- JumpCloud Community
- IT Topics
- Best Practices
- Setting up SSO for AWS IAM or AWS Identity Center
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Setting up SSO for AWS IAM or AWS Identity Center
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2023 04:04 AM - edited 04-04-2024 08:41 PM
I know the subject of this post may seem confusing at first, but rest assured, you will leave with a clear understanding of these concepts (hopefully).
Keep calm and read on 😉
What are these terms?
First thing first - let's clarify AWS IAM and AWS Identity Center:
- AWS IAM - manage the permission and access for user / groups to AWS resources.
- AWS Identity Center - manage resources in a similar way as above; AND it can be your IdP to setup SSO(SAML, OIDC, API, & SCIM) for accessing other applications.
But wait, there's more:
- Both services supports login from external identity sources via SSO.
- Additionally, AWS Identity Center supports SCIM to sync identities from external identity sources.
Ok, let's dive into each one before things get messier, shall we?
Setup SSO for AWS IAM
Good for:
- You have more than 1 AWS accounts.
- Multiple teams require various different accesses to different AWS accounts and resources.
- A relatively small engineering team with not-too-crazy people movements - less than 100 ideally.
It looks like this conceptually:
Setting it up:
- Follow this KB to setup SSO connector.
- Now, we design and create the roles in AWS for reflecting the permissions you wanted to control:
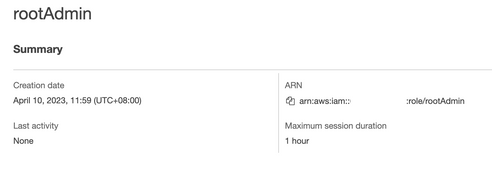
- i.e. I wanted to have an Admin role which has full access to all my AWS services and resources:
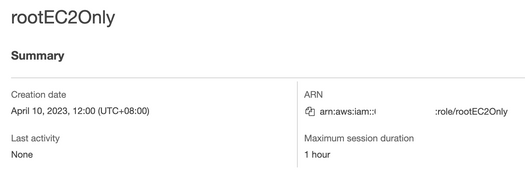
- And a role has access to EC2 only:
- Take note on the account name and ARN.
- Do the same with a different account name for the other AWS accounts.
- i.e. I wanted to have an Admin role which has full access to all my AWS services and resources:
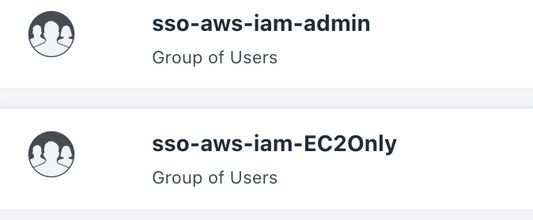
- Next, we "map" these roles in JC, as user groups, and bind the SSO connector to the groups too:
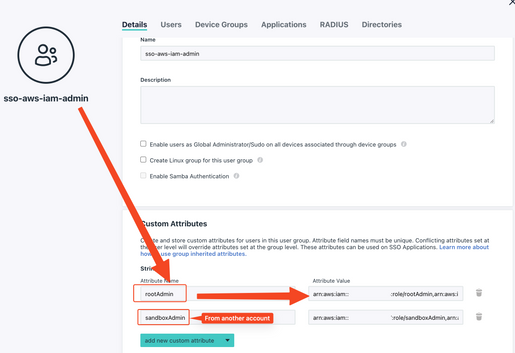
- Link the groups with the roles we created in AWS - i.e. for the admins on different accounts:
the attribute value looks like this:
arn:aws:iam::YOUR_AWS_ACCOUNT_NUMBER:role/ROLE_NAME,arn:aws:iam::YOUR_AWS_ACCOUNT_NUMBER:saml-provider/JumpCloud.
Then, update the SSO connector you created initially, with these role names:
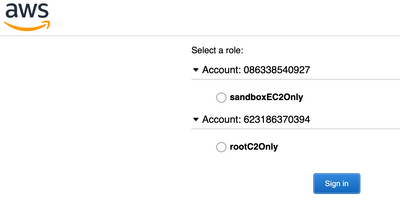
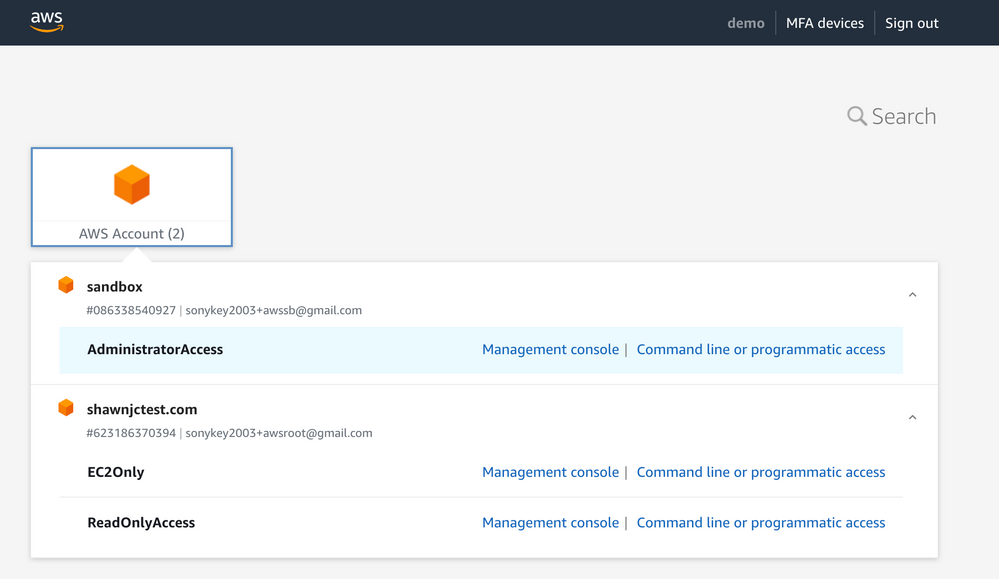
- Lastly, add the users to the groups you created respectively, it looks like this when users login:
The downside:
- You will have to create new roles in AWS and map it with new user groups in JC every time there are additional new permissions to handle.
