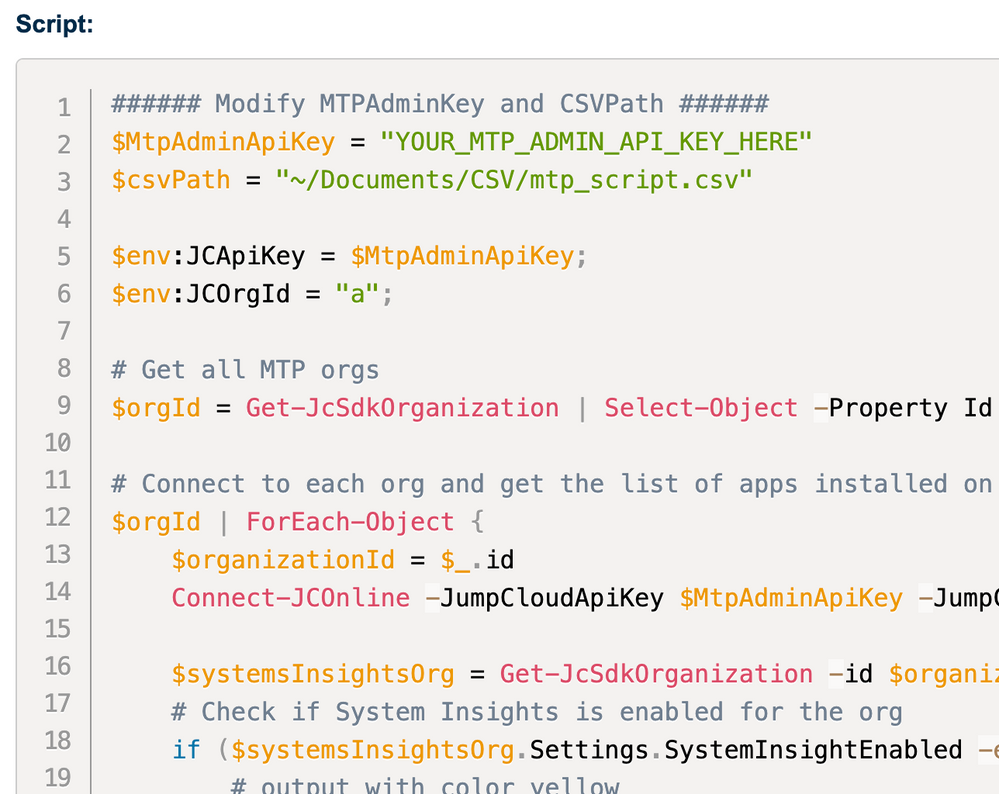
[PowerShell] How to scan for vulnerable applications? "JC - Get Vulnerabilities for an installed Application.ps1" is here for you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2024 03:54 AM - edited 01-17-2024 03:57 AM
Hi Community Folks
Over the festive season I pondered a bit more about the possibility to scan a JumpCloud managed environment for application vulnerabilities.
The National Vulnerability Database by NIST provides an API to make queries against it and you'll need an API-key for that if you want to make use of this script. Get one here, no worries: it's free
I made experiments with direct REST-API-calls via Powershell, but wasn't satisfied as the usage isn't that straightforward actually - or at least not without putting much more time into it first.
What I found then is a fairly new PowerShell Module for the NVD written by Dan Gough (big kudos for that!) and you can find the module here - you'll need that as well when using this script.
That said, you're requirements are the following:
- JumpCloud API-Key (Read-only will do)
- This script
- NVD API Key
- Posh-CVE PowerShell Module
- JumpCloud PowerShell Module
Now you have all the ingredients already and your good to go.
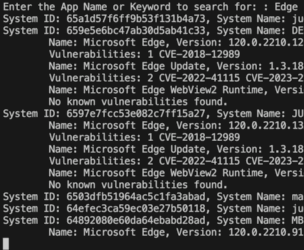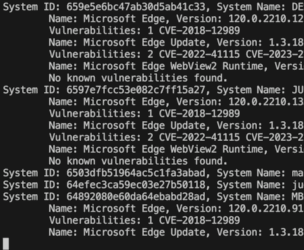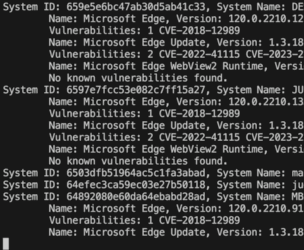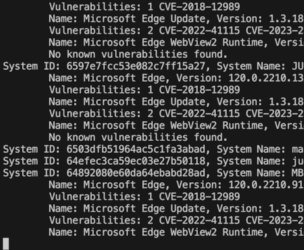
What the script will do is:
- Prompt for an application name, i.e. 'Edge', 'Chrome' or 'Microsoft Outlook'
- it then iterates through all systems by using 'Get-JCStystemApp' and 'Get-JCSystem'
- it makes a keyword search against the NVD DB using the PoshCVE-module
- it creates a table with all found vulnerabilities
- ... and finally writes the results into a CSV file for further consumption.
You can modify the columns to your needs and add/remove as needed.
if ($vulnerabilities) {
Write-Output "`tVulnerabilities: $($vulnerabilities.Count) $($vulnerabilities.CVE)"
foreach ($vuln in $vulnerabilities) {
$vulnerabilityData += [PSCustomObject]@{
CVE = $vuln.CVE
Score = $vuln.CVSSv3Score
Severity = $vuln.CVSSv3Severity
Description = $vuln.Description
OS = $os
SystemID = $systemId
Hostname = $hostname
}
Is it failsafe?
No, it's not. I did a bunch of tests and they were pretty satisfying so far, but yes, you will have false positives etc.
It's a good start to get a picture and more actionable visibility. For example you can make use of this when there are Zero-Days in the wild like this one for Google Chrome.
- Labels:
-
API
-
PowerShell
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2024 05:07 PM - edited 01-17-2024 05:07 PM
There were plenty of false positives with OpenVAS using an Alienvault appliance a few years back. Nothing out of the ordinary IMHO.