- JumpCloud Community
- IT Topics
- Security & Networks
- How to Leverage JumpCloud MDM for macOS Device Tru...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to Leverage JumpCloud MDM for macOS Device Trust Policy in Okta
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2023
09:06 AM
- last edited on
06-07-2023
04:06 PM
by
![]() BScott
BScott
![]()
Prerequisites
- JumpCloud MDM
- Okta MFA package
- Okta identity Engine
Motivation
There are several ways to enhance the security level of Okta SSO access. This article presents enabling Device Trust (devices must be managed) as an additional authentication factor within Okta FastPass.
Follow the step below to implement a device trust policy for Okta SSO access on JumpCloud-managed devices.
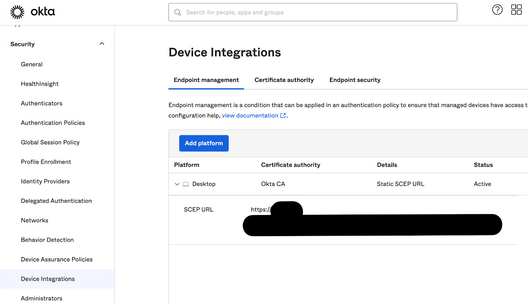
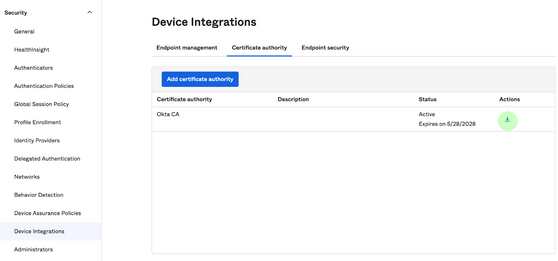
- Configure Okta as a CA with static SCEP
Follow tasks #1 and #2 from this Okta Help article. - Prepare a custom SCEP profile for macOS. In this article, we’re going to use iMazing.
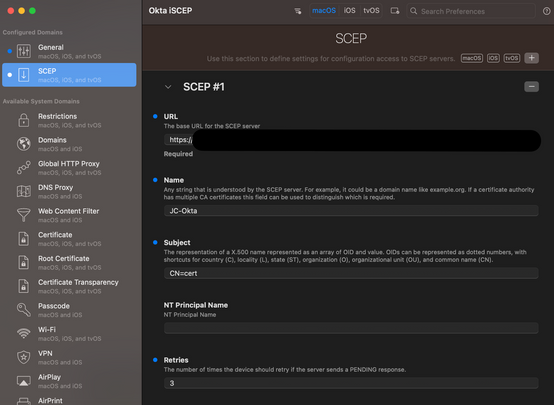
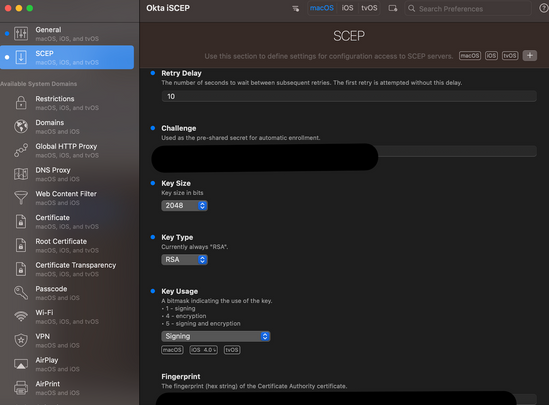
Open iMazing Profile Editor and set up a profile with the following parameters:
