Reimagine OS Provisioning with Dynamic Groups
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2023 05:20 AM - edited 09-11-2023 08:19 PM
Hi Folks,
It’s been a while (again lol) since last time I posted - I took a beautiful trip to Perth with my family (a long overdue holiday!), followed by a business trip to vibrant / lively Jakarta. Time to “settle down” my thoughts a bit, and embrace the coming game charge feature - yep, dynamic groups, for users & devices!
Dynamic groups, especially for the devices, is by far the most anticipated feature I ever had back in my days as a JC customer - it will make my automation workflows (easily) 100 times easier!
(I will do a user group focused post soon after)!
Let’s dive into it!
First of all, why does device group matter?
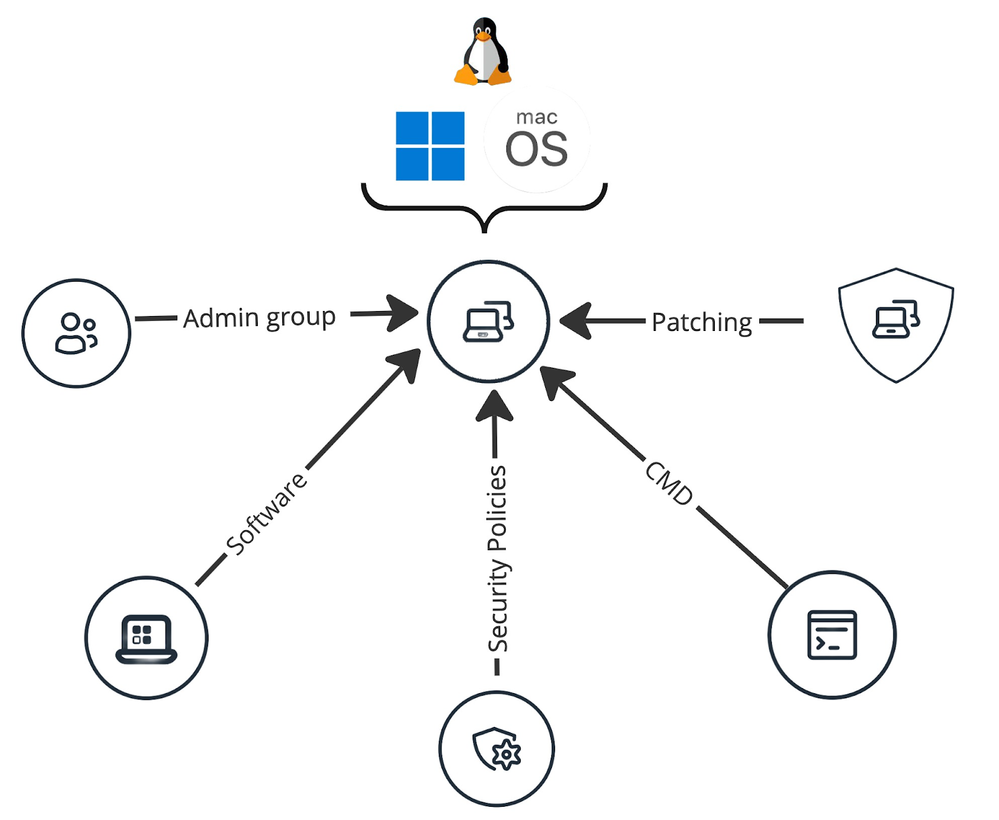
Well, it’s a scalable container in JC to link a device to resources, visually it looks like this:
As portrayed in the diagram, everything will automatically fall into place once the device is added to the group!
So, let’s take a moment to imagine that - you have shipped a vanilla OS to the user straight, and then the following matters will get taken care of:
- Systems configurations;
- Patches;
- App deployments;
- And, most importantly, hardening and compliance.
All of these are achieved with zero-touch!
By now, you should share my excitement. Let's proceed to set this up right away.
Setting things up
[Update - 12th Sep 2023] - Now you can configure the dynamic device group on UI, and of course the API approach described below is also available to provide complementary fine-grained operators.
Creating a fresh new device group member automation enabled
# Here is an example to create a group will automatically add Windows devices as the members.
# Constructing auth header
$headers = @{
"x-org-id" = $org_id #your org id
"x-api-key" = $apiKey #your admin api key
"content-type" = "application/json"
}
$osFamily = "Windows" # It can be darwin for MacOS, Linux, and any other OSes JumpCloud supports.
