- JumpCloud Community
- JumpCloud
- Demo Walkthroughs
- Create an SSO Application
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Single sign-on (SSO) eliminates identity silos and ensures that your security posture is consistent and access decisions are made around each asset/endpoint. SSO also makes it more convenient for your users to access the apps and resources that they use every day. We’re going to show you how to configure an app with the option to try Conditional Access.
The combination of those security features helps to ensure that access is only granted to authorized users. JumpCloud provides several options for MFA, including JumpCloud Go, push MFA, and TOTP. It’s a zero trust approach to security, and it’s not difficult to manage. This walkthrough demonstrates the work that’s involved and the user experience once it’s set up.
Keep in mind that JumpCloud doesn’t charge extra for the ability to make custom apps and accepts requests for AuthN and AuthZ configurations, using SCIM provisioning for the latter.
Prerequisites
Not every step here is necessary to complete this tutorial. However, if you want to experience your evaluation of this (and other) feature as if you’re implementing the product, we recommend the following:
- To complete this tutorial, we recommend that you have completed the following walkthroughs (or have set up your instance with the appropriate assets on your own):
- Creating JumpCloud Admins
- Creating Users 101
- Creating Groups 101
- Have MFA pre-configured for testers (optional for Conditional Access)
Demo Walkthrough
JumpCloud provides nearly 1,000 pre-built apps to make it easy for admins to extend SSO to resources. We’re going to use RSA’s Test Service Provider to have a SAML service available to work. It’s not in the catalog, because it’s for testing purposes only.
No production app is necessary, and doing this won’t affect any of your users.
We’ll set up a custom app in JumpCloud. It’s a simple process, and will only take about 10 minutes when you’re ready. Pro tip: you can add a Conditional Access policy to the app for mandatory MFA for extra security that is key to achieving a zero trust strategy.
It just takes a moment, and will help you understand the JumpCloud platform from day 1.
Step 1: Gather Service Provider (SP) Metadata
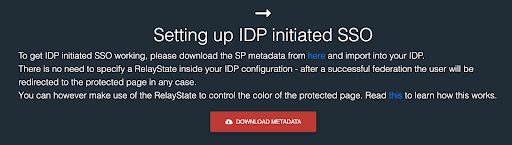
RSA’s instructions are to download its metadata for your Identity Provider (IdP) to consume. That eliminates manual data entry where mistakes can be made. It’s typically a first step to download metadata from the SP to configure the connector in JumpCloud.
Metadata is available from the SP we’re using for this walkthrough.
Resources:
How To Test SAML And Configure SSO For Free
Step 2: Create an App and Add the MetaData
Create the App
- Click SSO Applications in the left pane
- Click on the ( + ) icon to add an app
- You’d typically search for a pre-built app, but we’ll click on Select under “custom application” in the bottom right row of Featured Applications.
- Click Next and then select Manage Single Sign-On (SSO). SAML will be selected by default, so just click next.
- Name it and add a description and then it Next. Feel free to customize its look and feel.
- Save the application and then move on to Configure Application.
Keep in mind that the manual steps that follow aren’t usually necessary to create an SSO app. Pre-built apps do all of the heavy lifting. We’re doing it this way to avoid using production apps for this walkthrough. You can also learn about how this process would work with a pre-built app.
Import the SP Metadata
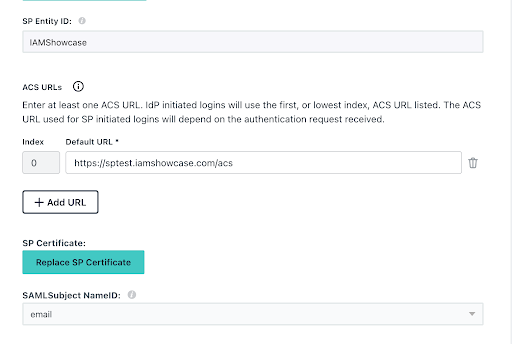
Upload the XML file that you downloaded from RSA.
