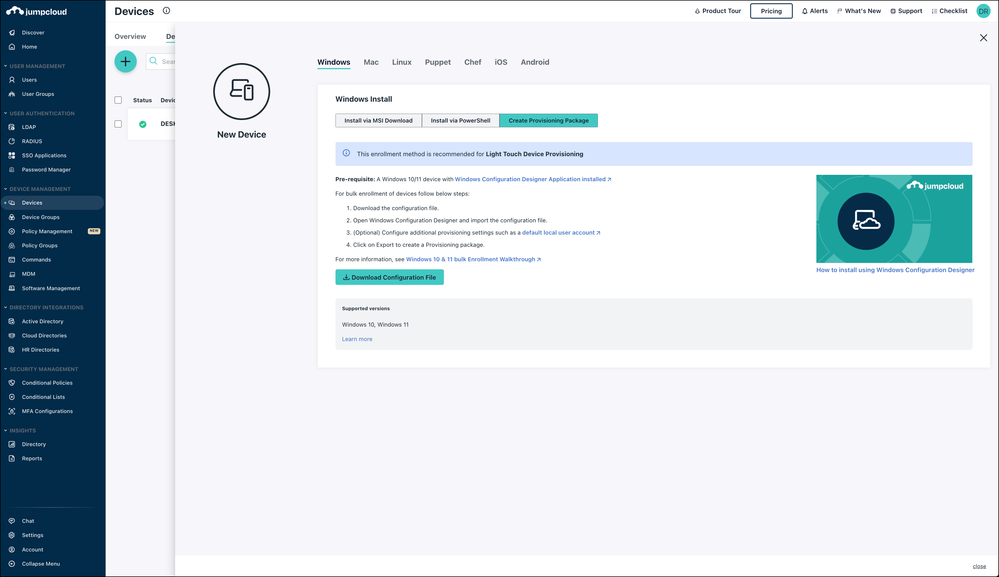
- Click ( + ). The New Device panel that appears contains various device tabs. Each tab includes information about downloading and installing the JumpCloud agent for that device’s OS. You can also read the following about installing agents from the command line, template or System Image, or the JumpCloud API.
- (Optional) You can add the JumpCloud agent to your allow list with your AntiVirus vendor.
- After installation completes, the agent checks in with JumpCloud and is active in the Admin Portal. You can view details about the device on the Device panel
Resources: Add a Device
Step 2: Explore Device Details
Once you've added your device, you can:
- Log in to the JumpCloud Admin Portal.
- Go to Device Management > Devices.
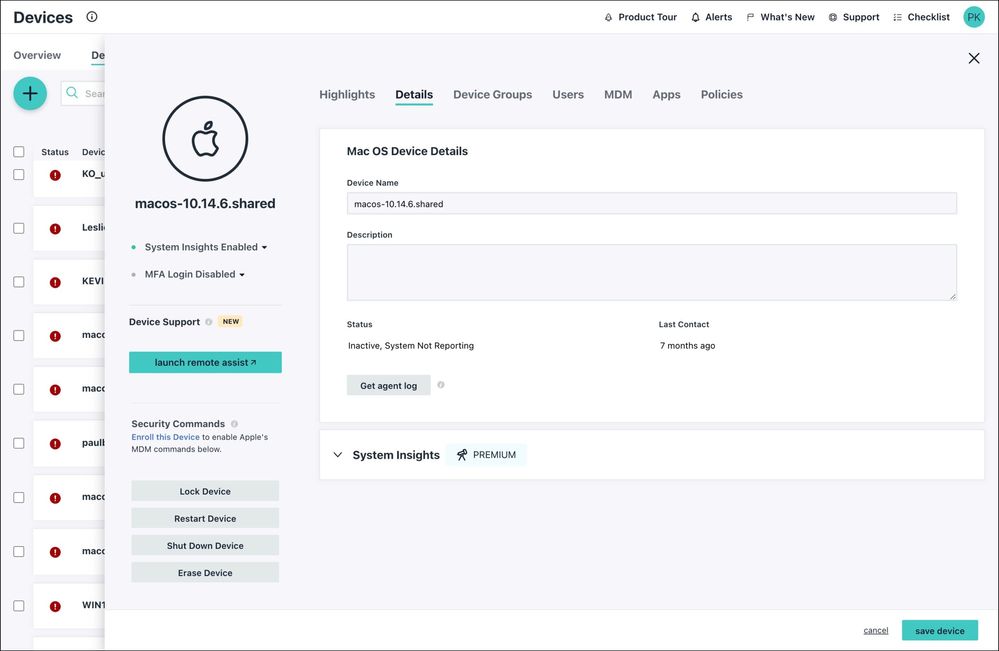
- Select the Devices tab, then select a device.
