Patch Dashboard - Part 2 Taking Actions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2023 04:28 AM - edited 08-14-2023 04:32 AM
Hey Folks,
Hope you had a great summary holiday - says a guy lives on a sunny island with eternal summer (minus the holiday, of course) 😂.
Apologies for the delay. Let’s dive back into our topic.
Since we gained the overall patching visibility in part 1, it's time to take action on those outdated systems.
Get Started
TL;DR
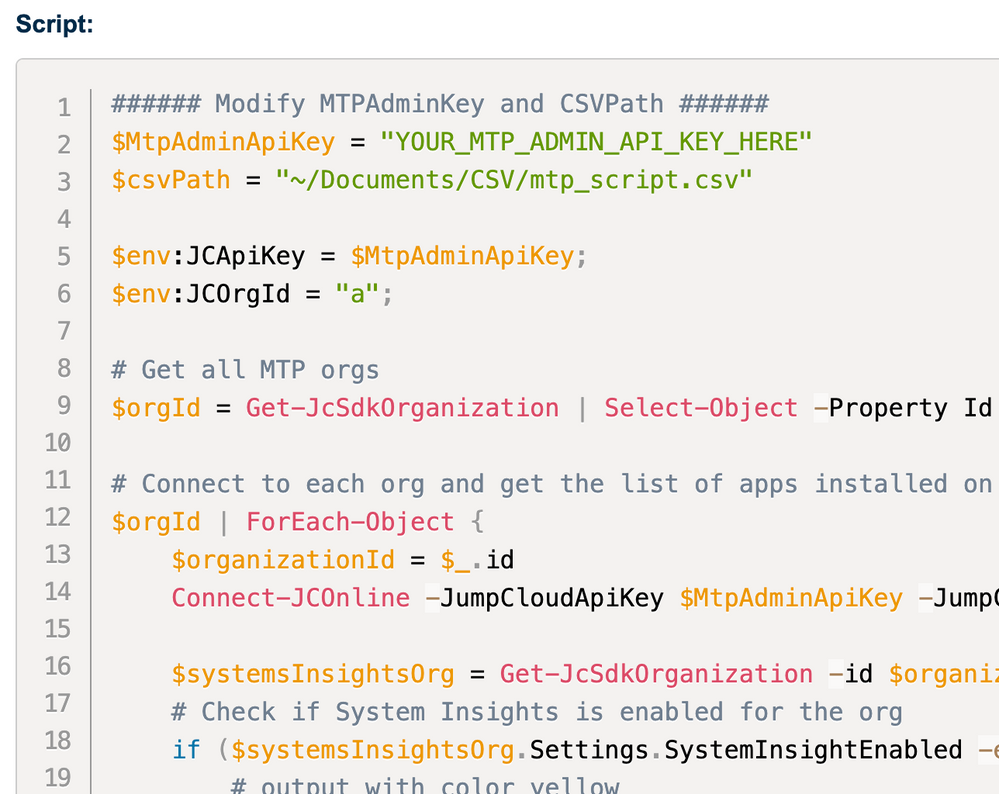
Get the script here - this time, it’s PowerShell 😀.
The idea is - create a group for the outdated systems, attach the patch policies, and let the enforcement take over.
Requirement
- Powershell 7+
- Jumpcloud powershell module
- OS: MacOS, Windows, Linux
- Use an API key from a JC admin with at least JC manager permission.
- Create or get the most aggressive patch policy IDs for respective OSes.
