Integrating Linux devices with JumpCloud LDAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2023 06:40 AM - edited 09-08-2023 03:44 AM
Hi Folks,
I hope you've all had an unforgettable summer holiday, taking the time to disconnect and create special memories with your loved ones.
Sooooo, I've stumbled upon something (thanks @james_herbert & Rickie 😉) that potentially could be a significant game charger for integrating Linux devices (servers) with JC. Before JC caught up with Linux’s myriad of distros for deploying the agents, I’ve discovered a mid-ground - using the JC user account to login via LDAP!
Try picture this: you effortlessly push out configuration settings to your Linux servers using popular automation tools like Ansible, Chef, or Puppet. All the while, secure the login by JC (via LDAP) —no agent required.
Let’s dive into it.
[Updated - 8th Sep 2023]
Systems Tested & Works
Ubuntu 22.04.2 LTS - Jammy
Oracle Linux 9.2 (Fedora 34)
Requirements
- Install SSSD - here is the example on Ubuntu & Oracle Linux:
sudo apt install sssd-ldap ldap-utils # Ubuntu #Or yum install sssd sssd-client # for Oracle Linux - SSSD should work on most of the Linux distros.
- Configured JC LDAP. - Most importantly, creating a Bind DN service account.
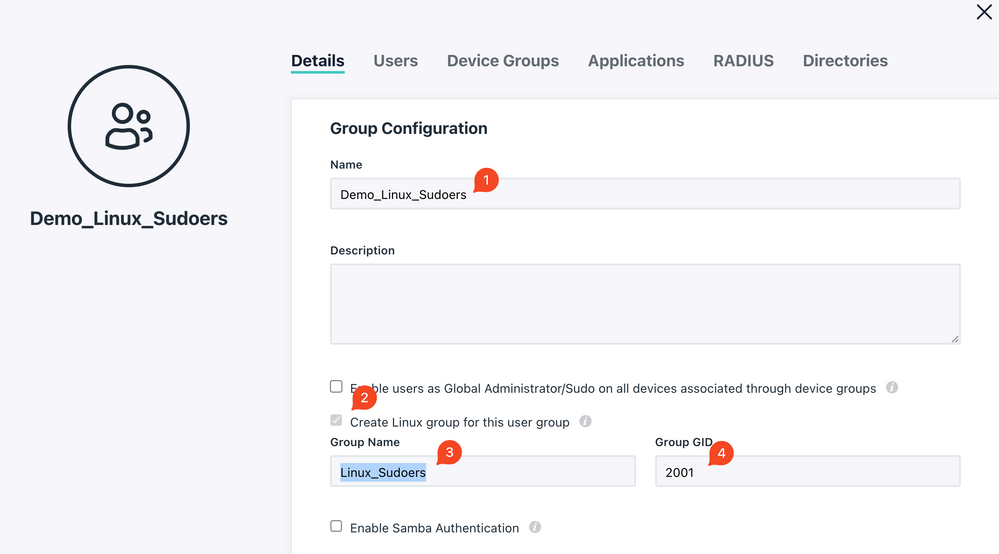
[Updated on 4th Sep 2023] - Added sudoer group & SSH keys support
- Create the Sudoer user group in JC with Linux GID "2001"
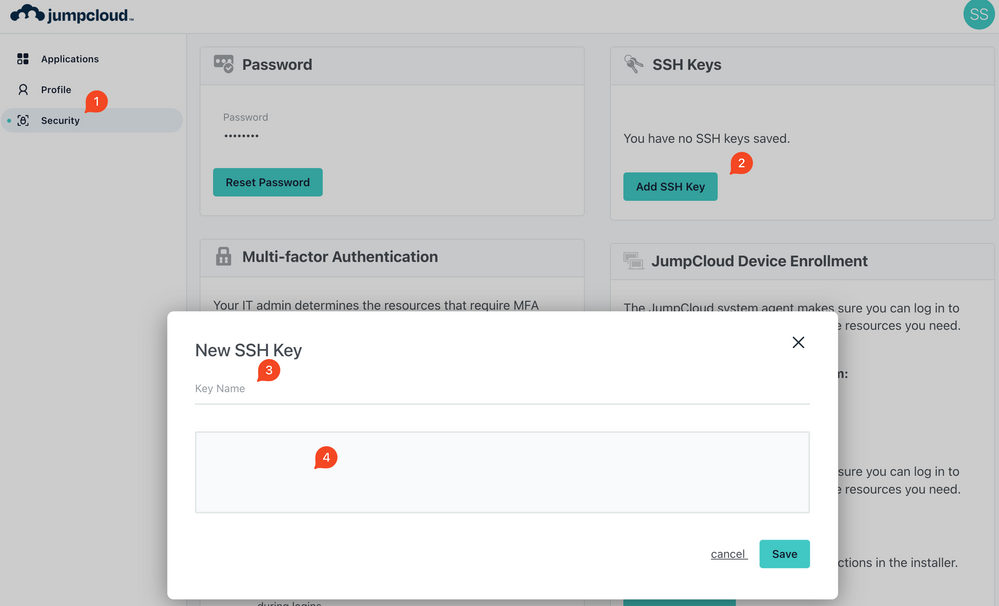
- Add the SSH public key to user's account via their user portal.
