RDP to EC2 instances via JumpCloud SSO
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2023 11:15 PM
Hi Folks,
I hope you all had a fantastic summer break and are fully recharged for Q4 2023!
It's Friday again, and what better time to share the joy of a cool AWS project with JC?
Let's take a revisit of setting up SSO for AWS IAM Identity Center. Once you've got that up and running, you're actually just a few steps away from extending this SSO functionality to RDP for a Windows instance.
Time to dive in!
Prerequisites
- Setup SSO for AWS IAM Identity Center if you haven’t done so yet.
- Enable AWS Systems Manager Fleet Manager.
Setting It Up
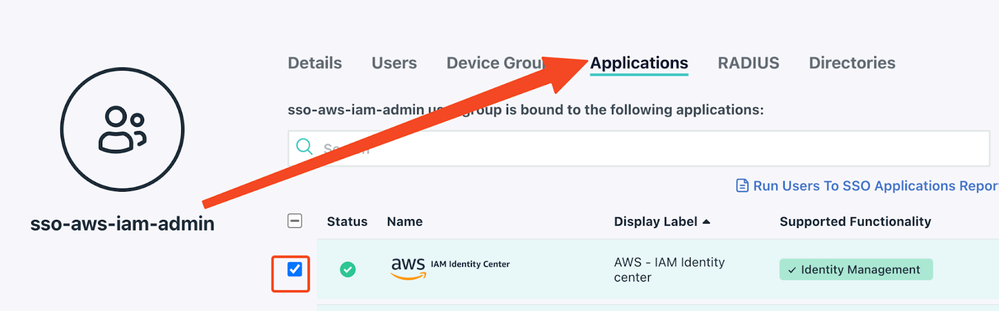
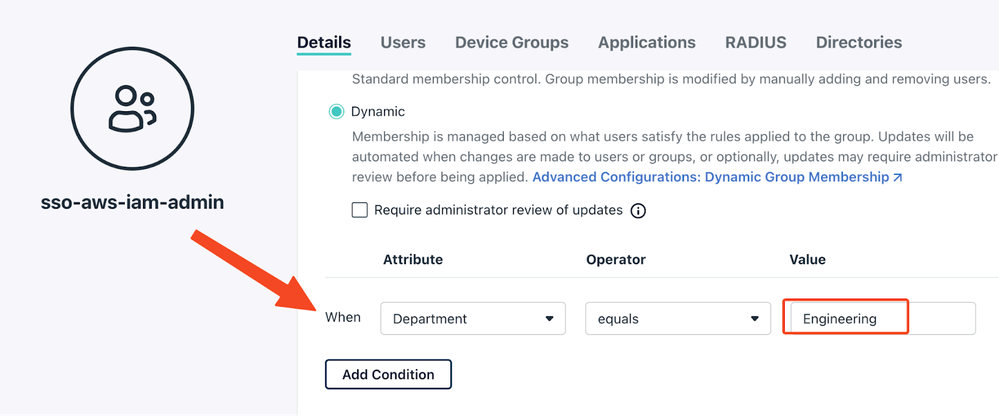
- Create a user group in JC and bind to the AWS SSO you created.
- Recommend setting this group up for dynamic membership.
- The group and users will be provisioned to AWS IAM Identity Center thanks to the SCIM integration we setup alongside with the SSO.
