LAPS for Windows aka "JC miniLAPS"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2022 03:25 AM
Why is it called 'JC-miniLAPS'?
To-Do (under consideration):
The script can be found here.
- Labels:
-
API
-
PowerShell
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 12:47 PM - edited 05-31-2023 04:57 AM
Hi Juergen,
my case is "SystemContext-API isn't available", even if my test pc has been migrated from AD domain using the Jumpcloud ADMU. I'm not very good as a programmer, but how can I modify the script to use for example the API key or enable the SystemContext-API ?
Thanks a lot
Dario
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2023 08:50 PM
Hello @dariovernelli
It's doable without SystemContext-API as well, but be clear about the fact that this carry - in some form - an API-key in the scripts. If that's ok with you?
I'll put this on my bucket list to make an alternative version.
Allow me some grace period as I'm going to travel as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2023 08:44 AM
yes I know the "risk" of an API-Key into the script, but it will be very useful for me.
Thanks a lot
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2023 10:58 PM
Hey @dariovernelli
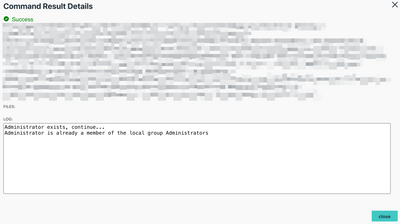
So, I got a couple of minutes to look into it and it's basically a minor change as you only have to change the last section where we're making the actual call against the API to set the password into the description field.
The initial version using the SystemContextAPI looks like this:
# Line 436 onwards:
# Invoke the WebRequest via API to writhe the password into the description of the device
$headers = @{
Accept = "application/json"
Date = "$now"
Authorization = "Signature keyId=`"system/$($systemKey)`",headers=`"request-line date`",algorithm=`"rsa-sha256`",signature=`"$($signature)`""
}
$Form = @{
'description' = [System.Runtime.InteropServices.Marshal]::PtrToStringAuto([System.Runtime.InteropServices.Marshal]::SecureStringToBSTR($LAPS_password));
} | ConvertTo-Json
Invoke-RestMethod -Method PUT -Uri "https://console.jumpcloud.com/api/systems/$systemKey" -ContentType 'application/json' -Headers $headers -Body $Form | Out-Null
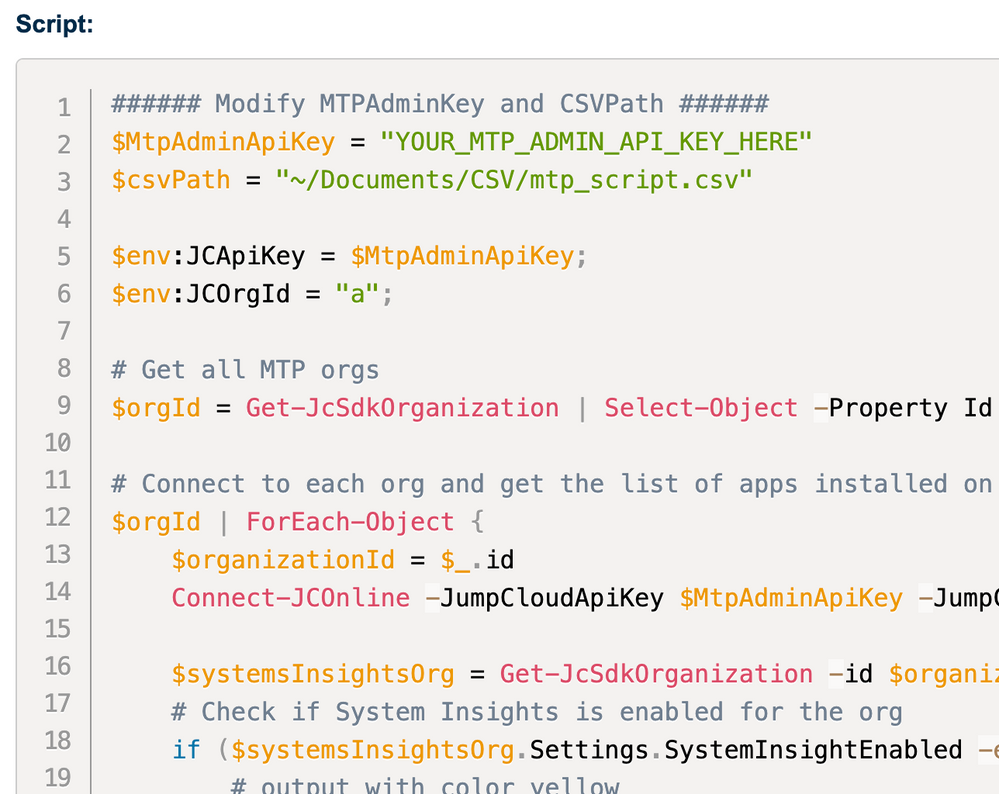
We're going to replace this with the following changed code using the API-Key:
# Replace "YOUR_API_KEY" with your actual JumpCloud API key
$apiKey = "<YOUR_API_KEY>"
$now = (Get-Date -Date ((Get-Date).ToUniversalTime()) -UFormat "+%a, %d %h %Y %H:%M:%S GMT")
# Set up headers for the request
$headers = @{
Date = "$now"
'x-org-id' = ""
'x-api-key' = $apiKey
'content-type'= "application/json"
}
# Convert password to string and create JSON body
$Form = @{
'description' = [System.Runtime.InteropServices.Marshal]::PtrToStringAuto([System.Runtime.InteropServices.Marshal]::SecureStringToBSTR($LAPS_password));
} | ConvertTo-Json
# Invoke the WebRequest via API to write the password into the description of the device
Invoke-RestMethod -Method PUT -Uri "https://console.jumpcloud.com/api/systems/$systemKey" -ContentType 'application/json' -Headers $headers -Body $Form | Out-NullI've put the whole script (taken out unnecessary code and the lengthy description) on my GitHub here.
I did 2-3 tests on my Windows Boxes and it worked fine.
A potential improvement could be to obfuscate the API-key in one or another form. (thinking about options).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2023 11:35 AM
Hi @JuergenKlaassen ,