URL: copy Okta Admin Console > Security > Device Integration
Name: Define the name of the profile
Subject: Okta does not require the subject name to be in any particular format. Choose a name that indicates
that the certificate is used as the device management signal to Okta. The default can be set to CN=cert
Retries: 3
Retry Delay: 10
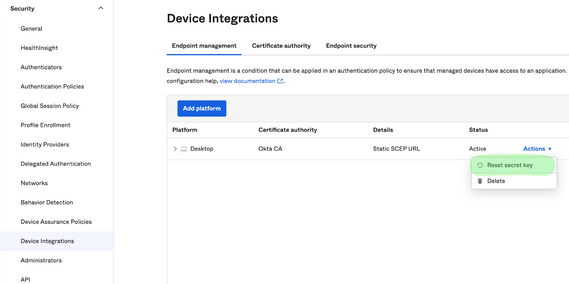
Challenge: paste the Secret Key you generated when configuring the CA with SCEP (step #1). The secret
can be reset
Key Size: 2048
Key Type: RSA
Key Usage: Signing
Fingerprint:
- Download the root CA from Okta
- Retrieve the certificate fingerprint - for example by openssl in the terminal on macOS: openssl x509 -noout -fingerprint -sha256 -inform pem -in cert
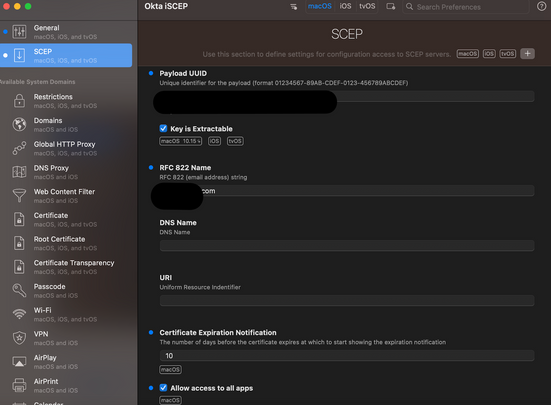
RFC 822 Name: this is a subjectAltName value which is not a mandatory component in this case - define a generic email address.
Certificate Expiration Notification: type a number (of days)
Tick the Allow access to all apps box
The SCEP profile in the iMazing Profile Editor should look like this:
3. Save the profile and deploy it by a Mac MDM Custom Configuration Profile Policy
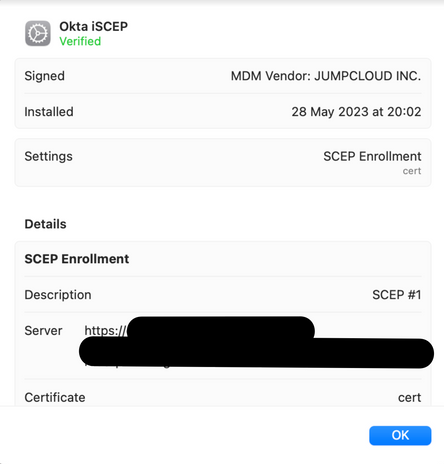
