The magical command trigger webhook
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2022
06:45 AM
- last edited on
10-21-2022
10:15 AM
by
![]() BScott
BScott
![]()
Inspired by @JuergenKlaassen 's latest post for Local Admin management - to secure the local admin with an unique and ephemeral password, we can take this a step further by using the the cmd trigger webhook, to pass in "parameters" as the environment variable for the cmd to run, completely invisible to anyone, and leave no trace behind.
So you can follow this guide to setup the cmd trigger and webhook.
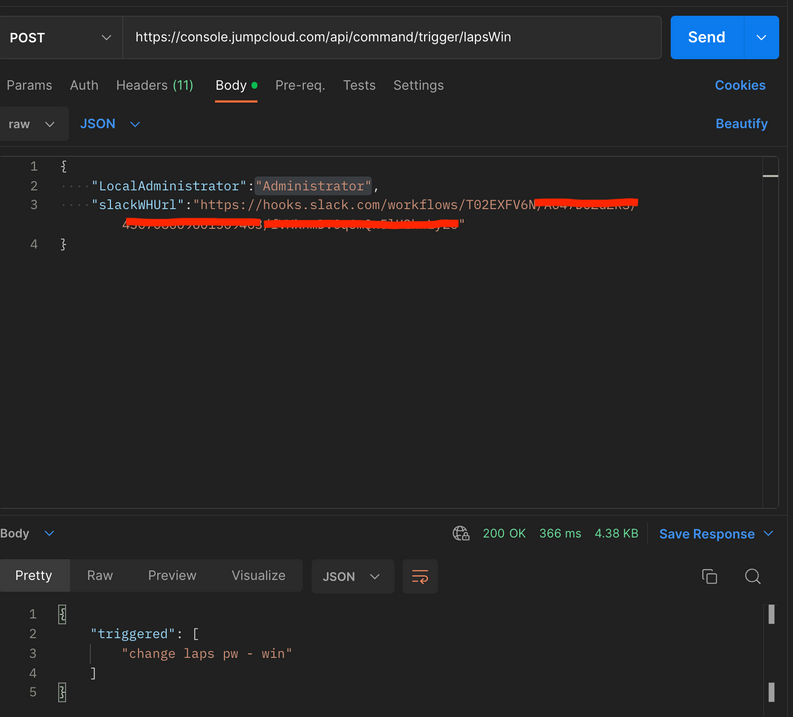
And pass in the variables by simply making a POST call:
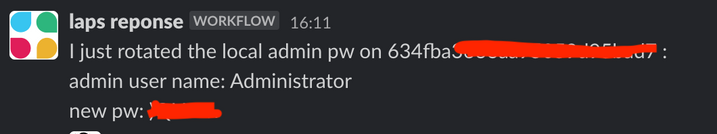
in my case above, i wanted to pass in the administrator account name for creation, and eventually i wanted to have the password delivered in a Slack channel.
Once the cmd successful ran on a windows box, i got this:
Tested login, all good!
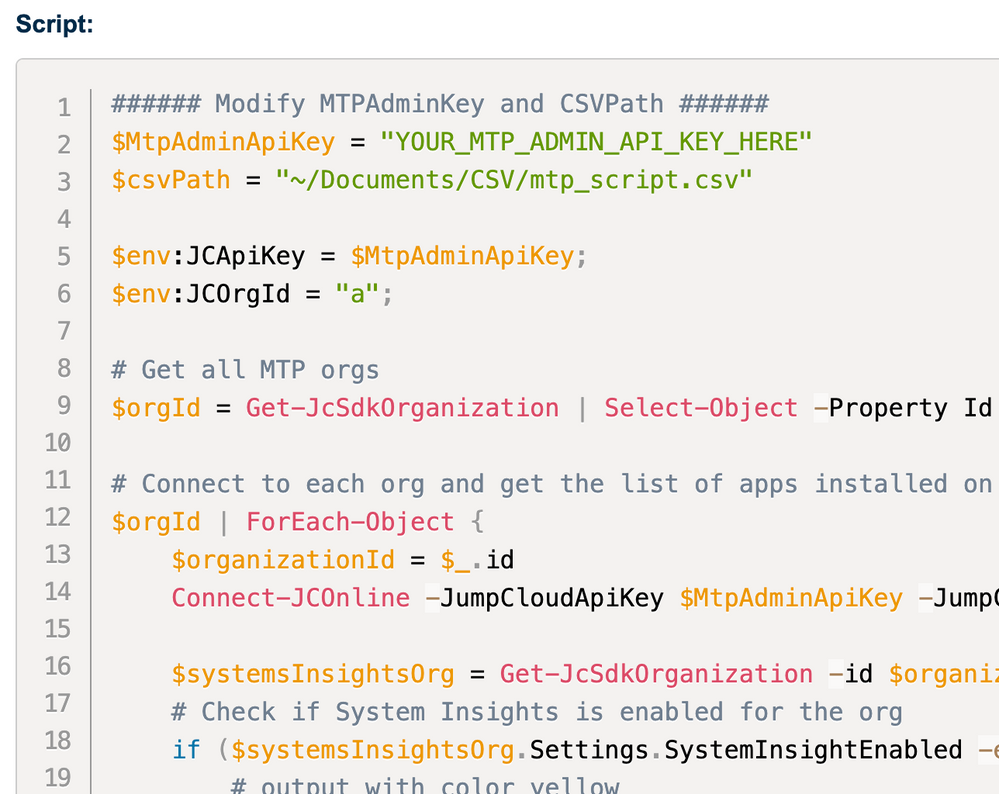
You can find the forked version from Juergen's script here if you want give it a go.
This capability opens a door to the infinite world of possibilities - imagine you can have multiple cmd triggers like modules can be called and pass data with each other 🚀
Happy automating with JumpCloud!
- Labels:
-
API
-
PowerShell
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2022 05:15 PM
Ah this is fantastic! We have a non-jc controlled "sysadmin" account that has full sudo privileges to the servers, but we randomly generate the passwords when creating and storing them in our internal asset tracking system. We've set it so that our COO, Jr. SysAdmin and myself can request the password whenever we need it. Then after 24 hours it connects to the server using the saved password and generates another random one. Having this hook to also alert our systems slack channel will be handy so we have an audit log of who and when they requested it!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2022 07:02 PM
Yep, and for what it worth, if you can pipe the randomly gened pw as the parameters pass in to the hook, actually you will able to keep the pw clear text trace clean - wont show up in cmd results, or leave on the server etc. 😉
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2022 04:03 PM
LOVE, Thank you!