- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
RADIUS remains one of the biggest hurdles for orgs moving to passwordless. Admins often have to maintain and support the Windows Network Policy Server (NPS) role and configure a hybrid Active Directory environment in order to authenticate into network devices. Otherwise, it becomes necessary to pay for a separate cloud-based RADIUS service as a point solution.
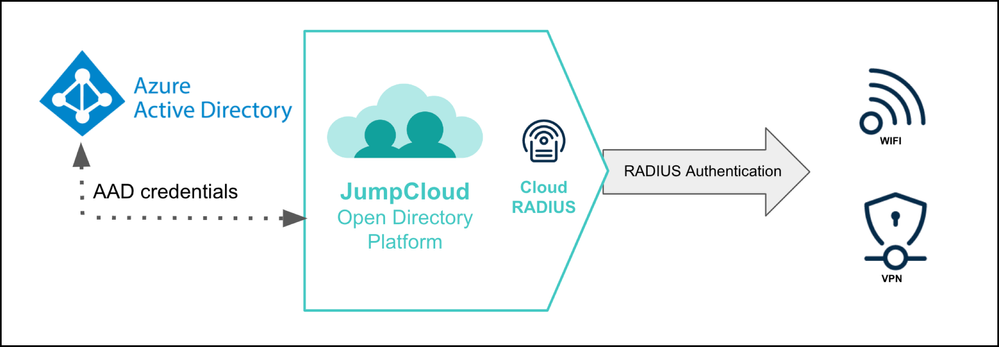
JumpCloud’s open directory platform provides Cloud RADIUS without the server hassle. It also makes it possible to delegate to Entra ID for use as your Identity Provider (IdP). Certificate-based authentication provides the most security and least friction for your users, but the platform also offers environment-wide MFA for password-based authentication.
Cloud RADIUS can be combined with JumpCloud Go™, a hardware-bound credential that works across endpoint operating systems, to eliminate the need for passwords within your organization. Don’t worry: it also offers Password Manager for instances when they’re required.
Ultimately, you’ll gain more security and greater user acceptance/experience.
Demo Overview
Adding up a RADIUS server with MFA is easy. It takes more time working with certificates, but it’s fully documented for your benefit. This will only take a few minutes. Let’s get started.
Prerequisites
Not every step here is necessary to complete this tutorial. However, if you want to experience your evaluation of this (and other) feature as if you’re implementing the product, we recommend the following:
- To complete this tutorial, we recommend that you have completed tasks:
Demo Walkthrough
Are you a visual learner? Check out this tutorial first.
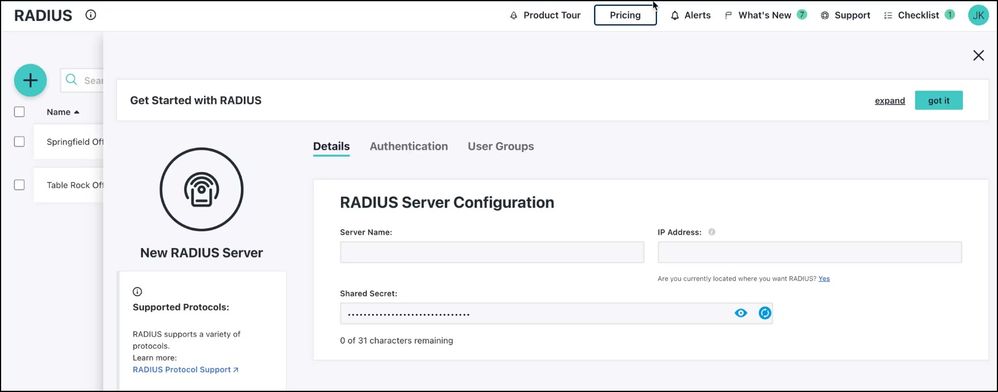
Step 1: Add a RADIUS Server
- Log in to the JumpCloud Admin Portal: https://console.jumpcloud.com/login.
- Go to RADIUS.
- Click ( + ). The New RADIUS server panel appears.
- Configure the RADIUS server:
- Enter a name for the server. This value is arbitrary.
- Enter a public IP address from which your organization’s traffic will originate.
- Provide a shared secret. This value is shared with the device or service endpoint you’re pairing with the RADIUS server. It goes without saying – keep it a secret.
Resources:
RADIUS Configuration and Authentication
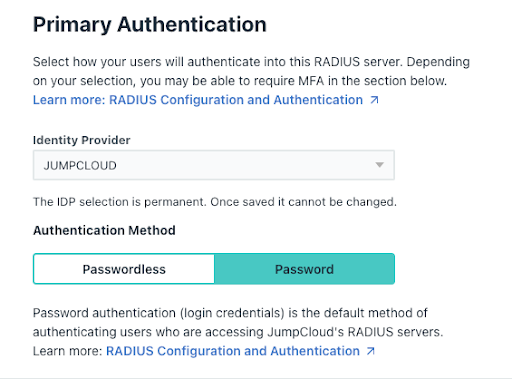
Step 2: Choose an IdP
- To select how your users will authenticate into this RADIUS server, click the Authentication tab and choose an Identity Provider from the dropdown menu.