- Review the reporting information in the Highlights tab, as well user, device groups, and policies that are bound to this device.
Tip: Search for a device or click “filter by” and narrow your search by serial number, OS version, enrollment status, system name, or JumpCloud system ID.
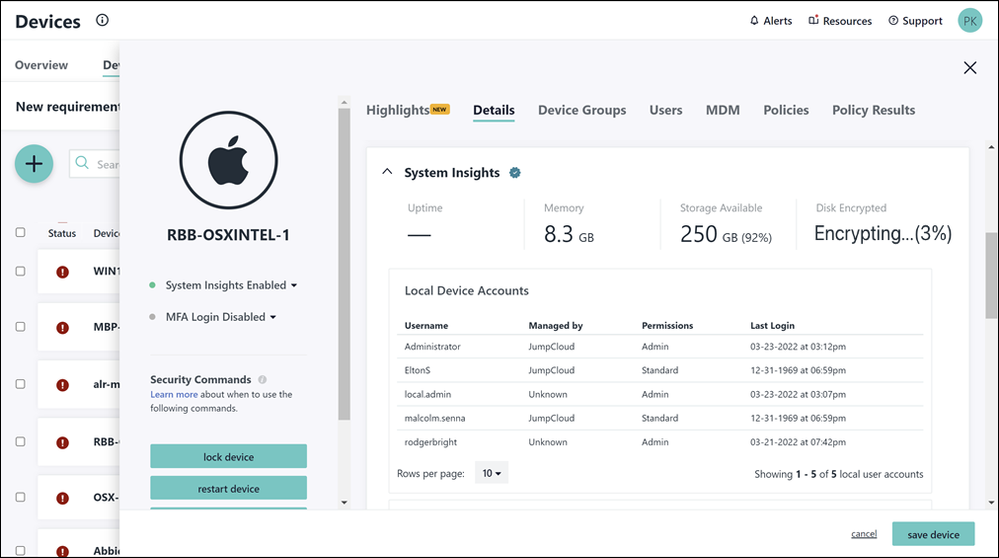
System Insights
A built-in tool called System Insights delivers telemetry across your fleet for compliance reporting, troubleshooting, and actionable security information. You can easily gather information from JumpCloud-managed devices with our RESTful API and PowerShell Module.
Prerequisites:
- System Insights is included in some of our package plans. See JumpCloud Pricing for information on our package plans.
- To enable System Insights for your account, current customers can contact systeminsights@jumpcloud.com. New customers can contact sales@jumpcloud.com.
- System Insights supports 64-bit operating systems.
To automatically enable System Insights for new devices:
- Under Settings > Features, toggle System Insights on or off.
- Under Auto enable System Insights on new devices, select which devices you’d like to enable this feature. Newly added devices will automatically have System Insights enabled.
- Devices that existed in your account prior to turning on auto-enablement require that you manually enable System Insights for an individual device.
Resources: System Insights
Step 3: Secure Your Devices
You can do as many or as few of these activities as you choose, but it’s best to think of this as an action list for your evaluation. Here’s some of the essential features to secure your endpoints.
Assign Policies to Devices
Check out this tutorial on configuring policies!
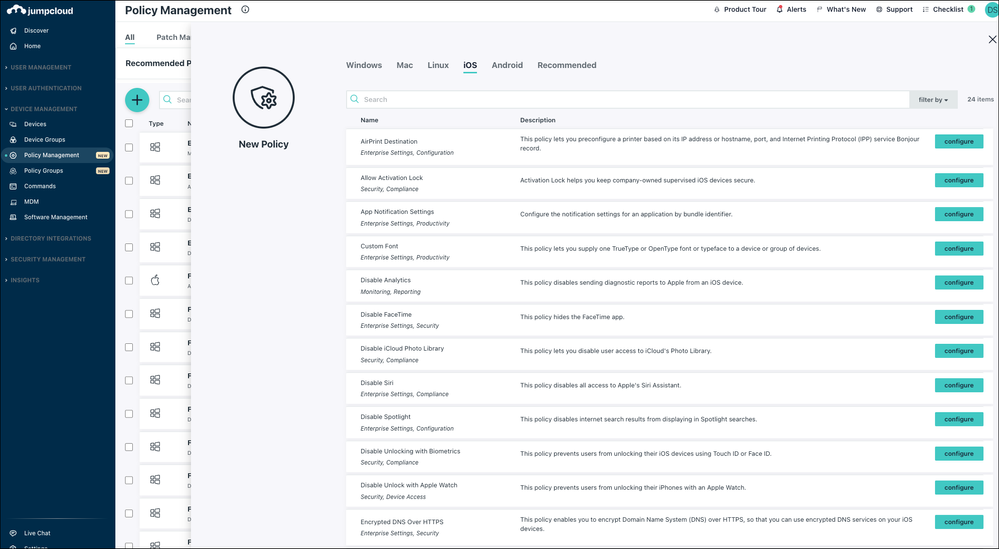
To create a policy:
- Log in to the JumpCloud Admin Portal: https://console.jumpcloud.com/login.
