Federated Authentication is Here!
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2024 05:36 PM
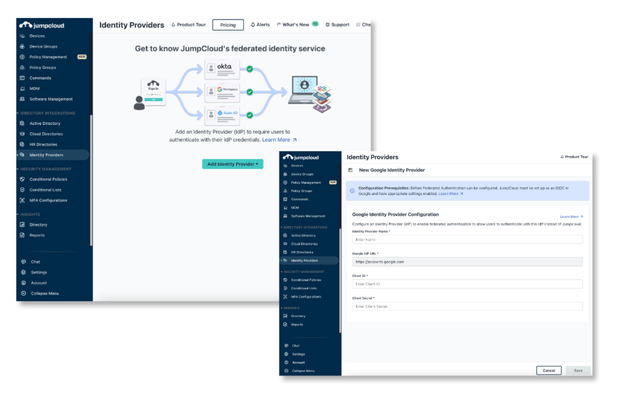
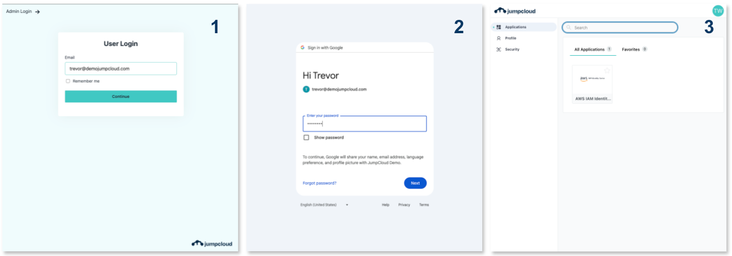
Today we launched Federated Authentication into General Availability! Configure Google, Entra ID, or Okta as a trusted external Identity Provider (IdP) to allow users to login with these IdPs to access JumpCloud resources.
What is it?
Federated Authentication allows you to configure a trusted, external IdP as a source of User authentication in JumpCloud. Users maintain all their group, device, and directory associations, but authenticate with a trusted IdP.
Key Capabilities
- OAuth OIDC authentication: Users login with a trusted OIDC provider such as Google, Entra ID, or Okta. This login takes place within the context of the external IdP - JumpCloud never sees the user’s password or any other secure credentials they may use during authentication.
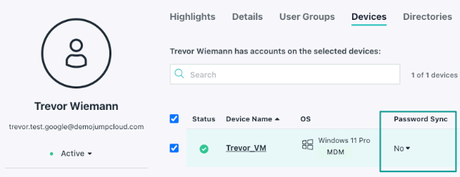
- Local device account passcodes: When you bind a user to a device, a corresponding local account is either created or taken over on the device. When this happens, the JumpCloud password is also set on the local account - the power of JumpCloud device identity! However, there may be cases where you want device identity (user bound to the device) but not to sync a password to the device - we’ve added this option! Disabling the device password sync means the user will have a local passcode on the device. This passcode is not synced with JumpCloud. On Windows, we leverage a PIN. On Mac, it’s a password. Regardless, the passcode is local to the device, and never is sent to JumpCloud.
- Self-Service Account Provisioning (or ADE) with a Federated Login: Users can login with an external IdP to provision a new account to a Windows or Mac device!
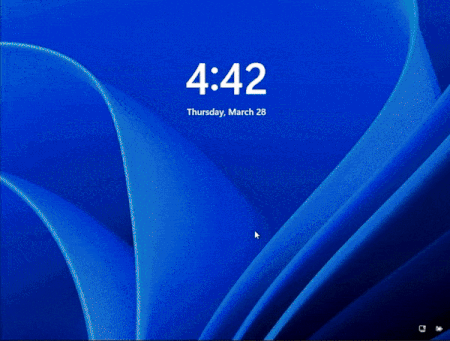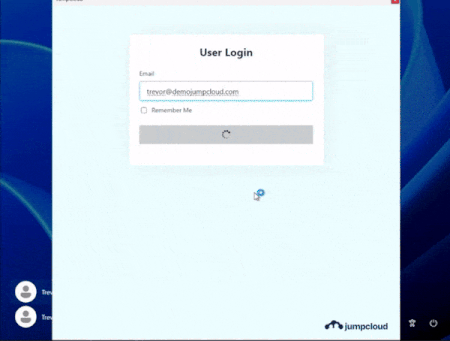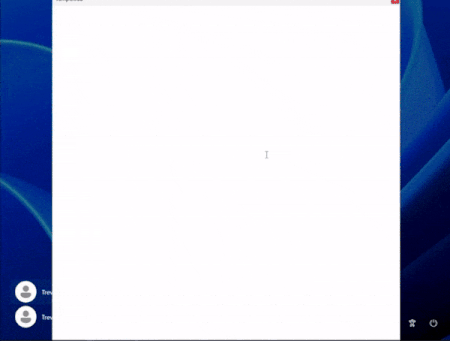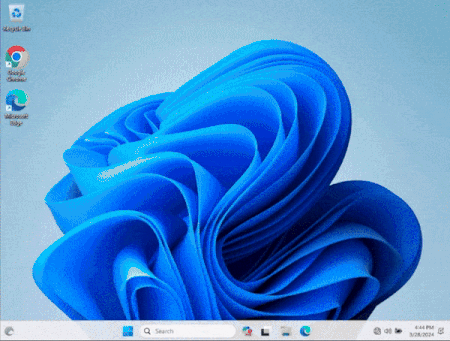
- Local Passcode Resets: When Device Password Sync is disabled, users may reset their local credential from the login window! Using the Sign in with JumpCloud option on Windows, or the Forgot password option on Mac, users may login with their IdP to reset their local device account password.
- Access User Portal and SSO applications with an external IdP: The trusted external IdP may be used for User Portal and SSO application authentication! Users login the same way they would with JumpCloud, but when an external IdP is applied, the login will be redirected to the associated IdP.
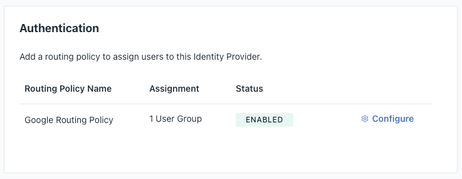
- Routing Policies (Group Binding): Routing Policies for IdPs allow you to bind User Groups to the IdP! Only users in these bound groups will login with the associated IdP. All other users will login with JumpCloud.
- Externally Managed Passwords: Users that login with an external IdP likely do not need passwords in JumpCloud. After configuring an external IdP, you may set a user as having a Password Authority of that IdP to prevent user password changes in JumpCloud. Once set, any password changes from the device tray app, User Portal, or reset password flows will be denied.
- Flexibility in how you integrate with JumpCloud: JumpCloud has long supported deep cloud directory integrations with both Google and Entra ID, including inbound and outbound provisioning. Before now, these integrations did not support authentication into JumpCloud. Today, you may choose to configure these directories as IdPs in JumpCloud, enabling inbound user authentication.
Support Resources:
Labels:
0 REPLIES 0