A Quick Manual
- Fill in the path of the outdated systems csv you downloaded from Step 2, in line 17:
$outdatedSystems = Import-csv "/the-path-to/outdatedSystems-2023-08-14.csv" # The CSV exported from Patch Dashboard step 2 - Fill in the API key in line 15:
$apiKey = '' # Your JC manager admin API key - Fill the policy IDs in line 20 ~ 22:
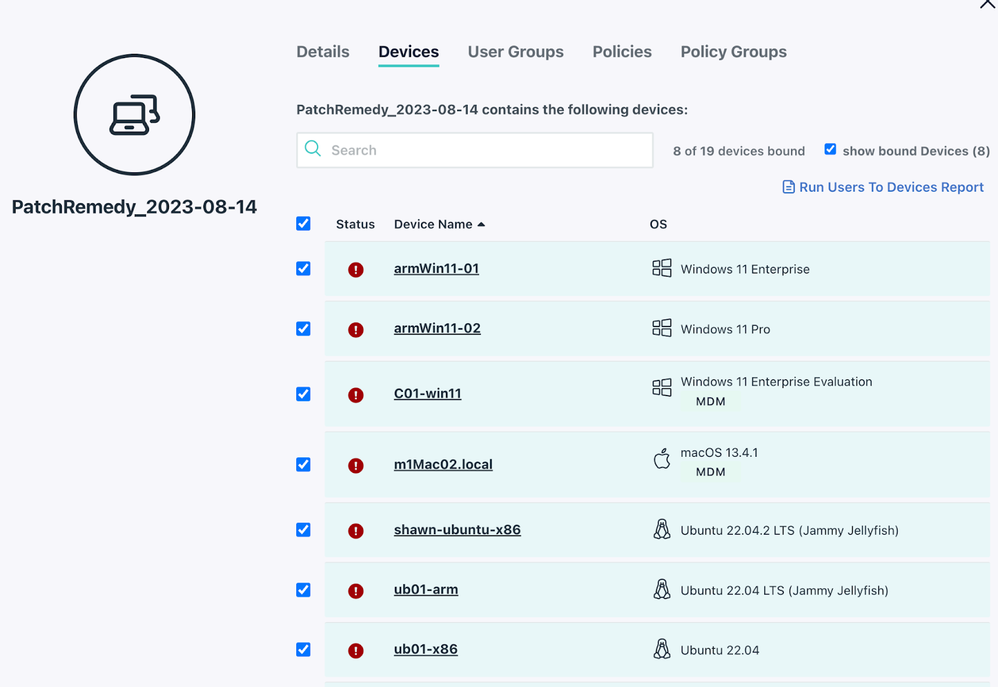
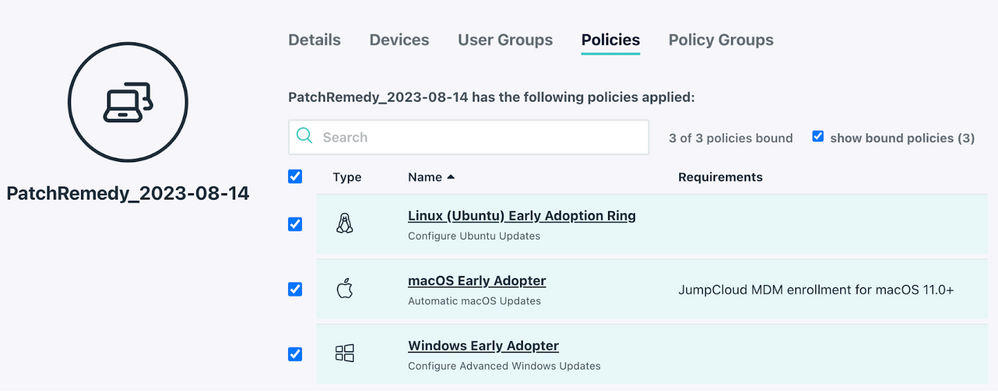
# Create or provide the most agressive patch policy IDs for respective OSes $winPolicyID = 'winPolicyID' $macPolicyID = 'macPolicyID' $linuxPolicyID = 'linuxPolicyID' - Run the script! You should be able to see a new group created with outdated devices added, and the patch policies attached:
- Done! You can rerun the dashboard report after a few days or so to check in, if all good, feel free to disband this group.
P.S. If there are “long-term residents” lingering after a period (typically 7+ days), consider using JC cmd for targeted-enforced updates. I highly recommend reaching out to the end user before taking action to avoid potential disruptions when the device reboots. For example:
- Using Get-WindowsUpdate module on windows.
- Use the MDM cmd to schedule an update on MacOS.
- Run “apt-get update && apt-get upgrade” on Ubuntu.
I’ve kept this part manual as the user communication is crucial - We definitely don't want unexpected device reboots in the midst of important tasks.
And that’s it folks, have a great start of your week!
- Labels:
-
API
-
PowerShell