The profile on the device side should look like this
💡Once the devices obtain Okta certificates, they're recognized as "managed", which allows Okta to
restrict SSO access for JumpCloud-managed devices
4. Distribute Okta Verify app to the macOS endpoints by JumpCloud Software Management for Mac (or install
manually)
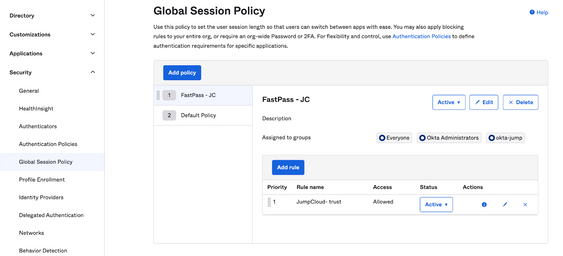
5. Configure a Global Session Policy for Okta FastPass
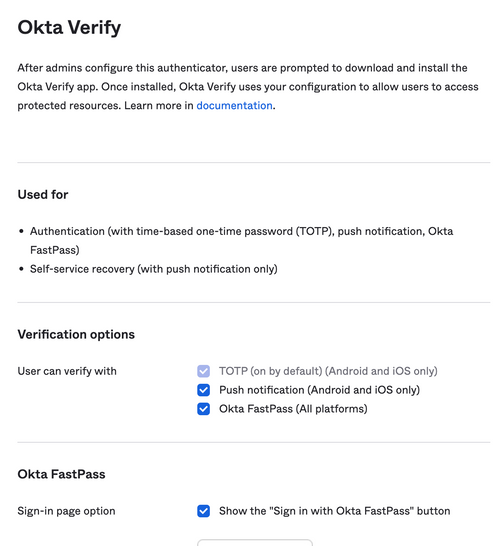
6. Enable Okta FastPass as an eligible authenticator
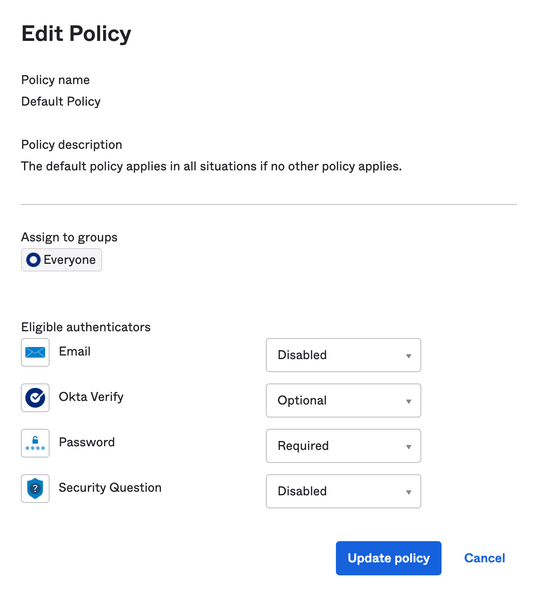
❗Note: for initial testing, Okta Verify authenticator can be set as Optional in the Default Policy
(Security>Authenticators>Enrollment)
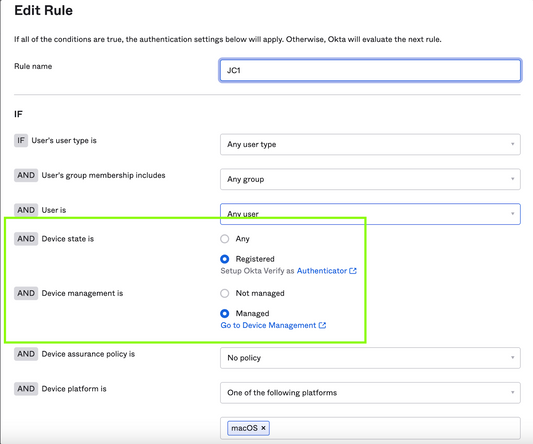
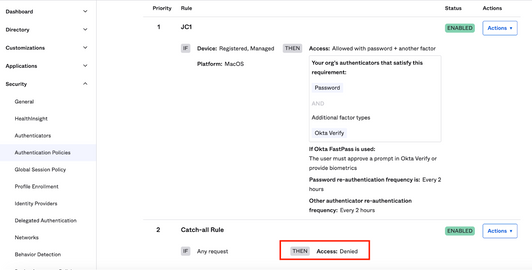
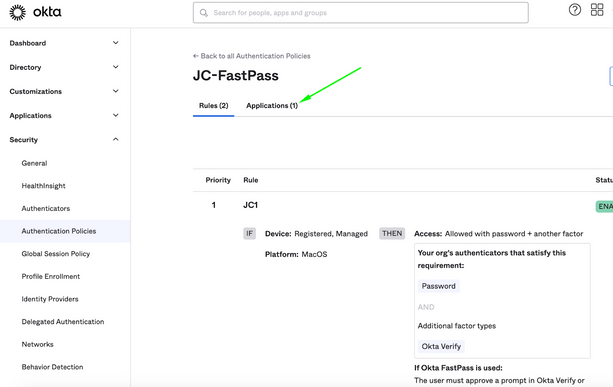
7. Configure an authentication policy for Okta FastPass
Create a rule that requires Device State is Registered AND Device Management is Managed
❗Note: once the rule is defined, devices can’t access apps by SSO if they haven’t obtained the certificate
JumpCloud MDM or installed the Okta Verify agent. We recommended assigning the rule to test Application
and verifying the functionality before wide rollout.