$groupName = "Demo_DynamicGroup_Windows"
# Request body to filter the device OS by Windows
$body = @{
"name" = $groupName
"membershipMethod" = "DYNAMIC_AUTOMATED"
"memberQuery" = @{
"queryType" = "FilterQuery"
"filters" = @(
@{
"field" = "osFamily"
"operator" = "in"
"value" = $OSFamily
}
)
}
"memberQueryExemptions" = @()
}
$request = Invoke-RestMethod 'https://console.jumpcloud.com/api/v2/systemgroups/' -Method 'POST' -Headers $headers -Body $body
$request | ConvertTo-Json
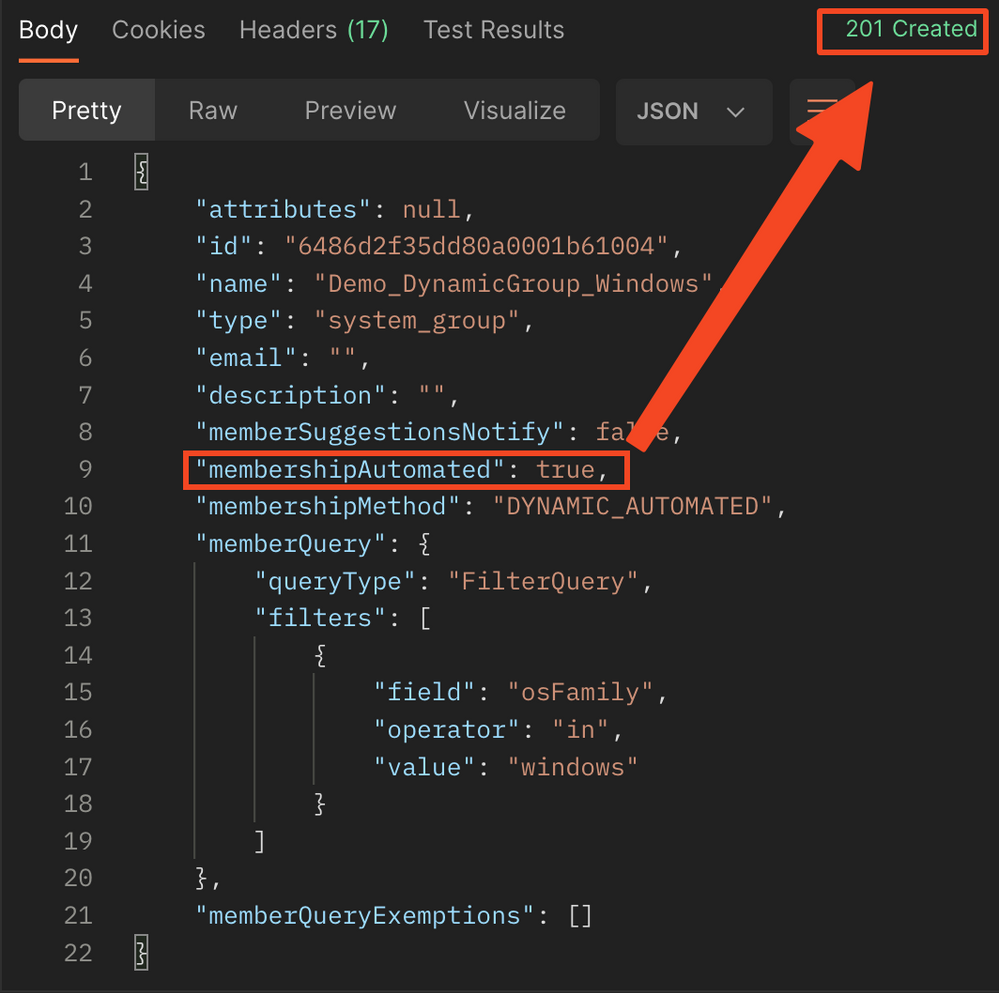
A success output looks like this:
Enabling device group member automation on existing group
# Here is an example enabling device group member automation on an existing group
# Constructing auth header
$headers = @{
"x-org-id" = $org_id #your org id
"x-api-key" = $apiKey #your admin api key
"content-type" = "application/json"
}
$osFamily = "Windows" # It can be darwin for MacOS, Linux, and any other OSes JumpCloud supports.
