- JumpCloud Community
- IT Topics
- Software & Hardware
- Re: Mabl & JumpCloud SSO - Custom SAML App Setup G...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Mabl & JumpCloud SSO - Custom SAML App Setup Guide
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2022 06:45 PM - edited 06-28-2022 06:52 PM
Configuring a Custom SAML App for JumpCloud SSO with Mabl
We recently added Mabl to our suite of Engineering Tools and wanted to get it configured to work with JumpCloud SSO. The Mabl support team we were working with did not have experience in using JumpCloud as an SSO provider so the best they could do was offer us their instructions for setting it up with Okta and then we went through a series of trial/failure troubleshooting steps until we found the configuration that worked successfully. I wanted to create this quick guide in case anyone else is faced with this scenario so that you will have a more seamless experience in getting it set up the first time.
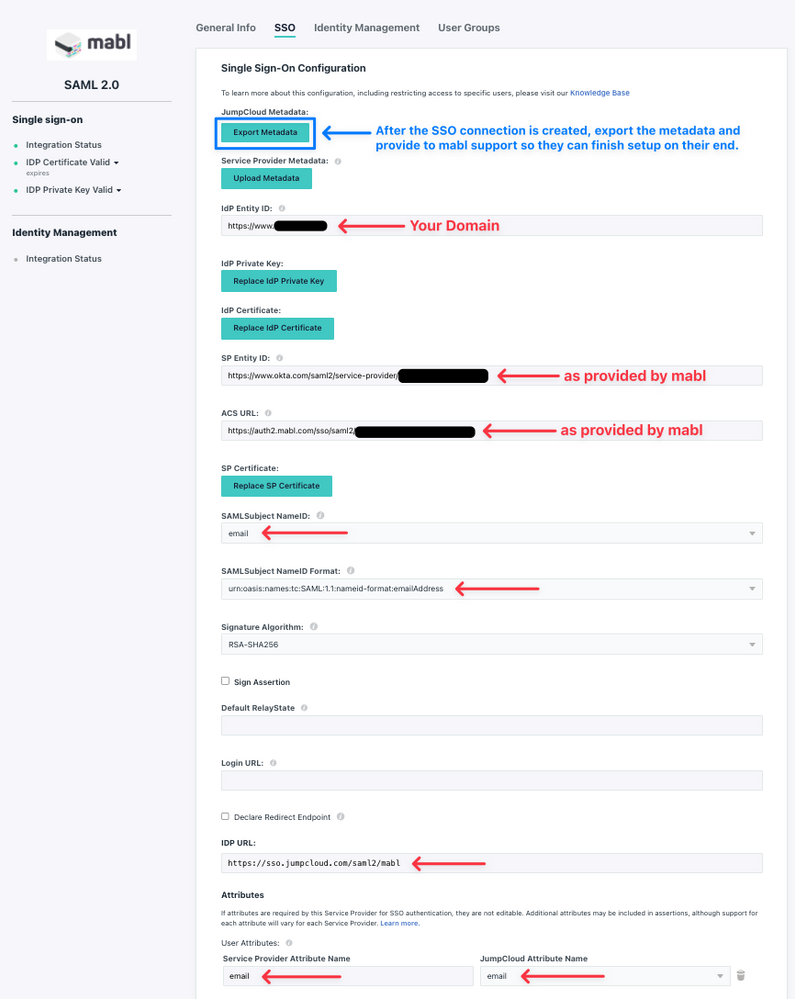
When setting this up, you will need to reach out to Mabl Support or your Mabl CSM and they will provide you with the following information which will roughly look like this (actual URLs will be specific to your account):
- audience_uri: https://www.okta.com/saml2/service-provider/####################
- reply_url: https://auth2.mabl.com/sso/saml2/$$$$$$$$$$$$$$$$$$$$
In JumpCloud SAML 2.0 terminology these values are mapped accordingly:
- audience_uri (from Mabl) = SP Entity ID (in JumpCloud)
- reply_url (from Mabl) = ACS URL (in JumpCloud)
You now have the necessary info to create the SAML 2.0 Custom Connector within JumpCloud. When doing so, here is all the information that you will need.
General Info
- Display Label: Mabl (or your chosen name)
- Description: (optional)
- Logo: (optional) If you want to use a Mabl Logo you can use this one or find another online.
SSO Info
- IdP Entity ID: https://www.domainname.com (use your organization's domain)
- SP Entity ID: https://www.okta.com/saml2/service-provider/#################### (as provided by Mabl)
- ACS URL: https://auth2.mabl.com/sso/saml2/$$$$$$$$$$$$$$$$$$$$ (as provided by Mabl)
- SAMLSubject NameID: email
- SAMLSubject NameID Format: urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress (select from drop-down)
- IDP URL: https://sso.jumpcloud.com/saml2/mabl (or whatever you want to name it after /saml2/)
- Create a Custom User Attribute with the following values:
Service Provider Attribute Name: email
JumpCloud Attribute Name: email
Save the connection and then download/export the metadata XML file as you will need to provide this to Mabl support so that they can finish the configuration on their side of things. If necessary, you should create the appropriate JumpCloud User Group that this SSO Connector will be bound to or, if appropriate, bind it to an existing group. I would suggest not adding any users at this point as you will want to test and verify the connection before performing a full rollout. Once you are ready, send the exported SSO metadata file to Mabl support so they can finish setup on their side of things.
It is likely they will have also asked if you would like any domains to be locked to your account for SSO purposes. Obviously, do what makes sense for your organization, but it is likely that you will want your primary domain to be locked so that it forces the use of SSO. If this is desired, provide the appropriate domain name(s) to them.
Once Mabl support has everything set up on their end they will let you know and ask that you test the connection. Add a test user to the previously created or designated JumpCloud User Group and then have that user attempt to launch Mabl from the JumpCloud User Console.
If successful, it will do one of the following:
- If the test user already had a Mabl account setup within your organization, it should log them in and take them to your company's workspace if they were already a member of it.
- If the test user did not already have a Mabl account, it will create a new account for them and sign them into their own personal workspace. They will then need to be invited to your company workspace.
If unsuccessful, you will likely get an error indicating that the connection was unsuccessful. Should this happen, you will need to work with Mabl support to troubleshoot.
Once you have confirmed that it is working, you should be all set for existing Mabl users. If this is a new installation or when providing access to new employees you will need to add them to the JumpCloud User Group that is bound to the Mabl SSO connector and also invite them to your workspace within Mabl.
- If they accept the Mabl invite before authenticating to Mabl via JumpCloud, they will be prompted to enter their name and then can sign in with the SSO option to create their account and have it automatically added to your Mabl workspace.
- If they authenticate to Mabl via JumpCloud prior to accepting the invite, it will create a Mabl trial account and sign them into their personal workspace. They can then click through the invite to have their account added to your organization's workspace.
For reference, here are our working connection settings:
- Labels:
-
General Software
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2022 10:00 AM
This will make a great knowledge base article!
New to the site? Take a look at these additional resources:
Ready to join us? You can register here.
- Block Apple ID and Internet Accounts on macOS and iOS devices in Software & Hardware
- Build a Custom HRIS Integration With GoogleSheet in Best Practices
- JumpCloud Go - A Progressive Onboarding Guide in Best Practices
- Tailscale SSO OIDC in Security & Networks
- Reimagine Employee Onboarding with Dynamic Groups in Best Practices