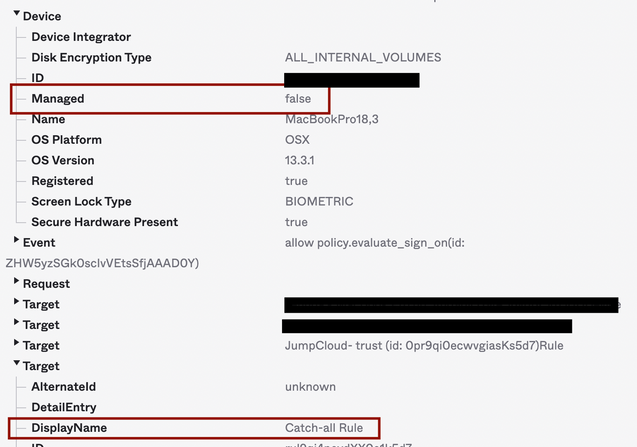
Important: Set Access: Denied in the default catch-all rule
💡Tip
The initial testing can be performed with Catch-all Rule in the "Allow" state so the following log fragment can
predict that access would be denied on unmanaged devices with catch-all rule in the "Deny" state.
Assign Applications
8. Try Connecting the desired Web App by SSO
Okta Verify will require registration according to the policy
9. Check the Authentication Log
Okta Admin Console > Reports > System Log
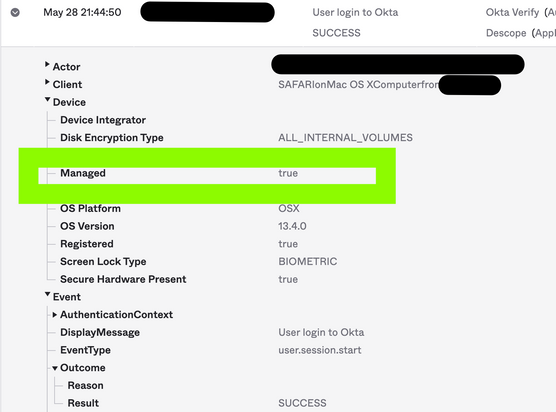
For example, search successful events by eventType eq "user.authentication.sso"
SUCCESS log with managed devices
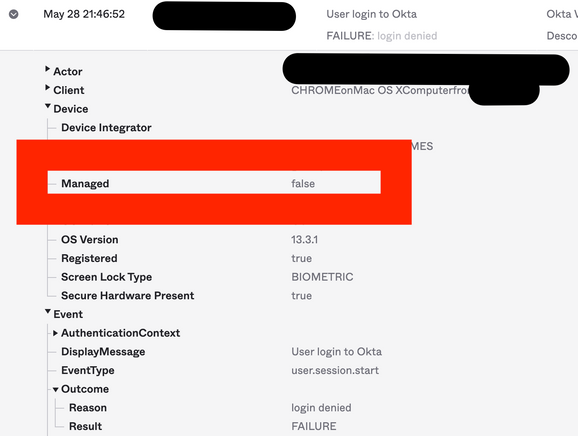
For example, search “Access Denied” events by outcome.result eq "FAILURE"
FAILURE log with unmanaged devices
Authentication FAILURE on an endpoint
- Labels:
-
Identity and Access Management
New to the site? Take a look at these additional resources:
Ready to join us? You can register here.
- JumpCloud SSO x CloudFlare Access Policies (Zero Trust) in Best Practices
- Claris Filemaker Pro OIDC connection...anyone done this? in Best Practices
- Okta Device Trust with JumpCloud via SCEP in Best Practices
- Phased IAM migration from Google to JumpCloud in Best Practices
- Okta Device Trust with JumpCloud - MacOS & Windows in Best Practices