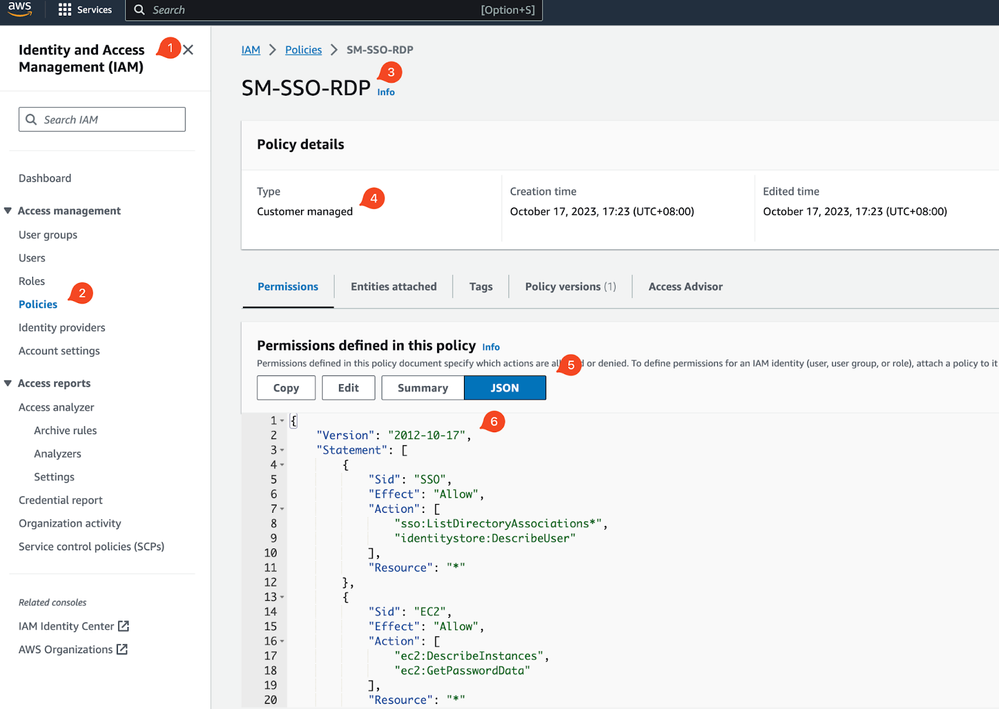
- On AWS, go to IAM (not IAM Identity Center), create a customer managed policy - you can copy over the template here.
- Then, follow the steps here (starting from: “To assign your AWS IAM Identity Center group”) to assign the policy to the permission set -> group -> sub accounts.
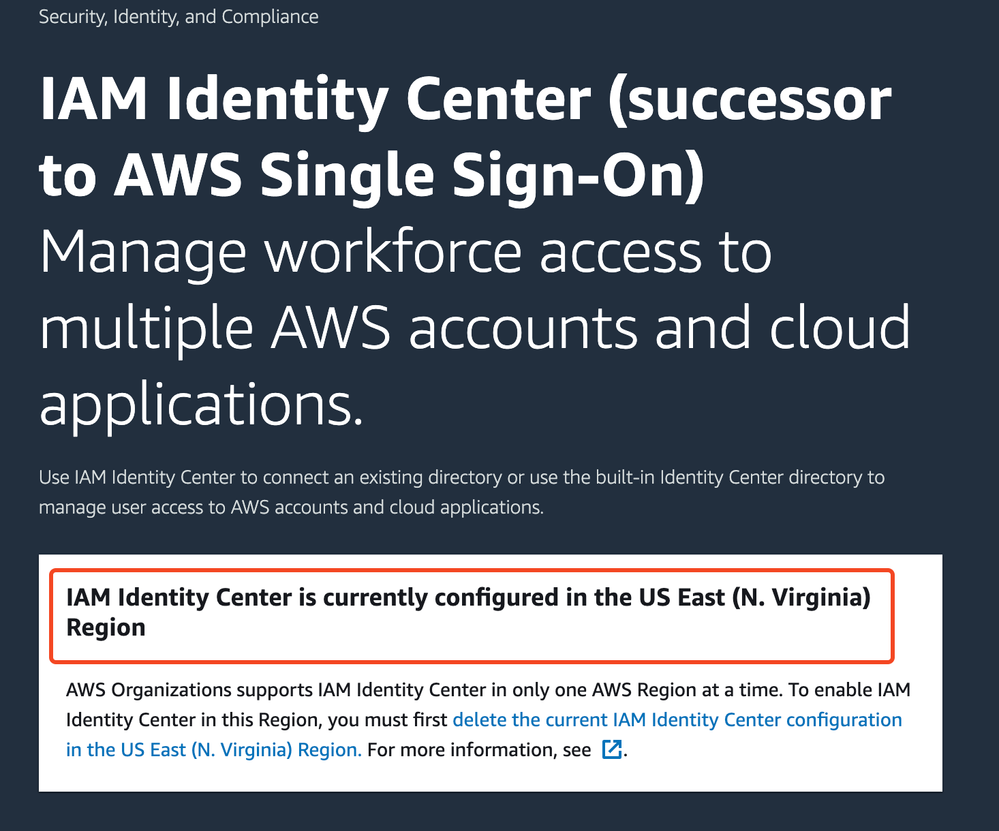
- Now, create the instances in the same region as your IAM Identity Center - you will get a banner when accessing the Identity Center not in its origin.
