Jumpcloud linux agent on debian 10 is disconnecting remote users when jump cloud protect MFA is enabled
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2022 09:55 AM
We're evaluating jump cloud with a test linux box having debian10. The testuser can connect fine with password and public keys (managed by jumpcloud). But when we enable MFA with Jump Cloud Protect, the sshd of the linux box disconnect users after successfull authentication.
When MFA is disabled, the user can login normally
The sample /var/log/auth.log is as below:
----
Jul 5 13:29:06 jumptest sshd[6785]: pam_warn(sshd:auth): function=[pam_sm_authenticate] flags=0x1 service=[sshd] terminal=[ssh] user=[testuser] ruser=[<unknown>] rhost=[xxx.xxx.xxx.xxx]
Jul 5 13:29:06 jumptest sshd[6786]: pam_jc_push_mfa(sshd:auth): In child process with pid 6786
Jul 5 13:29:06 jumptest sshd[6786]: pam_jc_push_mfa(sshd:auth): Handling GetEnabledFactors request
Jul 5 13:29:06 jumptest jc_localgrpc[6786]: connectLocalAgent() - dialing unix:///tmp/jumpcloud-grpc
Jul 5 13:29:06 jumptest jc_localgrpc[6786]: Successful connection
Jul 5 13:29:06 jumptest jc_localgrpc[6786]: requesting UserInfo for username: "testuser"
Jul 5 13:29:06 jumptest jc_localgrpc[6786]: response result: %!t(jumpcloudagentlocalproto.UserInfoResponse_UserInfoResult=0), enabledFactors: [{"factor":{"type":6}}]
Jul 5 13:29:06 jumptest jc_localgrpc[6786]: Push factor is enabled for user testuser
Jul 5 13:29:06 jumptest sshd[6785]: pam_jc_push_mfa(sshd:auth): Asking the user Authentication by phone required.
Jul 5 13:29:06 jumptest sshd[6786]: pam_jc_push_mfa(sshd:auth): Handling AuthenticatePushFactor request
Jul 5 13:29:06 jumptest jc_localgrpc[6786]: connectLocalAgent() - dialing unix:///tmp/jumpcloud-grpc
Jul 5 13:29:06 jumptest jc_localgrpc[6786]: Successful connection
Jul 5 13:29:06 jumptest jc_localgrpc[6786]: AuthenticatePushFactor - requesting auth for username: testuser, factorTypeId: 6
Jul 5 13:29:18 jumptest jc_localgrpc[6786]: response result type: *jumpcloudagentlocalproto.AuthenticateFactorResponse_Payload, payload: {}
Jul 5 13:29:18 jumptest sshd[6785]: pam_jc_push_mfa(sshd:auth): Push factor authentication accepted for user testuser
Jul 5 13:29:18 jumptest sshd[6785]: pam_jc_push_mfa(sshd:auth): Waiting for child process pid 6786 to exit
Jul 5 13:29:18 jumptest sshd[6786]: pam_jc_push_mfa(sshd:auth): Child process exiting cleanly with 0
Jul 5 13:29:18 jumptest sshd[6785]: pam_jc_push_mfa(sshd:auth): Child process done
Jul 5 13:29:19 jumptest sshd[6783]: Accepted keyboard-interactive/pam for testuser from xxx.xxx.xxx.xxx port 50567 ssh2
Jul 5 13:29:19 jumptest sshd[6783]: pam_warn(sshd:setcred): function=[pam_sm_setcred] flags=0x2 service=[sshd] terminal=[ssh] user=[testuser] ruser=[<unknown>] rhost=[xxx.xxx.xxx.xxx]
Jul 5 13:29:19 jumptest sshd[6783]: fatal: PAM: pam_setcred(): Permission denied
- Labels:
-
Device Management - Linux
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2022 09:52 AM
I will see if I can find someone to take a look and help a bit with this.
Like someone's post? Give them a kudo!
Did someone's answer help you? Please mark it as a solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2022 03:35 PM
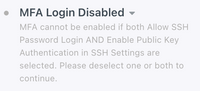
When you enabled MFA for the device, were both SSH password and public key auth enabled? That could be the issue as only 2 of the 3 authentications can be enabled for the device (SSH password, Public Key, and/or MFA).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2022 03:43 PM