Securing SonicWall Firewall with RADIUS and Push MFA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2022 12:28 PM - edited 03-24-2022 12:54 PM
Some things are too cool not to share. I've recently published articles about how to authenticate into network hardware using RADIUS + TOTP multi-factor authentication (MFA). It works by appending a code to your password after comma, i.e., "Password,12345." This method of authentication is best used on private networks or over a VPN, along with monitoring. The advantage is not having to share and manage a single set of local credentials, which is important if someone leaves the IT department. This configuration is now even easier with the inclusion of Push MFA, which eliminates the step of typing the extra code.
Combining RADIUS with MFA with previously only possible using EAP/TLS, which transmits passwords over cleartext. You'll soon be able to opt for CHAP/CHAP2, which is somewhat more secure given the shared secret is always encrypted. This video is an overview of work that I did with an AWS EC2 instance using a SonicWall NSv firewall. Please excuse the Philly accent.
This is the part that you won't see:
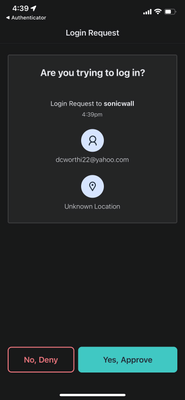
This type of MFA challenge is increasingly important given the high threat level.
- Labels:
-
General Networking