many thanks. I'll try asap.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2023 04:46 PM
We were discussing this recently. Love this post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2023 03:49 AM
Would it be possible to store the password on a shared folder in JumpCloud Password Manager?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2023 10:55 AM
I've done that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2023 10:03 PM
Do you mind sharing a script for that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2023 11:50 AM
Hi! Do you have the script for macOS? Or do you plan to implement it?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2023 04:46 AM
Hi Thomas
macOS is quite a 'different beast' here.
There's an open source project: https://github.com/joshua-d-miller/macOSLAPS/wiki/
I haven't dug in deeper yet on it though.
Is this something you could consider?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2023 02:08 PM
Sure!
It would be great to take advantage of the fact that JumpCloud installs an agent on all computers to resolve this LAPS requirement on both Windows and Macos natively to the JC console. Just a recommendation.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2023 01:56 AM
Totally agree, Thomas
Always good to have Feature Requests. I encourage everyone interested to file such.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2023 08:12 PM
Hi Juergen,
Do you have an updated script to store the password on other location aside from putting it on the Device Description. Sometimes people are provided with Read Only API on the platform and would gain access to those passwords via the Device description. Maybe storing them on a shared folder on JC's Password Manager?
Cheers!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2023 01:59 AM
Hey
Agree, it can be problematic to have it in the description field or any other rather unprotected one.
I'd love to be able to store it in the PWM, unfortunately there's no API or CLI available for this yet.
Also screams "Feature Request" 😉
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2023 02:12 AM
Hi Juergen,
Appreciate you taking the time to respond.
Yeah it would be great if they can include it on the roadmap soon. Other than the description field any other channels (JIRA maybe) that we might be able to do with the current feature?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2023 02:27 AM
🤔
Now you got me thinking.
Instead do writing it into the description field, it shouldn't be a crazy deal to make an API-call to Jira for example. (depending a bit on the version, hosted vs cloud).
What do you use?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2023 03:44 AM
We are using the Cloud. The from JIRA we can have it stored on other channel. Just getting it from JC to JIRA would be nice. 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2023 10:22 AM
Best you could do, perhaps, is store in a secure note in a shared folder in PWM, but like Juergen said, no API to access it. But at least you could share it securely that way.
Like someone's post? Give them a kudo!
Did someone's answer help you? Please mark it as a solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2023 07:10 PM
Yup, had a word with JC reps and PWM API is underway maybe 1st Q of 2024 and hopefully this would be included on the first phase of the roll out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2023 02:58 PM
This would be amazing in PWM! Good stuff in this thread!