$groupID = "Group_GUID" # You can get the group ID via pwsh cmdlet Get-JCGroup -Type System -Name "your_group_name"
# Request body to filter the device OS by Windows
$body = @{
"name" = $groupName
"membershipMethod" = "DYNAMIC_AUTOMATED"
"memberQuery" = @{
"queryType" = "FilterQuery"
"filters" = @(
@{
"field" = "osFamily"
"operator" = "in"
"value" = $OSFamily
}
)
}
"memberQueryExemptions" = @()
}
$request = Invoke-RestMethod "https://console.jumpcloud.com/api/v2/systemgroups/$groupI" -Method "PUT" -Headers $headers -Body $body
$request | ConvertTo-Json
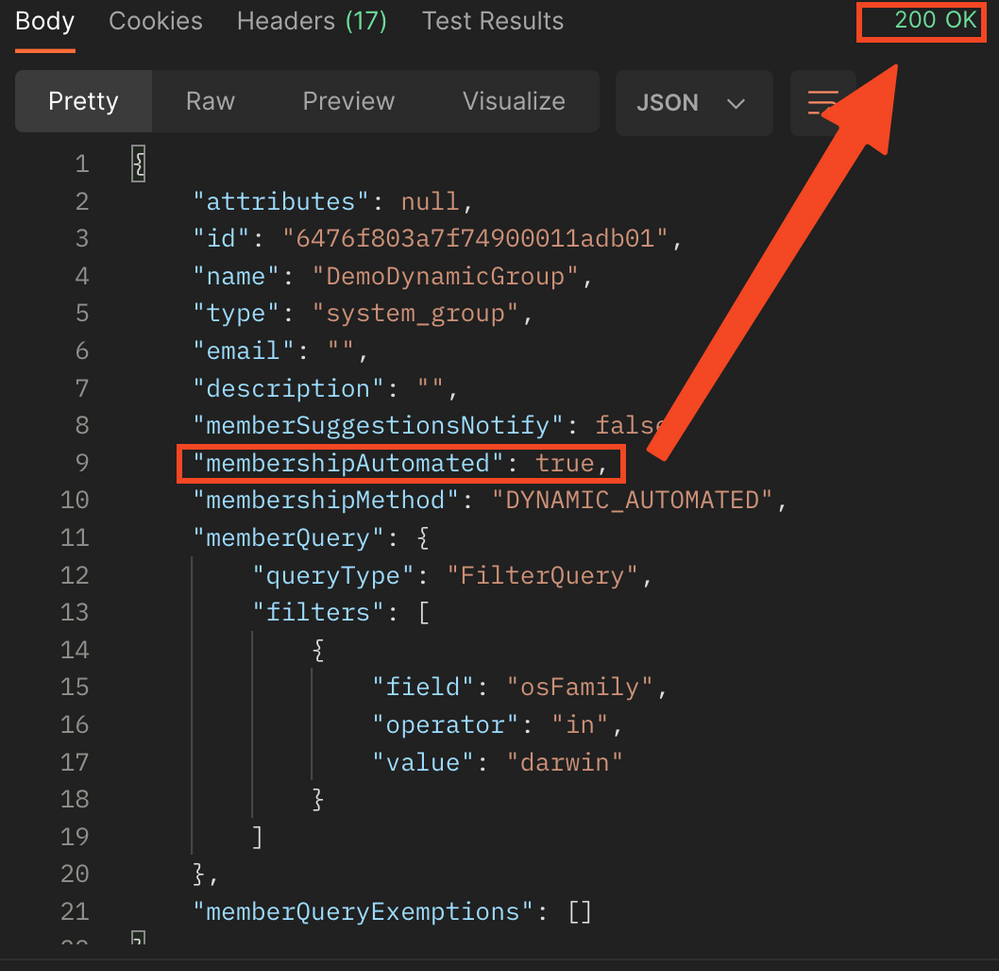
And the output should looks like this:
All set!
Now, attach the security/patch/software policies, hardening cmds (you may take a look at @JuergenKlaassen 's recent post on this very topic), and bind the global admin user group (if any) to it. - your scalable container just transitioned to an automated security fortress!
What’s Next
In a real life scenario, where the devices get shipped to the end user directly from the factories or resellers, and you (as an IT admin) has created the user account in JC:
For MacOS
- User opens the box for the 1st time ->
- Apple ADE kicks in ->
- User authenticate with their JC credential ->
- device enrolled and MDMed ->
- automatically added into “MacOS Device Group” ->
- 10~15 mins later, hardened and configured, boom!
For Windows
- User opens the box for the 1st time ->
- Login to JumpCloud user console ->
- Enrol the device via Windows MDM ->
- Device enrolled and MDMed ->
- Automatically added into “Windows Device Group” ->
- 10~15 mins later, hardened and configured, boom!
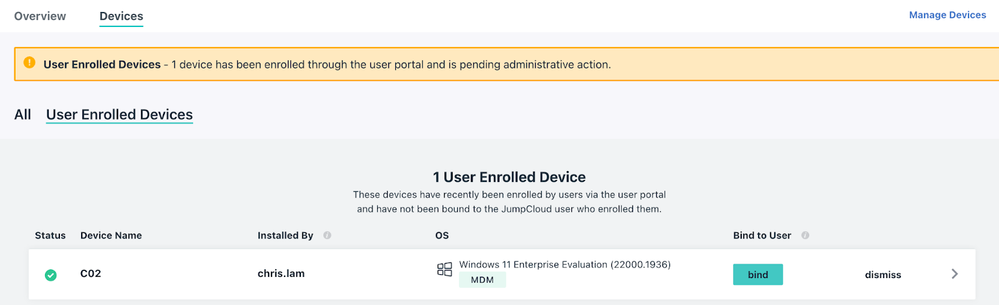
*P.S. Admin will receive a banner on the console to bind the user to the MDMed windows device, verify and bind the user to it.
Done!
Hopefully this feature will ease into your onboarding process, with a breeze. 😉
Thanks for reading this far, have a great start of the week.