JumpCloud Managed Pritunl SSL VPN: Great Security, No Hardware
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2022 12:28 PM
Hello my friends (and you are my friends),
You may have noticed a recent post about integrating SSO and zero trust security with Fortinet. I loved my Fortis are my last job, but realize that some organizations operate within very different budgetary parameters. Pritunl is a great way to set up an SSL VPN, sans the expensive hardware (depending upon how you define expensive). You get a cloud-directory managed VPN box.
Why make you wait for the "how-to?" A full blog is in our queue, but here's the "meat". These steps focus on JumpCloud, but Pritunl has pre-built integrations for other authentication providers. The important thing is that you have good security.
JumpCloud Setup
The initial step is to create a custom SSO connector for Pritunl. JumpCloud provides hundreds of free connectors as part of your subscription, and is routinely adding more, so search for it before you move ahead with this project. Continue to the next section if one isn’t available.
Create a SAML Connector
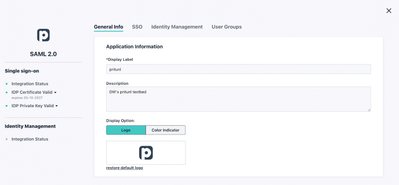
Click the SSO button in the left frame of the administrative console and hit the “plus” sign to start a new SSO connection. Select “Customer SAML App” and begin by filling in the requisite information to label your connector and choose a color scheme and logo. More context is available in JumpCloud’s SAML how-to article should you have any additional requirements.
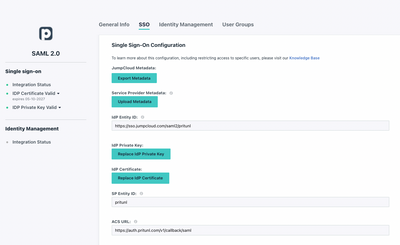
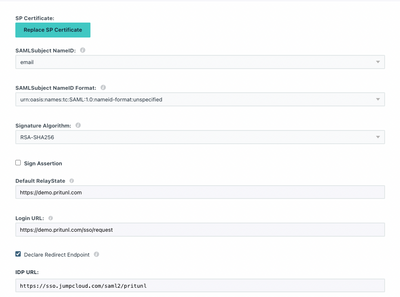
Then, navigate to the SSO tab and enter an Entity ID that’s unique to your organization’s environment. The settings on this screen are case-sensitive on both systems; any typo will result in errors and the integration will fail. Your Pritunl FQDNs and JumpCloud IDs may differ, but the fields should be formatted as outlined below:
Follow the URL/URI formats precisely
The redirect endpoint ensures that JumpCloud’s console will be used to log users into the VPN
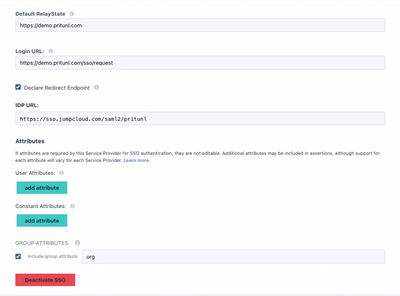
Pritunl requires the “org” attribute for group memberships
Activate the JumpCloud SSO connector once you’re finished and download the certificate. You’ll be required to copy the key into Pritunl’s GUI in a later step.
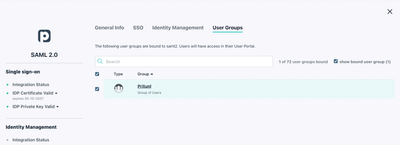
Setup Groups and Permissions
Click on the User Groups tab and add the group(s) that should have access to the VPN service. The link below is a detailed guide for admins who are unfamiliar with using JumpCloud.
Group membership grants access rights to the VPN
Pritunl VPN will be available within the JumpCloud User Console
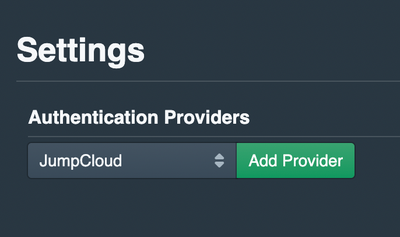
Pritunl SSO Setup
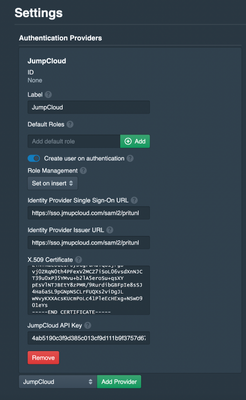
Pritunl has JumpCloud listed as an authentication provider. Pull down the list, select JumpCloud, and select “add provider” to start the process of filling in Identity Provider settings.
