- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Many organizations believe they have secure access handled when they roll out single sign-on (SSO)... until an auditor comes in and mandates that network devices like switches and firewalls must also have multi-factor authentication (MFA) enabled for compliance. Active Directory and most cloud Identity Providers (IdP) don’t provide support for LDAP authentication without additional on-premise components. True story: A former team member from a previous job had to set up servers to implement MFA for network devices to pass a PCI audit. His employer didn’t suspend other work; he just had to work more.
JumpCloud provides Cloud LDAP that’s protected by environment-wide MFA, without additional back-ups, servers, licenses, or other failover components to manage. IT teams benefit by being more focused on the work that matters and maximizing the potential of their headcount. Centralizing identity and access management also makes compliance audits easier to handle and less intensive.
Prerequisites
Not every step here is necessary to complete this tutorial. However, if you want to experience your evaluation of this (and other) feature as if you’re implementing the product, we recommend the following:
- To complete this tutorial, we recommend that you have completed the following walkthroughs (or have set up your instance with the appropriate assets on your own):
- Creating JumpCloud Admins
- Creating Users 101
- Creating Groups 101
- Have a test device like an old switch from your shelf
Demo Walkthrough
This walkthrough will show you how to set up an LDAP binding user, add users to the LDAP directory, and manage MFA for access control. You’ll be able to achieve true SSO to all resources. It will only take a few minutes. Let’s get started.
Are you a visual learner? Watch this video tutorial or take this short course at JumpCloud University.
Step 1: Create an LDAP Binding User
- Log in to the JumpCloud Admin Portal: https://console.jumpcloud.com/login.
- Go to User Management > Users.
- Click ( + ), then select Manual user entry.
- Input User Information:
- First Name
- Last Name
- (Required) Username
- (Required) Company Email
- Description
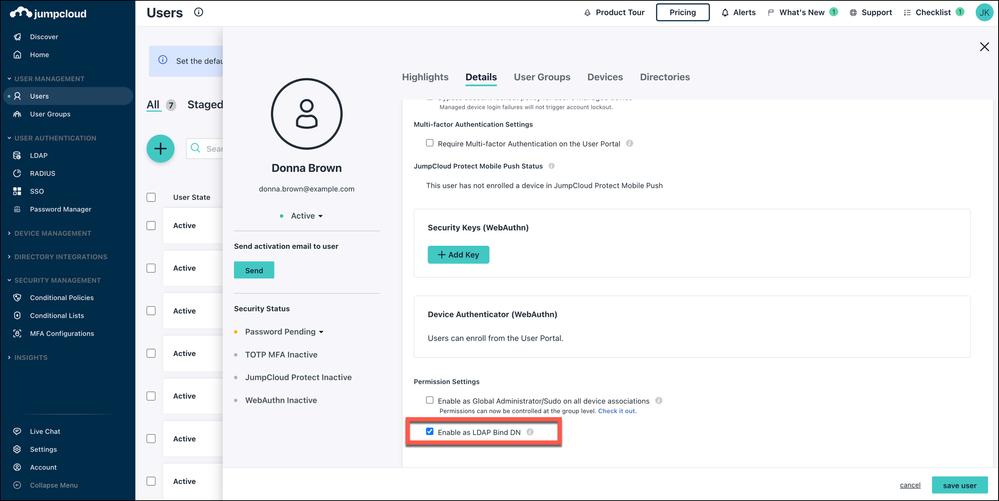
- Under User Security Settings and Permission > Permission Settings, check the box next to Enable as LDAP Bind DN. When enabled, this user acts to bind and search the JumpCloud LDAP directory; one or more users can enable this option.
Considerations:
- It’s not required that this user be a service account. Any JumpCloud user can be set as a binding user, although it’s generally recommended to treat this account as privileged for use only to facilitate the application’s ability to bind/search the LDAP directory.
- The LDAP binding user can be excluded from password expiration policy by selecting PASSWORD NEVER EXPIRES, an option that appears after the user is created. All other password policies are global and will apply.
Resources:
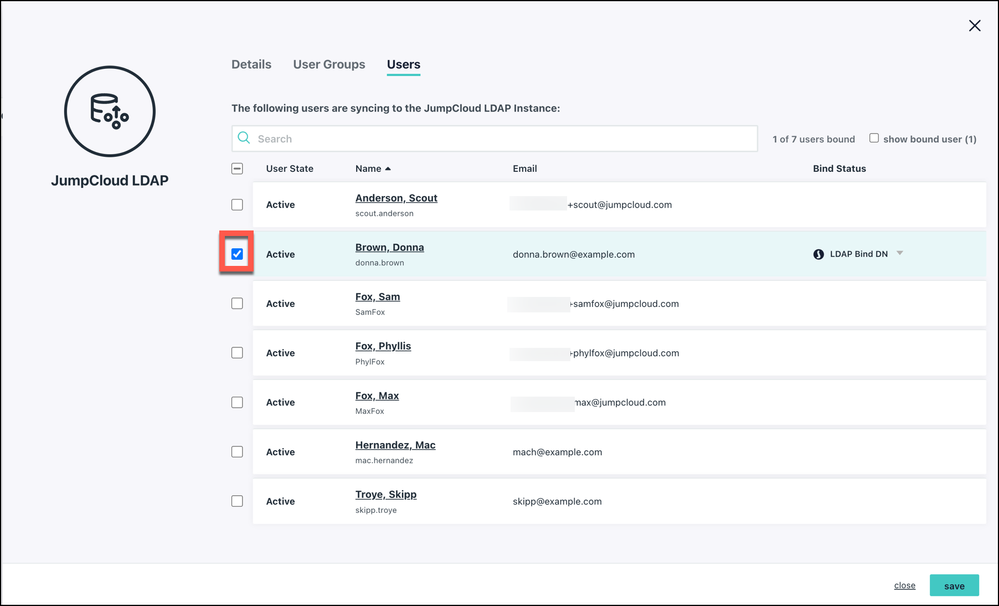
Step 2: Add Users to the LDAP Directory
- Log in to the JumpCloud Admin Portal: https://console.jumpcloud.com/login
- Go to User Authentication > LDAP.