- Go to Device Management > Policy Management.
- In the All tab, click (+).
- On the New Policy panel, select a tab for the desired OS.
- Select a policy from the list, then click configure.
Resources: Get Started with Policies, Configure Settings for Mac Policies, Configure Settings for Windows Policies, Configure Settings for Linux Policies
Tip: Policies may be assigned to individual devices or device groups.
Enable TOTP Multi-factor Authentication (MFA)
JumpCloud Protect Mobile Push MFA and biometric options are available (if your device supports it). This walkthrough will help you help up MFA for your organization.
First add users and user groups. We also have a quick walkthrough on how to manually create users to expedite this step. You must have already created a device group to bind it to the device.
- Go to User Management > User Groups.
- Select the user group by clicking anywhere on the user group’s row.
- Select the Device Groups tab.
- Click the checkbox next to the device group you want to bind the user group to.
- Click save.
- Click Bind Device Groups.
Configure TOTP MFA for user accounts first; learn how to do this in Add MFA to a JumpCloud User walkthrough.
To enable TOTP MFA on your devices:
- Log in to the Admin Portal: https://console.jumpcloud.com/login.
- Go to Device Management > Devices.
- Select the checkbox next to the devices you want to enable TOTP MFA on.
- Click more actions.
- Select Enable MFA.
- Confirm by selecting enable.
Resources: Enable TOTP MFA for Devices, Add User Groups to Device Groups
Enroll a Device in Windows MDM
JumpCloud Windows MDM can not be tampered with by end users attempting to remove JumpCloud agent or MDM management. This is a free feature with no additional fees required that has the added benefit of. Don’t worry: devices that are already being agent managed can be added to Windows MDM using a toggle. Here’s how you'd set it up as an admin and user.
As an admin:
- Go to Device Management > MDM.
- Click the Windows tab.
- To enable MDM for your users, select Allow users to enroll devices into Windows MDM through the User Portal.
To automatically enroll all users with Windows 10 & 11 devices into Windows MDM, select Automatically enroll all Windows 10 & 11 devices into Windows MDM.
Use Windows MDM (End User)
Note: Admin permissions are required to enroll a device into JumpCloud MDM via the user portal. This is a Windows MDM requirement.
- Log in to your JumpCloud User Portal.
- Click the Security tab.
- In JumpCloud Device Enrollment, select the Windows operating system and click Start MDM Enrollment.
Resources: Get Started with Windows MDM, Windows MDM Enrollment via Provisioning Package
Compliance Reporting
To export all of your device information from the GUI for audits, compliance, or troubleshooting reports, click export to export to either CSV or JSON.
- Log in to the Administrator Portal: https://console.jumpcloud.com.
- Go to Device Management > Devices.
- Click export, then select either Export JSON or Export CSV.
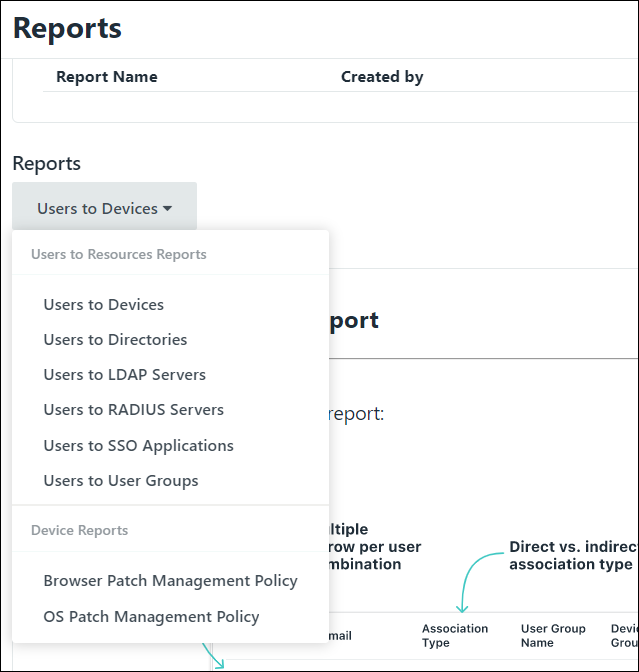
There are also pre-built reports accessible, such as Users to Devices.