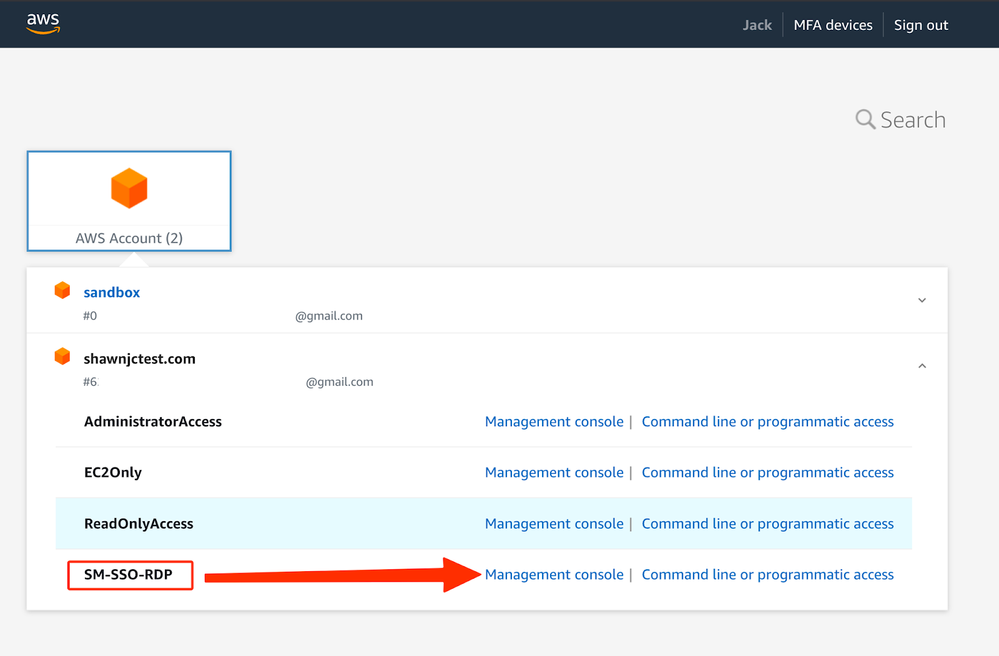
- Login to your JC user portal and jump over to AWS:
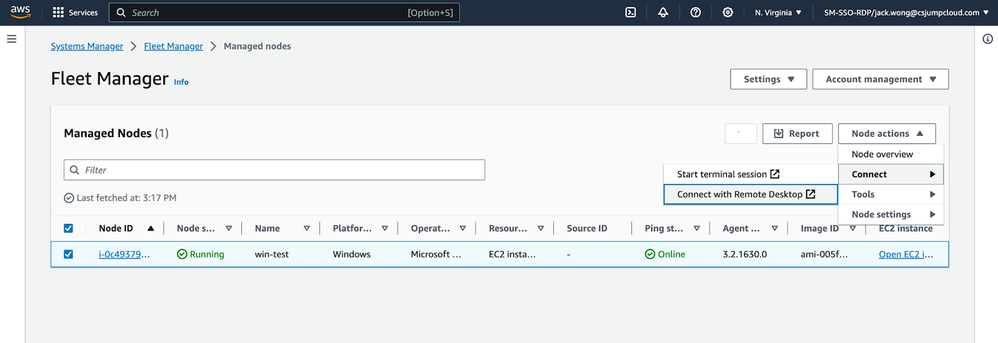
- Go to Systems Manager -> Fleet manager, select the instance you wanted to access.