- Go to the Users tab.
- Select users in the list.
- Click save.
In order to authenticate via LDAP, users must be granted access to the JumpCloud LDAP Directory, either individually or via a group.
Resources:
Advanced LDAP (JumpCloud University Course)
Connect New Users to Resources
LDAP Configuration Details and Supported Standards
Step 3: Set up MFA for LDAP
If your organization has LDAP applications that require extra security, you can build a Conditional Policy or Global Policy to enable multi-factor authentication (MFA) as a requirement before users can access the applications.
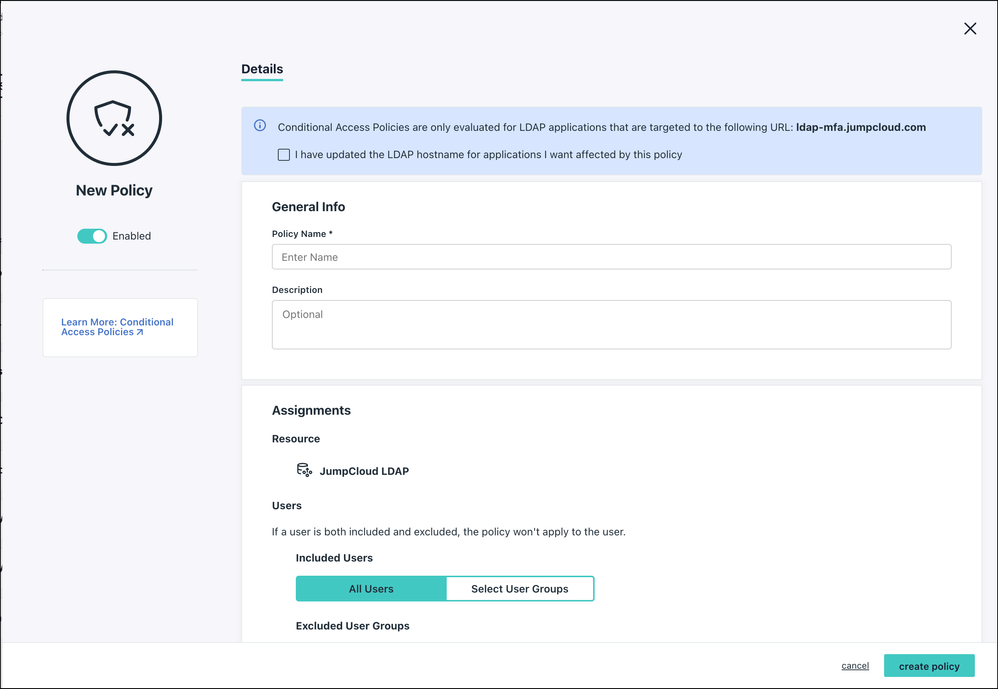
To configure MFA for LDAP Applications as a Conditional Policy:
- Log into the JumpCloud Admin Portal: https://console.jumpcloud.com
- Navigate to Security Management > Conditional Policies.
- Click the green + button and select JumpCloud LDAP.
-
Ensure that your LDAP hostname is updated and click the I have updated the LDAP hostname for applications I want affected by this policy checkbox.
Considerations:
- Conditional Access Policies AND MFA are only supported when the application is configured to the ldap-mfa.jumpcloud.com hostname.
- Some applications will require you to increase the authentication timeout setting.
- Enter the policy name and an optional description. (Optional) If you do not wish for the policy to go live as soon as you finish creating it, move the Policy Status slider to OFF.
- Under Assignments, you can choose to apply the policy to all users or select user groups. You can also specify whether to exclude certain user groups as needed.
- LDAP Bind DN users are excluded by default. To include them, uncheck the checkbox next to (Recommended) Exclude LDAP Bind DN Users. See Use Cloud LDAP for more information on Bind DN users.
- If your LDAP Application requires all of your users to be configured as Bind DN users, then you should uncheck the box and create a user group that excludes your service account.Users must be bound directly to the LDAP Directory in order to log in. LDAP Policies refine access to your resources; they do not grant it.
- Under Action, for Access select the Allowed button, and for Authentication, select the Password + MFA button.
- Note: If you have not enabled JumpCloud Protect or TOTP for your org, you will be prompted to do so.
- Click create policy. You will see the main policies page, and your LDAP policy will appear in that list.
Resources:
Get Started | Conditional Access Policies
Bonus Simulations
Overview of Single Sign-On (SSO)
Enabling MFA For Multiple Users
Final Results
You’ve just learned how to set up a cloud LDAP server. It’s a good starting point, but also considering using Conditional Access for every SSO app for a Zero Trust approach to security.
Get prepped now
JumpCloud Protect can be used to log into the Admin Portal, User Portal (where LDAP apps reside), or devices (Windows, Mac, Linux). Before your users can use the JumpCloud Protect mobile app, you, as an administrator, must enable it.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.