Resources: JumpCloud’s IT Compliance Quickstart Guide
Step 4: (Recommended): Go Passwordless with JumpCloud Go™
Prepare Your Systems
- JumpCloud Go supports macOS and Windows devices that meet these hardware specifications:
- macOS devices with a Secure Enclave.
- Windows devices with a Trusted Platform Module (TPM) 2.0.
- The JumpCloud agent has to be installed and running on macOS and Windows devices. See Install the Mac Agent and Install the Windows Agent.
- Google Chrome browser with the JumpCloud Go browser extension installed.
Prepare Your Users
- Users need to be working from their JumpCloud-managed device and logged in to their managed device account. JumpCloud Go does not support local device accounts.
- Users will need to configure biometrics on their device to be able to utilize them with JumpCloud Go:
- For macOS devices, see Apple’s Use Touch ID on Mac.
- For Windows devices, see Microsoft’s Learn about Windows Hello and set it up.
Deploy It
- Install the browser extension
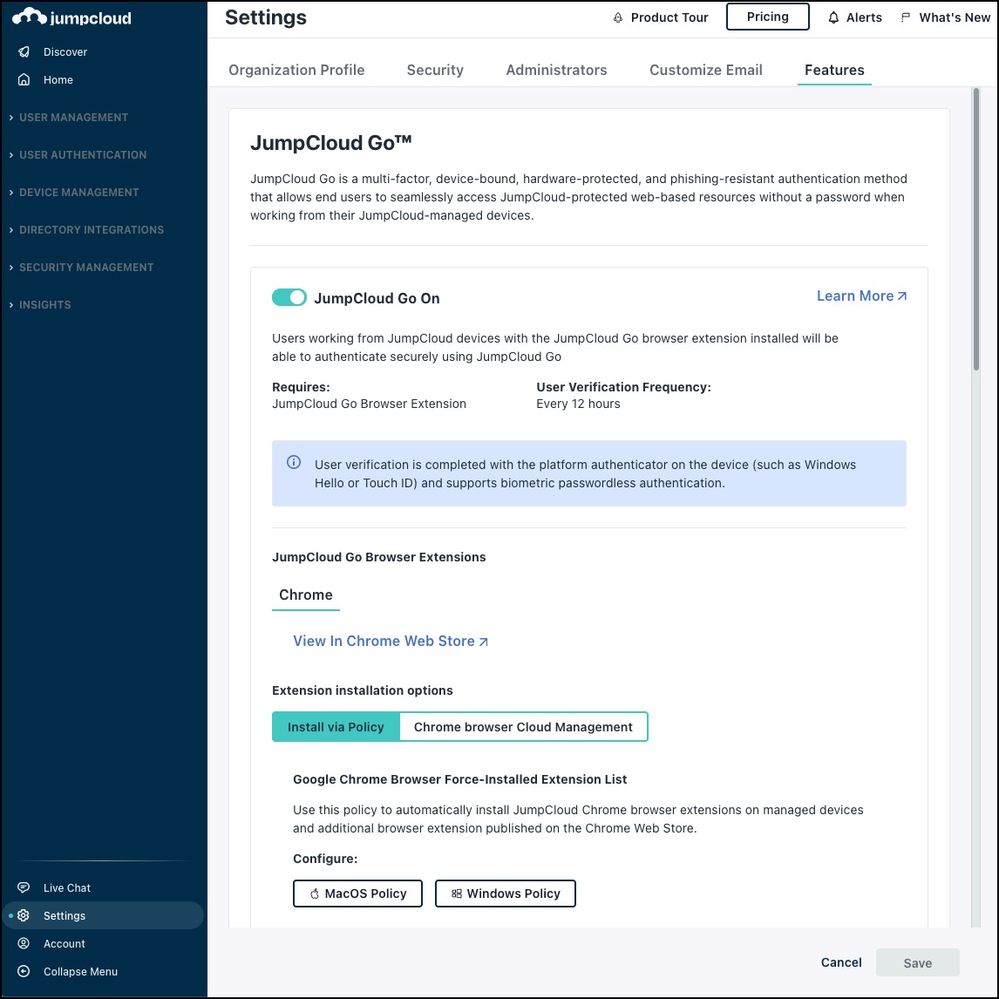
- Enable JumpCloud Go for Your Organization
- Go to Settings > Features > JumpCloud Go.
