March ’23 JumpShot: Product Edition
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2023 06:44 PM - edited 03-09-2023 06:49 PM
March ’23 JumpShot: Product Edition
This month's JumpShot featured new authentication, compliance, and administrative capabilities that will improve the security of your users and resources and make admins more productive. These new features deliver stronger passwords, higher integrity for devices as a gateway to IT assets, and more satisfaction for end users. Read on to learn more about these advancements.
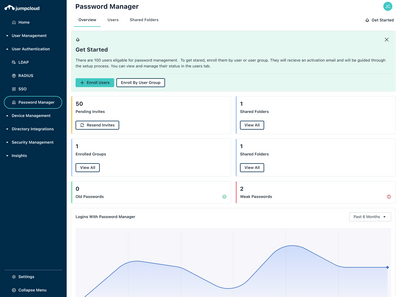
Password Manager Health Check
Admins now have even more visibility into the overall health and security of users’ passwords. This provides password protection and assurance that users are implementing high quality passphrases. See info on password complexity, age, repeated use, and shared status via the dashboard widgets and Directory Insights. [Learn More]
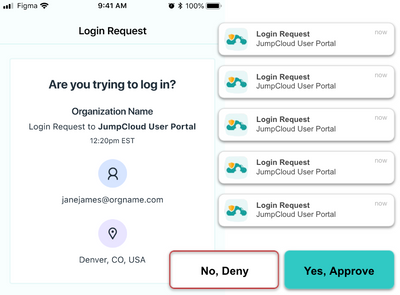
Push Bombing Mitigation
Devices are the gateway to your resources and attackers are leveraging potential MFA fatigue through push bombing attacks that can mislead users into authenticating. JumpCloud now supports rules to limit the number of push MFA user attempts for a resource or endpoint. This release will secure cloud applications and the User Portal, Mac, Windows, and Linux desktops, and SSH and Windows RDP login. [Read The Article] Push bombing mitigation is in Early Access. If you do not see it, contact your Account Manager for more details. JumpCloud disclaims all obligations or liabilities with respect to it. Please review your agreement for more details.
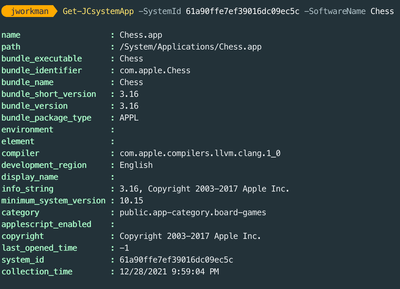
New PowerShell Function: Get-JCSystemApp
A new JumpCloud PowerShell Module helps admins easily gather information on what software (and which version of it) is on their systems. You can filter by systemID, systemOS, softwareName, and softwareVersion. This helps with compliance when it’s necessary to know what apps are installed on your endpoints. [Read The Community Post]
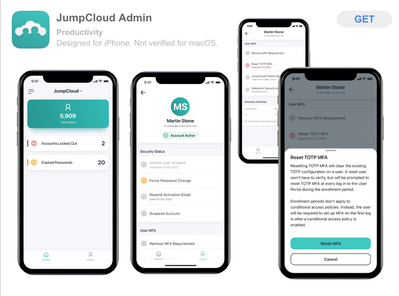
JumpCloud Admin Mobile App for iOS & Android
The brand new JumpCloud Admin mobile app helps admins resolve issues on the go. Unlock a user, reset passwords, and remove MFA registration, all without having to access the desktop console. [Read The Support Article]
- Labels:
-
Product News