Setting It Up
- (For Oracle Linux) Download JumpCloud's LDAP server cert:
echo -n | openssl s_client -connect ldap.jumpcloud.com:636 -showcerts | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > /etc/openldap/certs/jumpcloud.chain.pem - Create the /etc/sssd/sssd.conf. Here is an example:
[sssd] config_file_version = 2 services = nss,pam,ssh domains = jumpcloud [nss] [pam] [domain/jumpcloud] debug_level = 2 id_provider = ldap enumerate=true auth_provider=ldap ldap_uri = ldaps://ldap.jumpcloud.com:636 #ldap_uri = ldaps://ldap-mfa.jumpcloud.com:636 #MFA for JC LDAP ldap_search_base = o=YOUR_ORG_ID,dc=jumpcloud,dc=com ldap_default_bind_dn = uid=YOUR_LDAP_BIND_USER,ou=Users,o=YOUR_ORG_ID,dc=jumpcloud,dc=com ldap_default_authtok = YOUR_LDAP_BIND_USER_PASSWORD ldap_user_ssh_public_key = sshKey ldap_use_tokengroups = False ldap_tls_cacert = /etc/ssl/certs/ca-certificates.crt #ldap_tls_cacert = /etc/openldap/certs/jumpcloud.chain.pem # Oracle Linux only sudo_provider = none
- Here are the caveats from the ^ conf:
- Ldap_uri - Consider using ldaps://ldap-mfa.jumpcloud.com:636 for protecting ldap login with MFA.
- (Optional) ldap_access_filter - you can narrow down the scope to a specific group of users by adding a line like this:
ldap_access_filter = memberOf=cn=YOUR_GROUP_NAME,ou=Users,o=YOUR_ORG_ID,dc=jumpcloud,dc=com
- Update /etc/ssh/sshd_config with lines:
#Enabling PAM UsePAM yes #Disable Root Login PermitRootLogin no #Disable Password Login (enforce using SSH key) PasswordAuthentication no #Directing sshd to use SSSD as the authorized_keys AuthorizedKeysCommand /usr/bin/sss_ssh_authorizedkeys AuthorizedKeysCommandUser root - Update /etc/pam.d/sshd for automatically creating the home directory when a user logged in via JC LDAP
session required pam_mkhomedir.so skel=/etc/skel/ - Create /etc/sudoers.d/10-jumpcloud to grant the root permission to the group we created in JC:
%Linux_Sudoers ALL=(ALL) ALL #Use the linux group name, NOT the JC group name - Update the permission for sssd.conf and start the SSSD service:
sudo chmod 600 /etc/sssd/sssd.conf # authconfig --update --enablesssd --enablesssdauth # For Oracle Linux only sudo systemctl enable sssd sudo systemctl start sssd sudo systemctl restart sshd
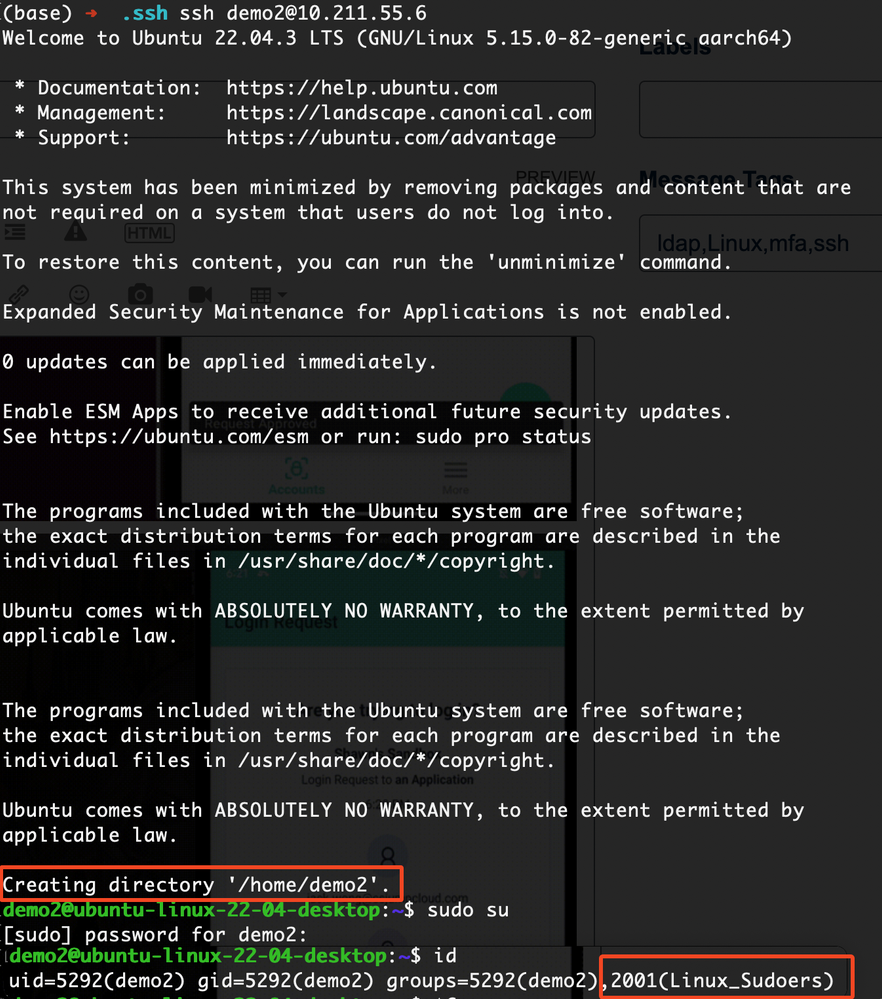
- Validate the login - you should see the home directory been created and you are in the sudoers' group:
- Done! By putting it together, this is how it looks like (with MFA enabled!):
Thanks for reading! Let me know your thoughts in the comments below.