That step will populate key fields and map the attributes.
Just type in an IdP Entity ID before clicking save and moving on to the next step.
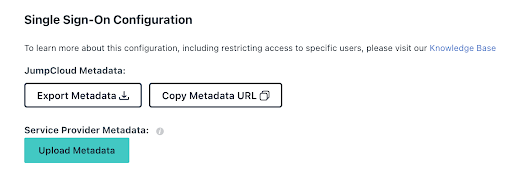
Exporting the IdP Metadata
Click Export Metadata to save the IdP information RSA will need.
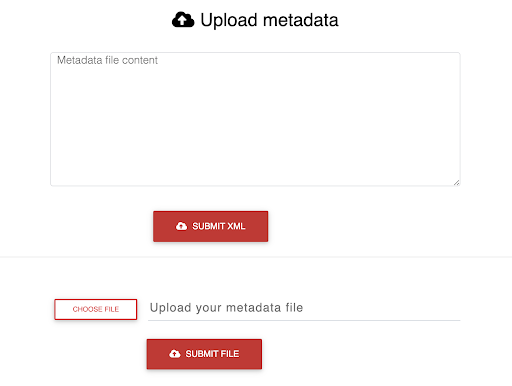
The RSA Demo has a field to upload it.
RSA will upload the IdP metadata and provide you with a URL to save (but you really won’t need it for this walkthrough). You’re almost ready to move on and try the app out.
The final step is:
- Navigate to the User Group tab and add the test group to the app. That will populate the User Portal with the RSA test app when they log into JumpCloud.
Resources:
Configuring a SAML Application
Connect Apps with Pre-Built Connectors
Step 3: Access the App as a User
You may load an incognito Window to simulate the user experience.
- Log into the User Portal as an authorized test user
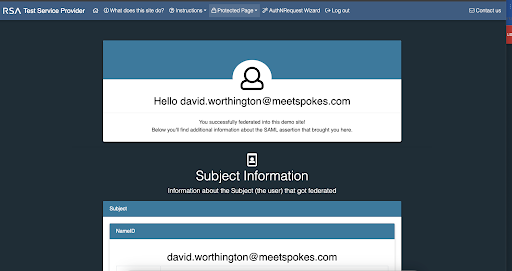
- You’ll see the RSA app; click it, and you’ll be taken through the log-in process.
This confirmation screen will be displayed if it all goes well.
Resources:
Bonus Simulations
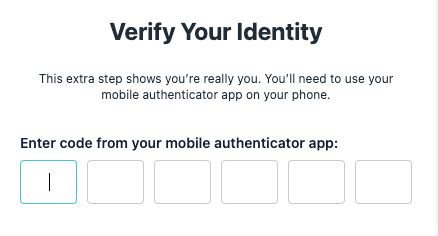
Let’s add a Conditional Access policy that will force users to authenticate when they access the app. We’ve linked to the walkthrough for that, but you can also see how it’s done with a simulation: https://university.jumpcloud.com/courses/conditional-access-sso-applications
Have authorized users access your app; they’ll be prompted to use MFA.
This step is important for privileged access, but consider doing it for all of your apps.
Final Results
You’ve learned how to set up a custom SSO app. Centralizing access control takes full advantage of JumpCloud’s integration of identity/access management and cross-OS device management. Your resources will be secured, and users will become more productive.
Get prepped now
Set up JumpCloud Password Manager
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
New to the site? Take a look at these additional resources:
Ready to join us? You can register here.
- Windows MDM CSP Policies V2 in JumpCloud Product News
- Secure Admin Portal with higher authentication assurance MFA methods - Now GA and Live ! (01/06/25) in JumpCloud Product News
- GA of Device Monitoring and Alerting is here! in JumpCloud Product News
- JumpCloud SaaS Management: Adding SaaS Apps Manually in JumpCloud Product News
- A Brand New Device List Experience! in JumpCloud Product News