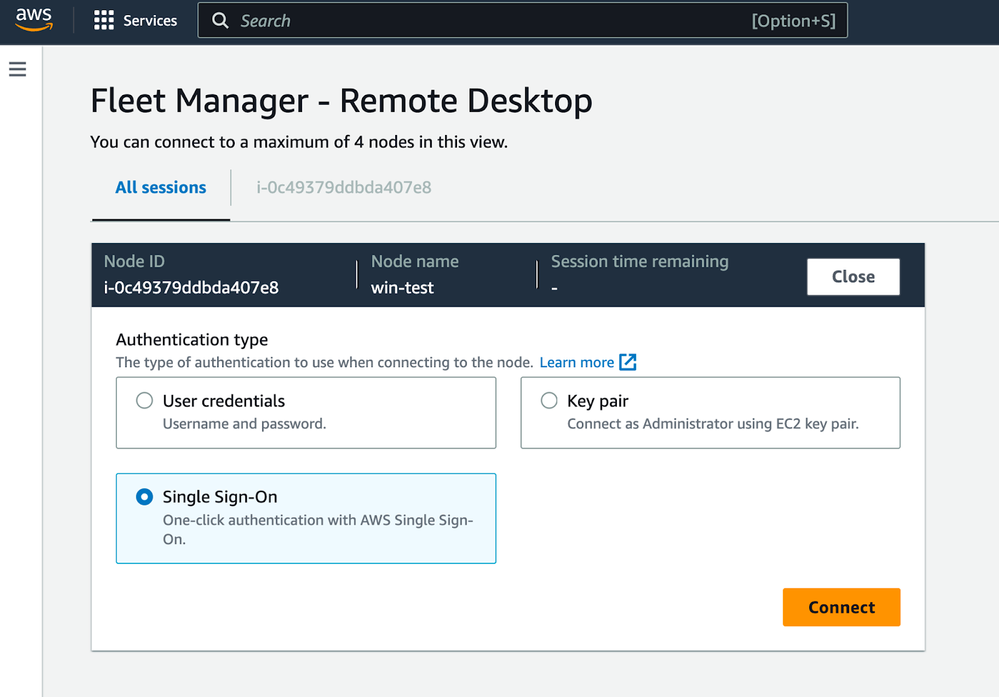
- Select SSO:
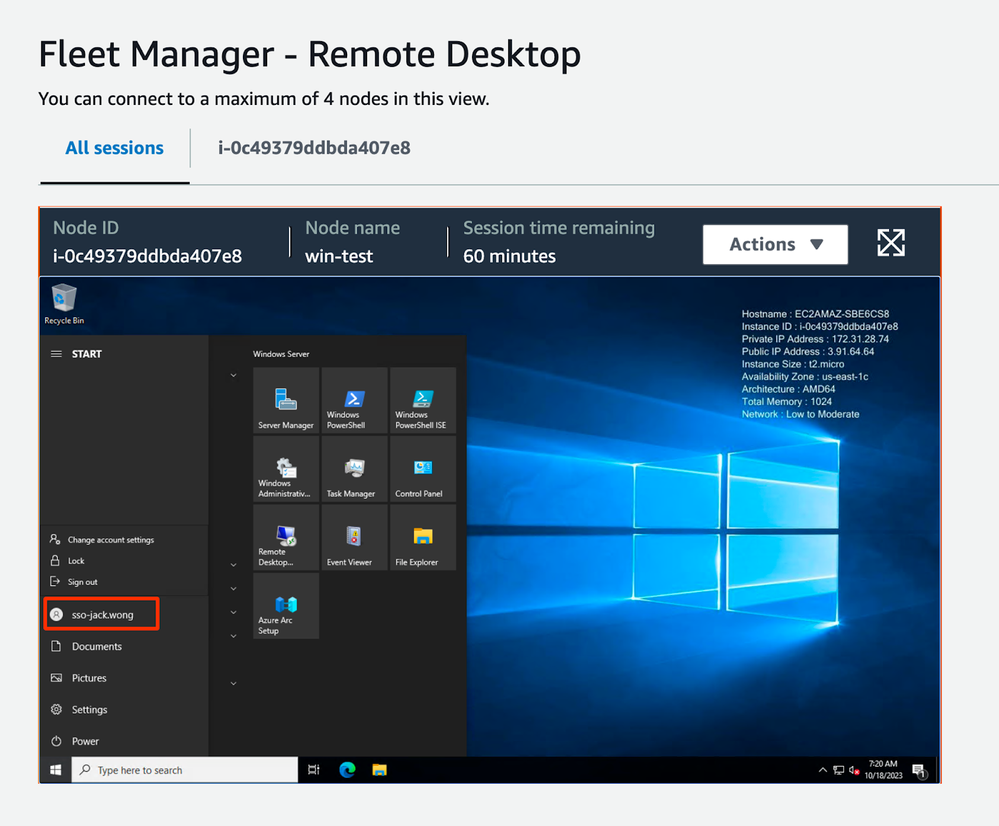
Tada! This is the user created on the spot by AWS according to your JC user! (The RDP session is embedded in my Chrome tab, which is very nice.)
Benefits
- You can consider securing the windows server access with JC SSO and MFA on top with JC’s conditional access policy.
- Automated user/group provisioning from JC to AWS via Dynamic Groups.
- Audit log tracks for such activity in JC’s Directory Insights.
That’s it! Hope you enjoy it, and thanks for reading this far.
Happy Friday folks, catch you up on the next one!
0 REPLIES 0