- If the selection is Entra ID, users will be able to access this RADIUS server using their existing Entra ID credentials. MFA cannot be configured when Entra ID is the identity provider.
Important:
- Once Entra ID is selected and confirmed, this selection cannot be changed without deleting this RADIUS configuration and starting over.
- Entra ID doesn’t pass the user’s password to JumpCloud, so the user remains in a Password Pending status. If an Entra ID organization is using JumpCloud exclusively for RADIUS, admins do not require users to create a password in JumpCloud, so the Password Pending status can be ignored.
RADIUS Authentication with Entra ID Credentials
If the selection is JumpCloud, admins will have the choice of Passwordless or Password for the Authentication Method.
Resources:
RADIUS Configuration and Authentication
Authenticate to RADIUS with Azure AD
Step 3: Choose an Authentication Method
JumpCloud RADIUS supports both credential (with a password) and certificate (passwordless) based authentication. Certificate Based Authentication (CBA) is considered the most secure method of authentication, with the least amount of user friction. Learn More: Certificate Based Authentication to RADIUS for Admins
Password Authentication
- To continue letting users authenticate with their username or email address and password, plus TOTP or PUSH, select Password as the authentication method.
- The MFA Configuration section will be available if using JumpCloud as the Identity Provider, and if Password is selected as the Authentication Method.
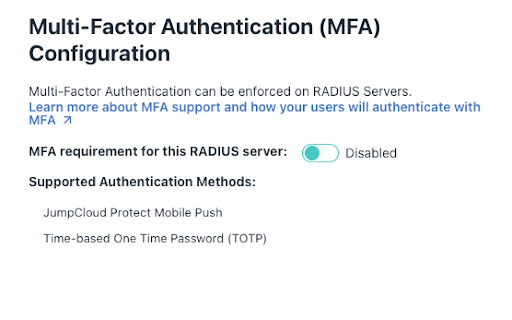
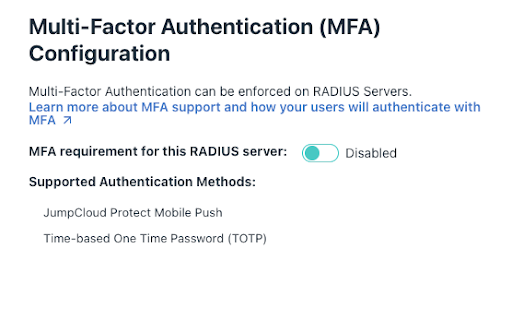
- Configure Multi-Factor Authentication (MFA)
- Toggle the MFA Requirement option to “Enabled” for this server. This option is Disabled by default.
- Select Require MFA on all users or Only require MFA on users enrolled in MFA.
- If selecting Require MFA on all users, a sub-bullet allows for excluding users in a TOTP enrollment period, but this does not apply to JumpCloud Protect (users in a TOTP enrollment period who are successfully enrolled in Protect will still be required to complete MFA).
- If JumpCloud Protect is not yet enabled, users can select the Enable Now link.
Passwordless Authentication
- To use certificate authentication, select Passwordless.
- Once Passwordless has been selected, the Save button will be disabled until a certificate has been successfully uploaded (or the authentication method has been changed back to Password).
- If desired, select Allow password authentication as an alternative method.
- If this checkbox is selected, admins can enable certificates for some users while allowing others to continue validating by username or email address and password. Users will continue to have the option to validate by username or email address and password, but once they choose to validate with certificates and a valid certificate is found, the password option will no longer be presented.
- The MFA Configuration section will be available if using JumpCloud as the Identity Provider, and Passwordless is selected as the Authentication Method, and the Allow password Authentication as an alternative method checkbox is selected.
- Configure Multi-Factor Authentication (MFA)
- Toggle the MFA Requirement option to “Enabled” for this server. This option is Disabled by default.
- Select Require MFA on all users or Only require MFA on users enrolled in MFA.
- If selecting Require MFA on all users, a sub-bullet allows for excluding users in a TOTP enrollment period, but this does not apply to JumpCloud Protect (users in a TOTP enrollment period who are successfully enrolled in Protect will still be required to complete MFA).
- If JumpCloud Protect is not yet enabled, users can select the Enable Now link.
- Uploading a Certificate Authority
- To upload your certificate, click on the Choose a File button, navigate to the file location, and select it for uploading.
- Once the file has uploaded successfully the file name will display on the screen and options will change to replacing or deleting the file. There is also an option to view the full CA chain.
- Clicking Save will return the user to the main RADIUS screen, where the Certificate badge will display in the Primary Authentication column.
Note: For more information about where and how to find trusted certificates outside of JumpCloud, see the RADIUS-CBA Tools for BYO Certificates white paper (PDF).
Resources:
Certificate Based Authentication to RADIUS for Admins
JumpCloud RADIUS Certificate based Auth 3rd Party Tools for BYO Certificates
Bonus Simulations
Install the Agent of Windows Devices (Simulation)
Final Results
You’re one step closer to being a passwordless enterprise. You’ll be more resilient against phishing while gaining more user acceptance of security controls.
Get prepped now
Enroll devices to configure JumpCloud Go™.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.