SSO, MFA, and Conditional Access to WarpSpeed WireGuard VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2022 05:02 PM
It was a productive day. My primary focus was setting up a SAML/SSO integration with WarpSpeed WireGuard VPN. WireGuard is a modern alternative to IPsec VPNs, simpler, faster, and very affordable for SMEs that need strong perimeter security. Let's face it, firewalls that have high throughput for VPN concentrators can be very expensive, and IPSec is confusing to the uninitiated.
A cloud directory such as JumpCloud can layer on zero trust IAM and a great user experience. My blog post is in the editing queue, but here's a sneak peak at the tutorial.
Create a SAML Connector
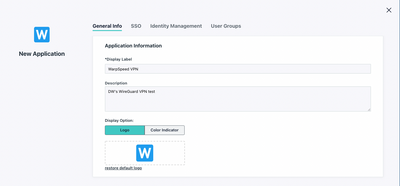
Click the SSO button in the left frame of the administrative console and hit the “plus” sign to start a new SSO connection. Select “Customer SAML App” and begin by filling in the requisite information to label your connector and choose a color scheme and logo. More context is available in JumpCloud’s SAML how-to article should you have any additional requirements.
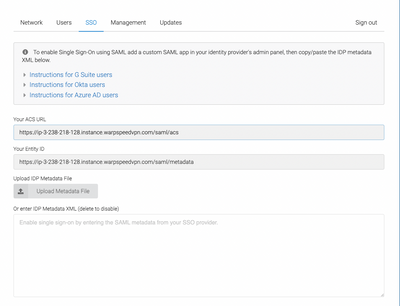
Exchange MetaData
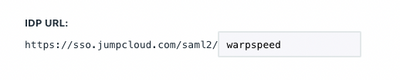
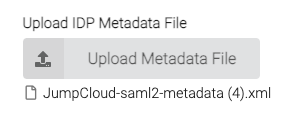
WarpSpeed only requires the IPD (Identity Provider) metadata to enable its SAML 2.0 integration. JumpCloud is the IDP in this scenario. Begin your setup by navigating to the SSO tab and enter an Entity ID that’s unique to your organization’s environment. Here’s an example:
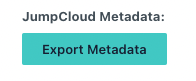
Your FQDN will be different from the one displayed above. The settings on this screen are case-sensitive on both systems; any typo will result in errors and the integration will fail. The best method is to export your IDP settings from JumpCloud.
This is the view from JumpCloud
This is the view from WarpSpeed
Your next step is to assign a group to the WarpSpeed SSO connector.
Setup Groups and Permissions
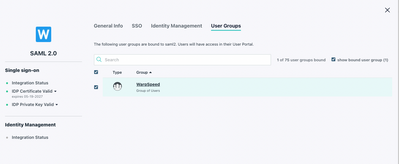
Click on the User Groups tab and add the group(s) that should have access to the WarpSpeed VPN applet. The link below is a detailed guide for admins who are unfamiliar with using JumpCloud. Note: MFA is configured on a per-user basis, unless Conditional Access is used.
Group membership grants access rights to the VPN
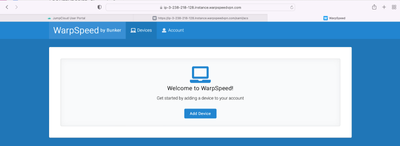
WarpSpeed VPN will be available from within the JumpCloud User Console
WarpSpeed then invites the user to register a device. SSO users won’t be admins by default.
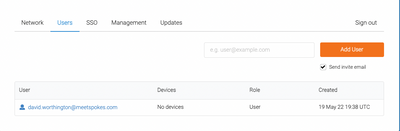
The active user will be visible from within the WarpSpeed admin console.
Add Zero Trust Security from JumpCloud
Additional Zero Trust security controls are available through JumpCloud’s Conditional Access Policies. These policies extend security beyond strong passwords and MFA alone.
Policies are assigned to existing groups or you may create dedicated groups for different sets of users. Different groups may have different policies (or no policies). Policies include:
- Geofencing: JumpCloud permits you to whitelist selected countries to access WarpSpeed. Any device that attempts to log in from locations that aren’t specified won’t be allowed. For instance, an employee who’s attempting to access internal resources from unsecured hotel Wi-Fi in a different country won’t be allowed into the VPN.
- Managed devices: This policy restricts access to JumpCloud managed devices, ensuring that rogue devices won’t be logging into your network.
- Mandatory MFA: Users must prove who they say they are prior to accessing the VPN by entering a TOTP code or Push MFA through the JumpCloud Protect™ application. This rule ensures that MFA will always be present when users login.
Tip: Retest your connectivity prior to making changes that could adversely affect user access.
- Labels:
-
General Networking