macOS 13.2.1 Security Update: Challenges and Risks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2023 12:22 PM
On Monday, February 13th, Apple released macOS 13.2.1, new minor release of macOS 13 Ventura. This security update contains fixes for three CVEs, most serious among them a flaw in WebKit:
Impact: Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited.
Any security vulnerability that is closed by an update represents a risk for unpatched systems, but this is a full zero-day exploit that has been closed, meaning that Apple has reports of this particular flaw being actively used by an attacker. That this bug is within the WebKit rendering engine -- which powers Safari and any web view generated by an app -- is very concerning, and organizations may want to close this gap immediately.
There's a small problem, though, in a small number of cases -- generally under 2% of systems -- the update does not complete successfully, and users are required to input their user password (if they are admins), or their FileVault Personal Recovery Key (PRK).
More information about recovery paths for this situation are on Robert Hammen's excellent post on recovering from this situation. If your users are admins, they should use their JumpCloud passwords to unlock the disk during the trip through Recovery Mode. If your users are standard users, they should the FileVault Personal Recovery Key, located on their device details aside in the admin portal:
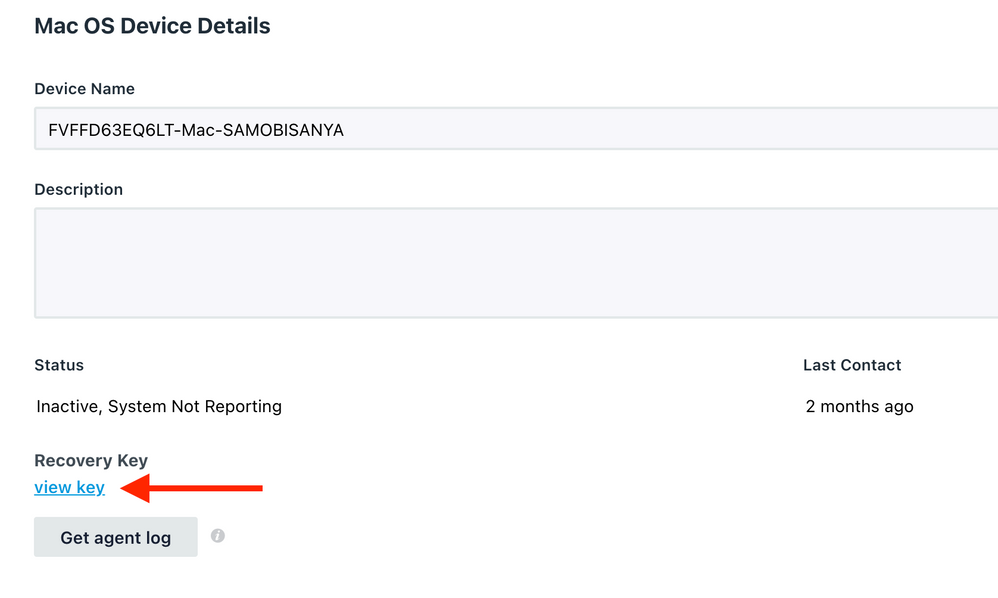
Selecting the view key option will show you the key you need to give your user:
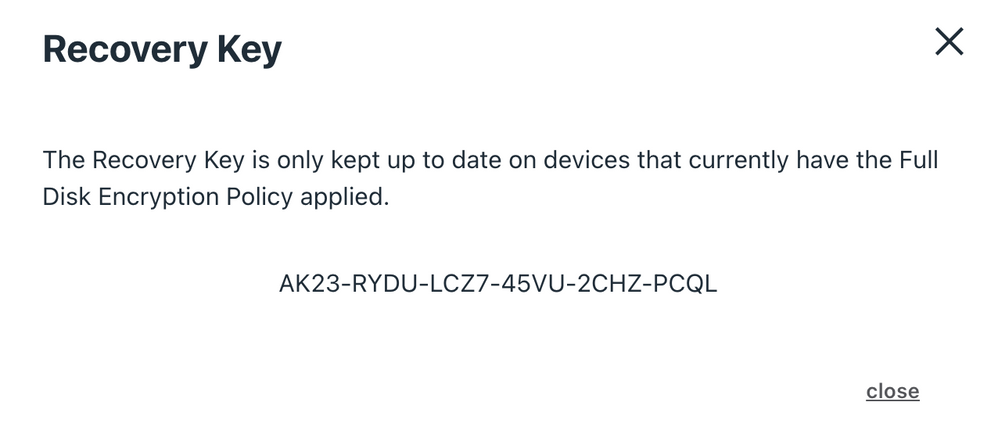
Coping with this situation is tricky, and I strongly encourage you to discuss the risk/reward scenario with your CISO or Internet Security team. Having an exploited zero day in the field is not great, nor is a 1-2% failure rate of the upgrade.
If you choose to delay until this has been fixed in a future release of macOS, you can delay your fleet using our Patch Management policies, or using our Delay macOS Minor Version policy, and set those values to their maximum (90 days) while this is fixed, or a new version is released. Caveats apply: we do not know if this will be fixed in the next OS version, or even when that version will be released, and that the security vulnerability, now that it has been acknowledged, is more likely to be exploited.
This isn't easy or good, but it is something that is knowable.
What are you thinking about this current situation?
- Labels:
-
Deployment and Patching