- Delicate design and clear documentation are required - for maintaining and day-to-day operations.
How to address these ^ on a scale? Read on please.
Setup SSO for AWS Identity Center
Good for:
- You have more a ton of AWS accounts.
- Scattered and distributed engineering team across different geo locations and timezones, require various different accesses to different AWS accounts and resources.
- Large engineering team in general - typically more than 100 people.
It looks like this conceptually:
Setting it up:
- Follow the KB here.
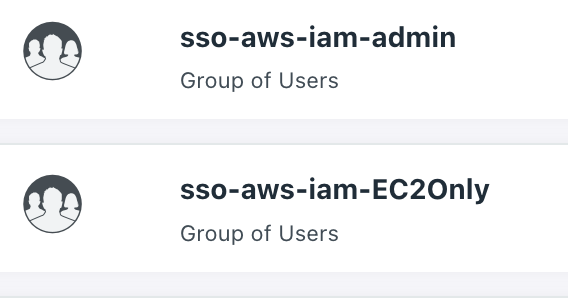
- Once the SCIM is up, similarly design the groups with different permission projections in JC, and bind the SSO connector to these groups:
- Bind the users respectively to these groups.
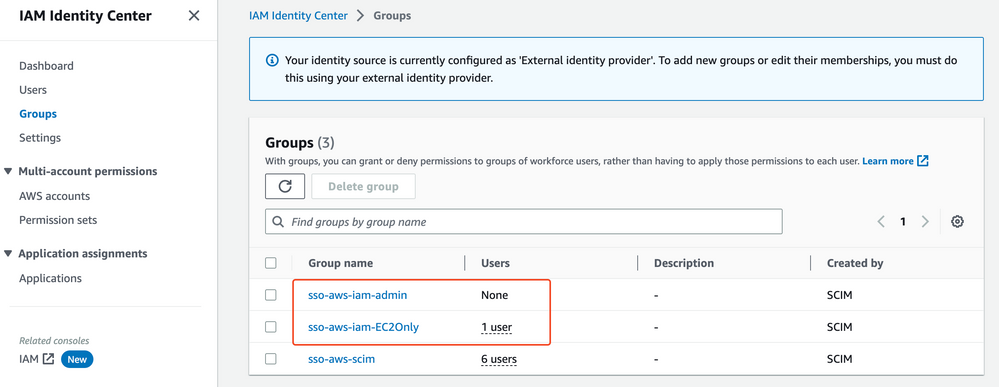
- Now go to AWS Identity center, these groups and users will be created accordingly via SCIM:
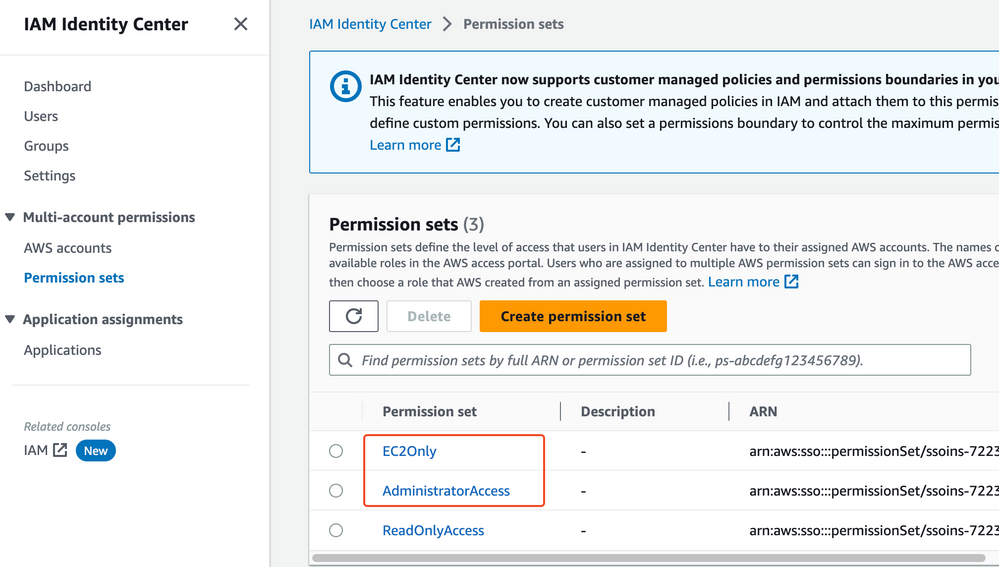
- Then, create the permission sets to define the boundaries of the permissions to your AWS resources:
- Assign the groups to respective AWS accounts - with the desired permission sets:
- Lastly, user from the JC groups login looks like this:
The downside:
- You will need to get familiar with how AWS identity center works.
- Keep monitoring the SCIM provisioning status between JC and AWS - if the account is not provisioned in Identity Center, user wont be able to login.
- Permission sets need deep understanding and delicate designs to avoid potential conflicts, or permission loopholes.
- Still have to assign the groups with permission sets for each account you have.
Alright, that's it! I hope you have gained a clear understanding by reading this far. That's right; these are not black & white options to choose from. Both carry pros & cons and are suitable for different environments.
Happy designing, folks!
New to the site? Take a look at these additional resources:
Ready to join us? You can register here.