The settings will be identical to what you entered into the JumpCloud admin console. Cut and paste the certificate from a text editor when you open the certificate on your PC. This integration also requires a JumpCloud API key from your console, which will be outlined in the next section. Both of these entries are confidential and should be kept private and carefully controlled.
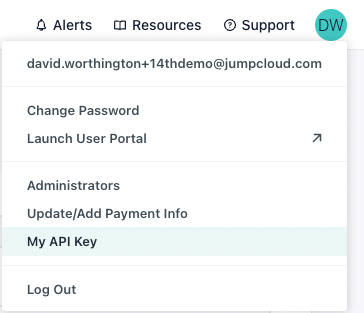
Your JumpCloud API key may be reviewed by clicking on your user icon at the top right of your console. Note: Generating a new key will revoke prior keys and could break prior integrations.
You’re now ready to test your configuration.
Add Zero Trust Security from JumpCloud
Strongly consider adding Zero Trust security controls with JumpCloud’s Conditional Access Policies. These policies extend security beyond strong passwords and MFA alone.
Policies are assigned to existing groups or you may create dedicated groups for your requirements. Different groups may have different policies (or no policies). Policies include:
- Geofencing: JumpCloud permits you to whitelist selected countries to access your VPN. Any devices that attempt to log in from locations that aren’t specified will be denied access. For instance, an employee may be attempting to access internal resources from unsecured hotel Wi-Fi while on vacation.
- Managed devices: Limit access exclusively to JumpCloud managed devices. This ensures that IAM isn’t allowing rogue devices into your network.
- Mandatory MFA: Users must prove who they say they are prior to accessing the VPN by entering a TOTP code or Push MFA through the JumpCloud Protect™ application. This extends MFA beyond initial device/session logins for additional assurance, which is advisable given the current threat landscape.
Tip: Retest your connectivity prior to making changes that could adversely affect user access.
- Labels:
-
General Networking
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2022 02:56 PM
Hey we're using Pritunl! After some hiccups in the beginning it's a pretty nice VPN so far. The only qualm I have with it, is that after the user downloads their profile to the Pritunl client, the "Mandatory MFA" doesn't activate. It only forces MFA when you log into the web UI the first time. @JCDavid did you also run into this? Or am I misconfiguring something (very possible tbh)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2022 03:35 PM
Steven,
This should help:
To set up MFA:
- Log in to the Admin Portal: https://console.jumpcloud.com/login.
- Go to SECURITY MANAGEMENT > MFA Policies.
- Enable the MFA factor you want to use in your organization. Read the JumpCloud MFA Factor Guide to figure out which type of MFA to set up.
When you create a conditional access policy that requires MFA, users who are included in the policy but don’t have MFA set up are required to enroll in MFA the next time they log in to the User Portal.
-d
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2022 11:36 PM
That's what I have setup currently 😕 A conditional policy that is "Allow authentication & require MFA". It only requires MFA when visiting the UI, not connecting via the Pritunl client. May be time to submit a support ticket?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2022 05:04 PM
Sorry this is happening. Support would be a good start to resolving your issue. I'm probably missing something that's totally obvious...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2022 09:53 AM
Hi,
I plan to implement JumpCloud SSO for Pritunl and find your write-ups very helpful.
However, I can't find that screen in 'Pritunl SSO Setup' in my Pritunl Web console. Which part of pritunl has that authentication provider settings?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2022 01:17 PM
Hello, Hendro. Thanks for your business.
Click Sign On and View Setup Instructions. Then open the Pritunl settings and set Single Sign-On to JumpCLoud and set the Single Sign-On Organization. This organization will be the default organization users are added to.
Regards,
David
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2022 08:05 PM
Thanks David,
Apparently, to use SSO, I need to subscribe the pritunl enterprise feature.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2022 01:52 PM
Not sure if you're using Pritunl for an actual company environment or just personal
From a company standpoint the $70 / month was an easy sell because my time as a SysAdmin is billed at ~$130/hour. So if the SSO saves me even 30 minutes / month on average for managing users it's well worth it. Might be an easy sell if you put it that way to your leadership!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2022 02:07 PM
I think even my former CFO would have said yes!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2024 06:48 AM - edited 12-24-2024 08:26 AM
I’ve been using JumpCloud’s managed Pritunl SSL VPN for a while, and I have to say, it’s pretty solid. The security is top-notch, and what I like is that there’s no need for any extra hardware – everything runs in the cloud. It’s easy to set up, and the interface is user-friendly, which makes managing everything a lot smoother. Plus, with the way it integrates with other services, it’s pretty flexible for most setups. If you’re worried about reliability, I’ve found it to be pretty consistent. If you’re looking for something with great security but without the headache of extra hardware, it’s worth checking out. And for those looking to step up their game, I’d also suggest looking into 4G proxies for added privacy and security.