- Click to toggle JumpCloud Go to On.
- Click Save.
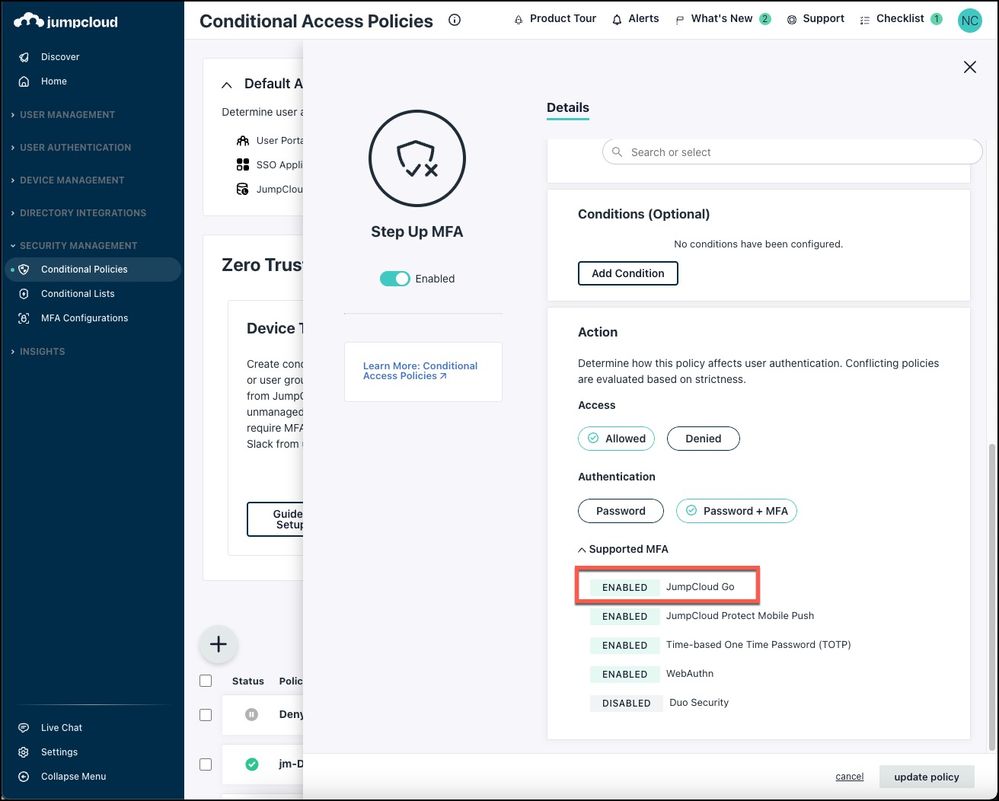
Use Step Up MFA
Enabling JumpCloud Go in Features will automatically enable it as an MFA factor for your users. JumpCloud Go SSO requests have security with user and device verification occurring during every new application session established using Go. Users that authenticated to the User Portal with JumpCloud Go will now use the Go loader while accessing their SSO applications.
JumpCloud Go is the default MFA method for SSO Conditional Access policies. When a user accesses an application that’s protected by a policy, they'll be prompted to "step up" and verify their identity using JumpCloud Go.
Note: JumpCloud Go provides instant revocation when a user status changes from “active” to “suspended”. That’s possible because the platform has integrated identity and device management.
Users must first register JumpCloud Go with their credentials before passwordless verification becomes available. Try it out. It’s simply easier than TOTP, and even more secure.
Resources: Get Started with JumpCloud Go™, JumpCloud Go™: A Simpler, More Secure Login Experience
Try Remote Access
Establish secure, direct connections and troubleshoot devices whether on-prem or remote to solve active technical issues. JumpCloud Remote Access provides a combination of Remote Assist and Background Tools to take remote sessions and troubleshoot Windows, Mac, and Linux devices from a single console. This is accessible after your agent is installed, but can be disabled if your organization has compliance or security policies that won’t allow it.
Using JumpCloud’s Remote Access means one less invoice.
Check out this tutorial to see how Remote Assist works.
Resources: Get Started with Remote Assist
Bonus Simulations
Enable and Configure Dynamic Device Groups
Conditional Access | Device Trust
Android Enterprise Mobility Management (EMM)
Final Results
Thanks for taking the time to get started with your evaluation. Device management is essential for asset-based security. You cannot protect identities without also managing your devices (and keeping those endpoints in a healthy posture). Likewise, devices are better protected when UEM is integrated with identity and access management.
Get prepped now
Create a dynamic device group and add managed users to devices.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.