- JumpCloud Community
- IT Topics
- Security & Networks
- Commands for Critical Outlook/Exchange Privilege E...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Commands for Critical Outlook/Exchange Privilege Escalation
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2023 04:19 PM - edited 03-16-2023 10:19 AM
It's been a minute since I posted about using JumpCloud Commands for security remediations. There's a particularly nasty zero day that's been actively exploited now that involves attackers obtaining an NTLM hash (Windows password) through Microsoft 365 Apps for Enterprise. That's the self-hosted edition of M365, which isn't vulnerable.
There doesn't seen to be a patch ready, and mitigations are the only defense. Microsoft offers this guidance:
- "Add users to the Protected Users Security Group, which prevents the use of NTLM as an authentication mechanism. Performing this mitigation makes troubleshooting easier than other methods of disabling NTLM. Consider using it for high value accounts such as Domain Admins when possible. Please note: This may cause impact to applications that require NTLM, however the settings will revert once the user is removed from the Protected Users Group. Please see Protected Users Security Group for more information.
- Block TCP 445/SMB outbound from your network by using a perimeter firewall, a local firewall, and via your VPN settings. This will prevent the sending of NTLM authentication messages to remote file shares."
A remote admin could use remote desktop to access their domain controller and then make changes in Active Directory Users and Computers (ADUC). Read this guide to understand more about how the Protected Users security group works. It would then only be a matter of adding members through group properties.
OR use JumpCloud's PowerShell interface:
Get-ADGroup -Identity "Protected Users"
Get-ADGroup -Identity "Protected Users" | Add-ADGroupMember –Members "CN=Test,CN=Users,DC=Test1,DC=com"
Get-ADGroupMember -Identity "Protected Users"
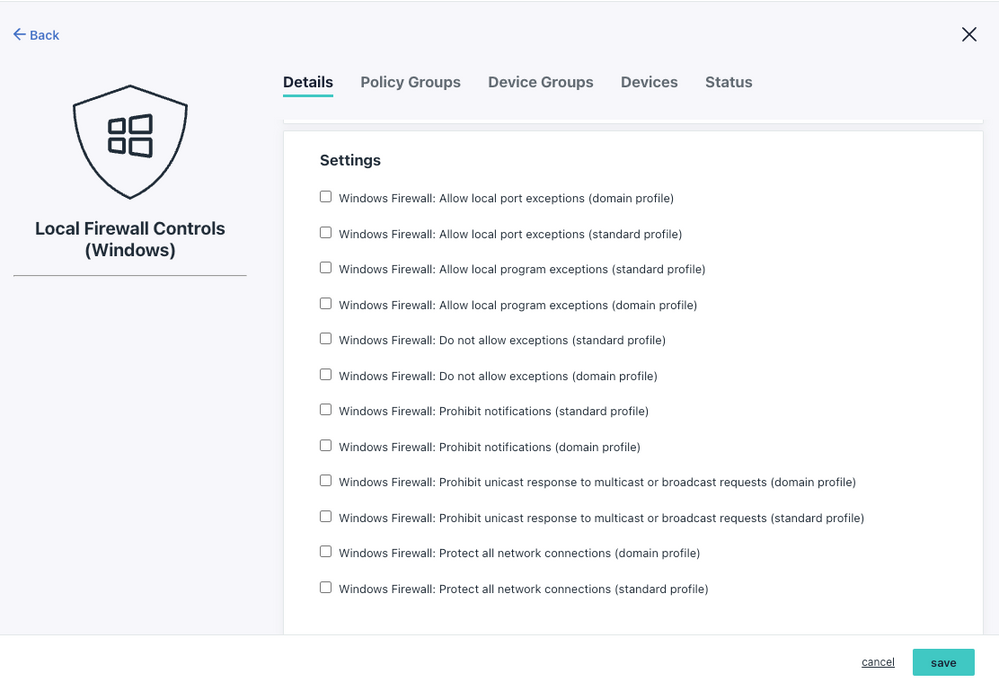
You can manage SMB traffic with guidance from your firewall vendor / network admin. JumpCloud also provides a point-and-click policy for Windows Firewall settings:
PowerShell is another option:
New-NetFirewallRule -Name "AllowSMB" -DisplayName "Allow SMB" -Enabled True `
-Profile Domain -Direction Inbound -Action Allow -RemoteAddress YOUR IP RANGE `
-Protocol TCP -LocalPort 445 -Program System
Mitigations are great options for security protection and they can provide faster protection to limit uncertainty. Don’t just sit there waiting for a patch, use (JumpCloud) commands to implement a mitigation after you weigh the potential impact(s). This becomes even more significant if your organization is using an un-supported OS that doesn't have any vendor patch forthcoming.
New to the site? Take a look at these additional resources:
Ready to join us? You can register here.