User Verification Codes for MFA into LDAP Applications
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2022 06:34 PM
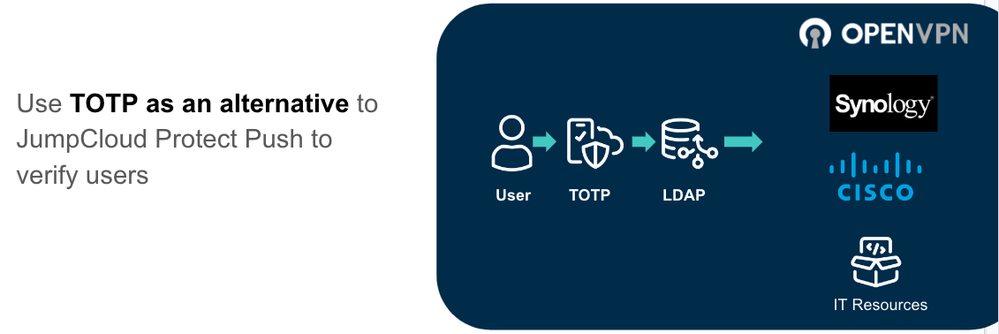
I'm happy to announce that we've added TOTP (Time-based One-Time Password) verification code support for Multi-factor Authentication (MFA) into LDAP.
As an alternative to using JumpCloud Protect, your users can now use TOTP verification codes in order to verify their identity when accessing your LDAP applications, such as OpenVPN, Synology, and many others.
How do users enter a TOTP verification code for MFA with these applications?
Your users can simply append their TOTP verification code in the password field and JumpCloud will verify the TOTP code.
Like this: <password> + <comma> + <OTP code>
Example: Nicepassword01!,123456
How do admins enable MFA for LDAP applications?
Follow our documentation here or take these simple steps:
- If you've already got your LDAP configuration setup in JumpCloud, then there is nothing in there that needs to change. If you are starting anew, then follow this guide, Using JumpCloud's LDAP-as-a-Service.
- Configure your client application(s) to our LDAP URL for MFA (vendor configuration varies):
ldap-mfa.jumpcloud.com - Create a Conditional Access Policy requiring specific user groups to MFA.
Note: If a user has both JC Protect and TOTP enabled, they can use either option. If they don't input a TOTP, JumpCloud will automatically send a Push notification to their phone. - Inform your users that it is available.
We think your users will enjoy having an alternative option for verifying their identity when accessing your VPNs, NAS, and other LDAP applications.